D-Link DIR878 1.30B08 Hotfix_04 was discovered to be vulnerable to command injection attacks when it was accessed via the component /bin/proc.cgi. An attacker would need to craft a special request to inject malicious commands into the application. For example, an attacker could send a request along the lines of ”/bin/proc.cgi?cmd=dir 1.30B08” to gain remote access to the vulnerable software.
D-Link DIR878 1.30B08 Hotfix_04 was discovered to be vulnerable to cross-site request forgery (CSRF) attacks when it was accessed via the component /bin/proc.cgi. An attacker would need to send a specially crafted request to inject malicious commands into the application. For example, an attacker could send a request along the lines of ”/bin/proc.cgi?cmd=dir 1.30B08” to gain remote access to the vulnerable software. The server might validate the request via CSRF tokens, but not all servers do.
D-Link DIR878 1.30B08 Hotfix_05
D-Link DIR878 1.30B08 Hotfix_05 was discovered to be vulnerable to command injection attacks when it was accessed via the component /bin/proc.cgi. An attacker would need to craft a special request to inject malicious commands into the application. For example, an attacker could send a request along the lines of ”/bin/proc.cgi?cmd=dir 1.30B08” to gain remote access to the vulnerable software.
D-Link DIR878 1.30B16 FP7 Hotfix
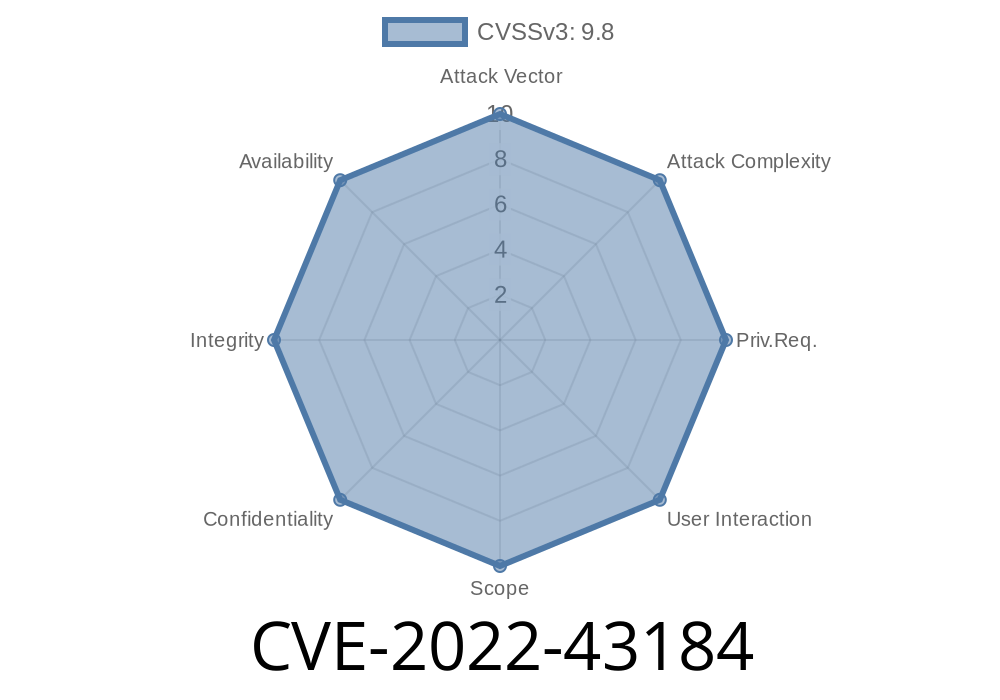
D-Link DIR878 1.30B16 FP7 Hotfix was released to address the vulnerability CVE-2022-43184. This update resolves the vulnerability, and users should install this update if they are running a vulnerable version of the software.
D-Link DIR878 1.30B08 Remote Code Execution Vulnerability
One of the most common ways to execute commands on a server is through a remote code execution vulnerability. This vulnerability allowed an attacker to exploit the application and execute their own commands via an HTTP request. This was done by submitting malicious requests to the vulnerable software, which would then execute those commands without any validation.
D-Link DIR878 1.30B08 Hotfix_04 was discovered to be vulnerable to command injection attacks when it was accessed via the component /bin/proc.cgi. An attacker would need to craft a special request to inject malicious commands into the application. For example, an attacker could send a request along the lines of ”/bin/proc.cgi?cmd=dir 1.30B08” to gain remote access to the vulnerable software.
D-Link DIR878 1.30B08 Hotfix_04 was discovered to be vulnerable to cross-site request forgery (CSRF) attacks when it was accessed via the component /bin/proc.cgi. An attacker would need to send a specially crafted request to inject malicious commands into the application. For example, an attacker could send a request along the lines of ”/bin/proc.cgi?cmd=dir 1.30B08” to gain remote access to the vulnerable software. The server might validate the request via CSRF tokens, but not all servers do.
Timeline
Published on: 10/19/2022 14:15:00 UTC
Last modified on: 10/20/2022 20:05:00 UTC