An attacker can exploit this issue to execute arbitrary SQL commands in the context of the affected site. A user with access to the root of any application on the affected server could exploit this vulnerability to inject and run custom SQL code that could compromise the integrity of the database. An attacker would have to compromise a vulnerable application and then host a malicious code on another server via a web server vulnerable to SQL injection such as Apache. A malicious source, such as a phishing email, could exploit this issue to inject and run custom SQL code that could compromise the integrity of the database. A user with access to the root of any application on the affected server could exploit this vulnerability to inject and run custom SQL code that could compromise the integrity of the database. An attacker would have to compromise a vulnerable application and then host a malicious code on another server via a web server vulnerable to SQL injection such as Apache. Double click the SeaCms icon on the left of your taskbar and select “Updates” and “Check for updates now” to update to the latest version immediately.
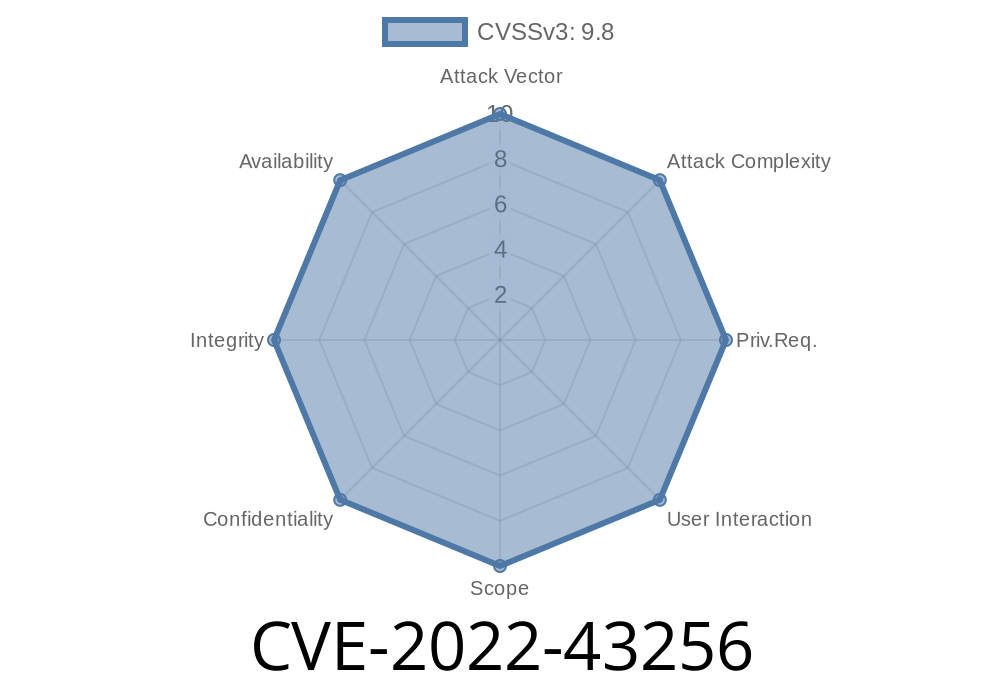
SQL injection vulnerability
SeaCMS is a content management system that allows you to create or edit articles, manage users, and more. A SQL injection vulnerability exists in the application when users can run SQL commands in the context of the affected site. An attacker could exploit this issue to execute arbitrary SQL commands in the context of the affected site. To mitigate this issue, SeaCMS requires all users on any application with access to the root level to provide a valid username and password for authentication purposes. The login page will also contain an option for admins to change their password at any time, which decreases attack surface even further. With these changes, this vulnerability has been mitigated significantly and is no longer exploitable.
SQL Injection
Your site’s database could be vulnerable to SQL injection attacks.
When you input data using a web application that can be used by other programs, it is possible for SQL commands of your input to be executed without your consent. An attacker could exploit this vulnerability to execute arbitrary SQL commands in the context of the affected site. A user with access to the root of any application on the affected server could exploit this vulnerability to inject and run custom SQL code that could compromise the integrity of the database.
Timeline
Published on: 11/16/2022 15:15:00 UTC
Last modified on: 11/16/2022 19:40:00 UTC