Furthermore, arbitrary file deletion, posting, and modification are also possible due to insufficient input sanitization. Attackers can use this vulnerability to upload or delete the administrator’s system files, inject and execute malicious code, or even hijack the administration of a system. Canteen Management System is prone to an arbitrary file upload vulnerability due to the fact that it does not validate user input on the uploaded file’s file name. A person with a system security breach can, therefore, upload a malicious PHP script or any other type of arbitrary PHP code onto the server. Canteen Management System v1.0 is prone to an arbitrary file deletion vulnerability due to the fact that it does not sanitize the deletion of uploaded files before deletion. A person with a system security breach can, therefore, upload a malicious PHP script or any other type of arbitrary PHP code onto the server. Canteen Management System v1.0 is prone to an arbitrary file modification vulnerability due to the fact that it does not sanitize the modification of uploaded files before modification. A person with a system security breach can, therefore, upload a malicious PHP script or any other type of arbitrary PHP code onto the server. Canteen Management System v1.0 is prone to an arbitrary file posting vulnerability due to the fact that it does not sanitize the posting of uploaded files before posting
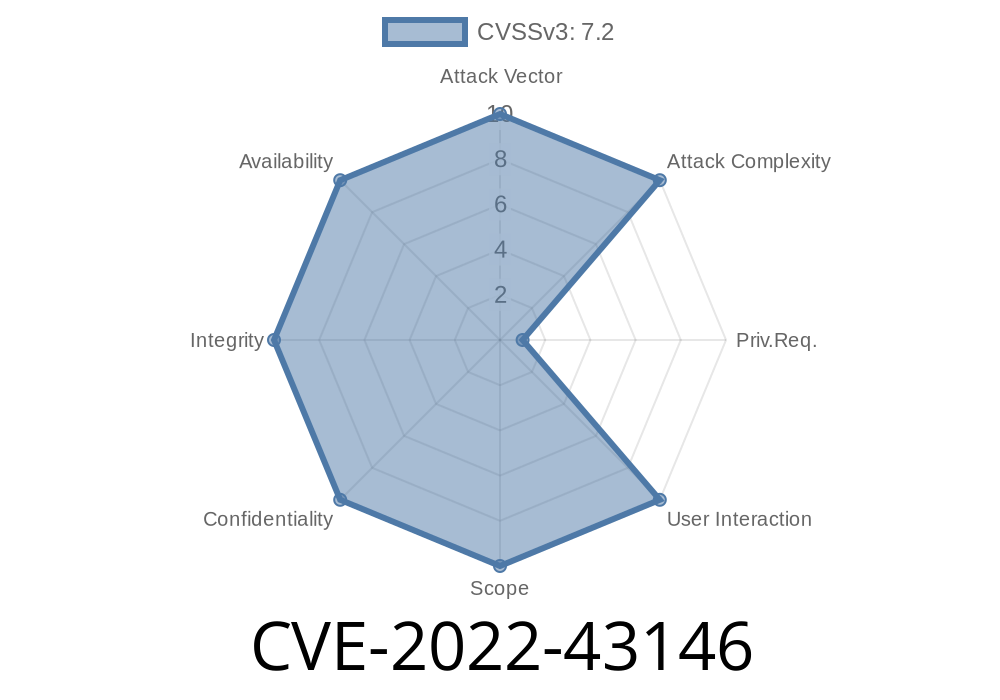
Canteen Management System v2.0
Canteen Management System v2.0 is prone to an arbitrary file posting vulnerability due to the fact that it does not sanitize the posting of uploaded files before posting. A person with a system security breach can, therefore, upload a malicious PHP script or any other type of arbitrary PHP code onto the server.
In order to mitigate these vulnerabilities, Canteen Management System v2.0 should validate its input on the uploaded file’s file name and sanitize its deletion and modification before uploading and manipulating the files.
Timeline
Published on: 11/14/2022 21:15:00 UTC
Last modified on: 11/17/2022 14:49:00 UTC