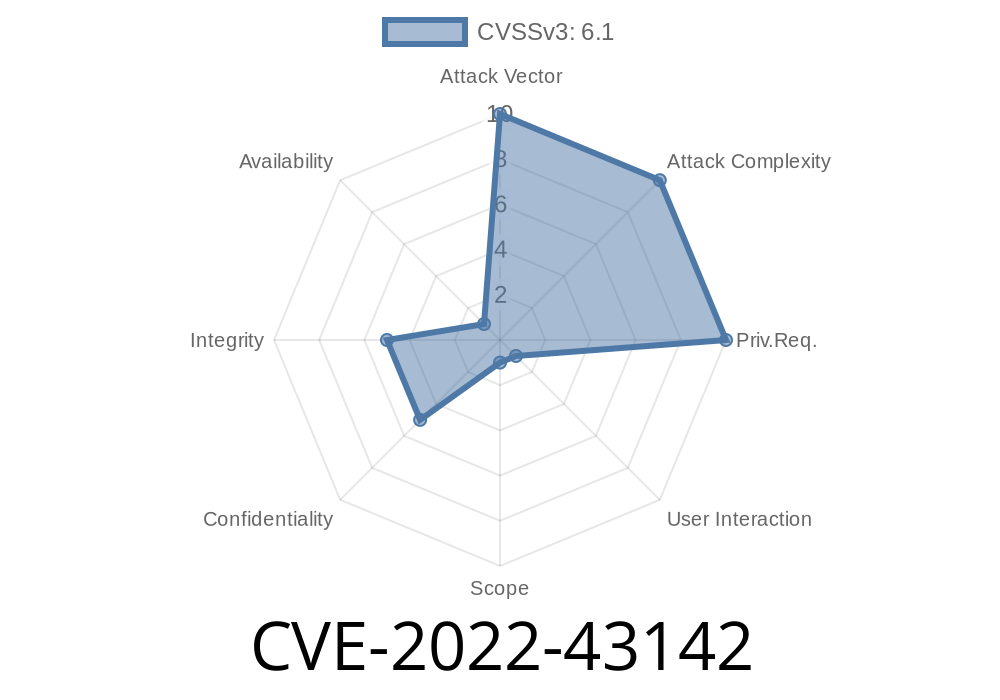
An attacker can inject malicious scripts to conduct session hijacking, data manipulation, or other attacks. In certain cases, XSS can be used to bypass certain security measures or prevent access to admin functions. Furthermore, if left un-checked, XSS could lead to a compromised user database. An attacker can inject malicious scripts to conduct session hijacking, data manipulation, or other attacks. In certain cases, XSS can be used to bypass certain security measures or prevent access to admin functions. Furthermore, if left un-checked, XSS could lead to a compromised user database. Add-fee.php is located on the application's private backend. In order to exploit XSS via add-fee.php, the targeted user must have a password that is stored in an encrypted format.
Summary
The XSS vulnerability on the add-fee.php URL allows an attacker to inject malicious scripts into the application's interface.
Add-fee.php is located on the application's private backend, meaning that an attacker needs to have a valid password to exploit this vulnerability.
Add-fee.php XSS Payload Input:
Timeline
Published on: 11/17/2022 19:15:00 UTC
Last modified on: 11/18/2022 18:24:00 UTC