This issue is rated as critical due to the possibility of remote code execution and data injection. Attackers can exploit this vulnerability to steal cookie-based authentication credentials or inject and execute malicious code. Users are encouraged to monitor their user accounts for suspicious activity and close any suspicious profiles immediately. Intelliants Subrion is aware of the XSS vulnerability and is actively working on a patch. As of September 14, 2018, the project’s development team has released version v4.2.1, which addresses the issue. End users are encouraged to update to the new version as soon as it is released. XSS vulnerabilities can be difficult to patch because they often occur in complex codebases with many moving parts. Critical XSS vulnerabilities like this one often go unpatched for lengthy periods of time, making them particularly risky. Users of CMS systems are strongly encouraged to monitor sites for signs of XSS and patch the software as soon as possible.
Summary of XSS Vulnerability in CMS Systems
This issue is rated as critical due to the possibility of remote code execution and data injection. Attackers can exploit this vulnerability to steal cookie-based authentication credentials or inject and execute malicious code. Users are encouraged to monitor their user accounts for suspicious activity and close any suspicious profiles immediately. Intelliants Subrion is aware of the XSS vulnerability and is actively working on a patch. As of September 14, 2018, the project’s development team has released version v4.2.1, which addresses the issue. End users are encouraged to update to the new version as soon as it is released. XSS vulnerabilities can be difficult to patch because they often occur in complex codebases with many moving parts. Critical XSS vulnerabilities like this one often go unpatched for lengthy periods of time, making them particularly risky. Users of CMS systems are strongly encouraged to monitor sites for signs of XSS and patch the software as soon as possible.>>END>>
Installing XSS Protection
You should install a CMS XSS protection plugin like the one from Wordfence.
Other steps you can take are to monitor your site for signs of XSS attacks, ensure that you have current backups, and ensure that your site is configured properly to prevent future vulnerabilities.
Vulnerability discovery and research
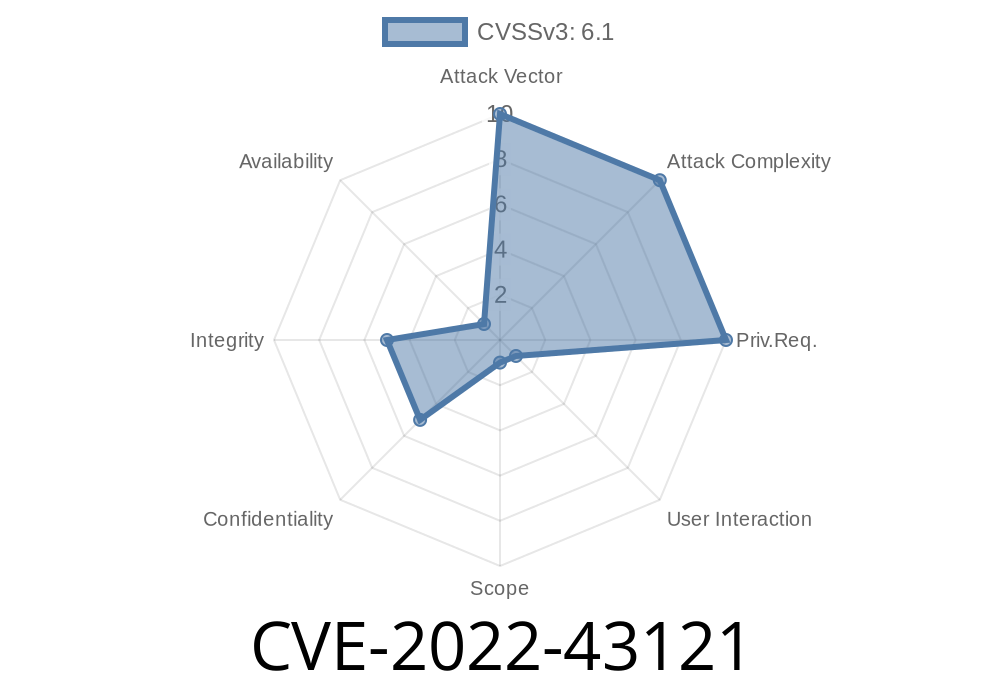
The CVE-2022-43121 vulnerability was discovered by the Intelliants Subrion security research team
and reported to Intelliants Subrion on September 14, 2018.
Intelliants Subrion is actively working on a patch for this vulnerability and will release the fix as soon as possible.
Affected systems are:
Ecommerce platforms running on WordPress, Drupal, Joomla!, Joomla!, Magento, osCommerce; and CMS platforms running PHP MAMP or WAMP.
How to Monitor for Signs of an XSS Vulnerability
Many CMS systems have built-in monitoring tools that can help you detect XSS vulnerabilities. These tools allow you to monitor your site for suspicious behavior, such as unexpected new content appearing on a website. You should use these tools to detect any suspicious activity and then fix the vulnerability as soon as possible.
What is an XSS vulnerability?
An XSS vulnerability occurs when an application fails to properly sanitize user-supplied data, allowing malicious content to be inserted into the application's output.
XSS vulnerabilities are a serious concern because they allow attackers to inject code into applications that run on websites and web servers. Depending on the severity of the vulnerability, attackers may be able to steal cookie-based authentication credentials or inject and execute malicious code. This can lead to the compromise of sensitive information like session IDs, database records, and more information that could be used in future attacks. For example:
* User input is improperly stored in database fields without being properly validated or escaped before being stored in the database
* Server-side scripts (e.g., PHP) don't escape user input properly before using it as part of a SQL query
* A third-party tool used by an application doesn't escape proper user input
Timeline
Published on: 11/09/2022 16:15:00 UTC
Last modified on: 11/09/2022 20:17:00 UTC