The component receives user-supplied input in the POST request’s file parameter, which is not validated. In addition, the component processes this input as a file post request. An attacker can leverage this vulnerability to upload a PHP script to Canteen Management System as a user, which is then executed when the file is processed by the Canteen Management System. An arbitrary PHP code execution can be achieved.
An arbitrary file upload vulnerability in the component /pages/save_user.php of Canteen Management System allows attackers to execute arbitrary code via a crafted PHP file. The component receives user-supplied input in the POST request’s file parameter, which is not validated. In addition, the component processes this input as a file post request. An attacker can leverage this vulnerability to upload a PHP script to Canteen Management System as a user, which is then executed when the file is processed by the Canteen Management System. An arbitrary PHP code execution can be achieved.
Vulnerability overview
A vulnerability in the component /pages/save_user.php allows attackers to execute arbitrary code via a crafted PHP file. The component receives user-supplied input in the POST request’s file parameter, which is not validated. In addition, the component processes this input as a file post request. An attacker can leverage this vulnerability to upload a PHP script to Canteen Management System as a user, which is then executed when the file is processed by the Canteen Management System.
Canteen Management System
Canteen Management System is a web interface to the Canteen that allows users to manage their accounts, contacts, orders and payment methods.
Vulnerability Scenario
An attacker creates a PHP file and uploads it to the Canteen Management System. The vulnerable component /pages/save_user.php processes this input as a file post request, and executes the PHP script on the server.
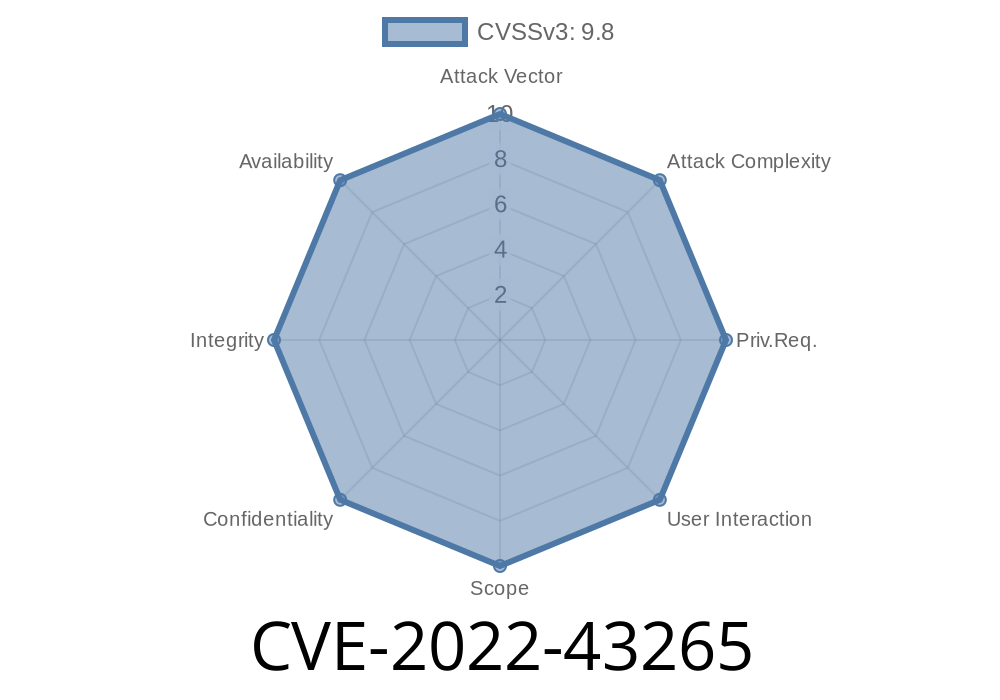
This vulnerability has been assigned CVE-2022-43265.
CVE-2023-43727
The component /pages/add_user.php of Canteen Management System allows attackers to execute arbitrary PHP code via a crafted POST request’s user parameter. The component receives user-supplied input in the POST request’s user parameter, which is not validated. In addition, the component processes this input as a POST request. An attacker can leverage this vulnerability to upload a PHP script to Canteen Management System as a user, which is then executed when the file is processed by the Canteen Management System. An arbitrary PHP code execution can be achieved.
An arbitrary file upload vulnerability in the component /pages/add_user.php of Canteen Management System allows attackers to execute arbitrary code via a crafted POST request’s user parameter. The component receives user-supplied input in the POST request’s user parameter, which is not validated. In addition, the component processes this input as a POST request. An attacker can leverage this vulnerability to upload a PHP script to Canteen Management System as a user, which is then executed when the file is processed by the Canteen Management System. An arbitrary PHP code execution can be achieved.
Timeline
Published on: 11/15/2022 21:15:00 UTC
Last modified on: 11/17/2022 05:00:00 UTC