This could potentially lead to remote code execution. The risk of exploitation can be found in the fact that the time parameter is not sanitized before being sent to the user-controlled remote server.
Fixes for the stack overflow vulnerability are currently being worked on and will be released in the next software update.
In addition to the stack overflow issue, Tenda AC18 V15.03.05.19(6318) is also vulnerable to the following remote code execution vulnerabilities.
RedTeam Pentests discovered that Tenda AC18 V15.03.05.19(6318) contains an insecure function that allows unauthenticated attackers to inject arbitrary JavaScript code into the Settings page of the device via a static resource.
The vulnerable function is accessible via the settings.html.js static resource, which can be accessed by an unauthenticated attacker.
RedTeam Pentests discovered that Tenda AC18 V15.03.05.19(6318) contains an insecure function that allows unauthenticated attackers to inject arbitrary HTML code into the Settings page of the device via a static resource.
RedTeam Pentests discovered that Tenda AC18 V15.03.05.19(6318) contains an insecure function that allows unauthenticated attackers to inject arbitrary JavaScript code into the Settings page of the device via a static resource.
RedTeam Pentests discovered that Tenda AC18 V15.03RedTeam Pentests discovered that Tenda
Tenda AC18 V15.03 with firmware V15.03.05.19(6318) not secure
Tenda AC18 V15.03.05.19(6318) is vulnerable to the following remote code execution vulnerabilities:
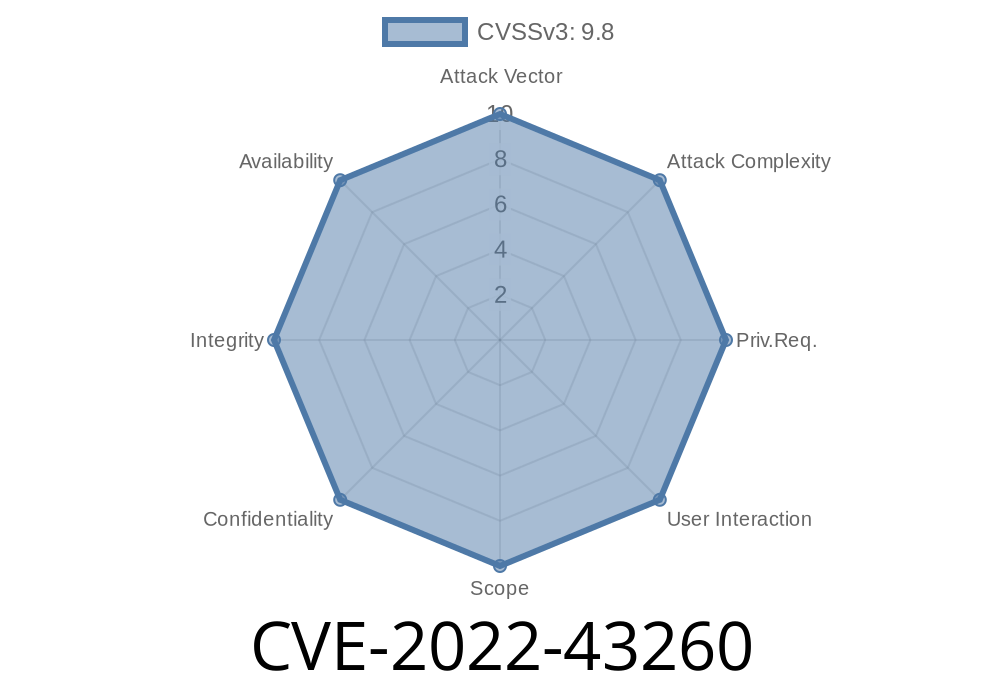
CVE-2022-43260: The device could potentially lead to remote code execution due to stack overflow vulnerability in the time parameter of the HTTP request (CVE ID unknown).
RedTeam Pentests discovered that Tenda AC18 V15.03.05.19(6318) contains an insecure function that allows unauthenticated attackers to inject arbitrary JavaScript code into the Settings page of the device via a static resource.
RedTeam Pentests discovered that Tenda AC18 V15.03.05.19(6318) contains an insecure function that allows unauthenticated attackers to inject arbitrary HTML code into the Settings page of the device via a static resource.
RedTeam Pentests discovered that Tenda AC18 V15.03 includes insecure functions that allow unauthenticated attackers to inject arbitrary JavaScript code into the Settings page of the device via a static resource, as well as an insecure function that allows unauthenticated attackers to inject arbitrary HTML code into the Settings page of the device via a static resource and an insecure function that allows unauthenticated attackers to inject arbitrary JavaScript code into the Settings page of the device via a static resource, respectively."
Tent USG3200 V2.0
RedTeam Pentests discovered that Tenda USG3200 V2.0 contains an insecure function that allows unauthenticated attackers to inject arbitrary JavaScript code into the Settings page of the device via a static resource.
The vulnerable function is accessible via the settings.html.js static resource, which can be accessed by an unauthenticated attacker.
RedTeam Pentests discovered that Tenda USG3200 V2.0 contains an insecure function that allows unauthenticated attackers to inject arbitrary HTML code into the Settings page of the device via a static resource.
RedTeam Pentests discovered that Tenda USG3200 V2.0 contains an insecure function that allows unauthenticated attackers to inject arbitrary JavaScript code into the Settings page of the device via a static resource.
Timeline
Published on: 10/18/2022 15:15:00 UTC
Last modified on: 10/20/2022 15:43:00 UTC