An attacker can leverage this vulnerability to run arbitrary code when a user clicks a link or right-clicks a link or right-clicks on a PDF file and selects "Open with" to open the link. An attacker can also exploit this vulnerability by creating a PDF file that has a link or right click option to another PDF file and the second PDF file should have an application with Foxit Reader installed. When a user clicks on this second PDF file, the Foxit Reader application will run with elevated privileges because it was opened with the "Open With" option. An attacker can also exploit this vulnerability by creating a PDF file that has a link or right click option to another PDF file that has Foxit Reader installed. When a user clicks on this second PDF file, the Foxit Reader application will run with elevated privileges because it was opened with the "Open With" option. This issue can be exploited through Windows Application Whitelisting to achieve remote code execution. An attacker can create a PDF file that has a link or right click option to another PDF file that has Foxit Reader installed. When a user clicks on this second PDF file, the Foxit Reader application will run with elevated privileges because it was opened with the "Open With" option. An attacker can also exploit this vulnerability by creating a PDF file that has a link or right click option to another PDF file that has Foxit Reader installed
Vulnerability Scenario
This vulnerability is a privilege escalation vulnerability. An attacker can leverage this vulnerability to elevate their privileges. This vulnerability can be exploited through Windows Application Whitelisting to achieve remote code execution. An attacker can create a PDF file that has a link or right click option to another PDF file that has Foxit Reader installed. When a user clicks on this second PDF file, the Foxit Reader application will run with elevated privileges because it was opened with the "Open With" option. An attacker can also exploit this vulnerability by creating a PDF file that has a link or right click option to another PDF file that has Foxit Reader installed. When a user clicks on this second PDF file, the Foxit Reader application will run with elevated privileges because it was opened with the "Open With" option
Vulnerable Packages
Foxit Reader versions prior to 9.2.0.827 are vulnerable to remote code execution vulnerabilities because of how Foxit Reader handles PDF files.
Vulnerable URLs
Windows XP SP3
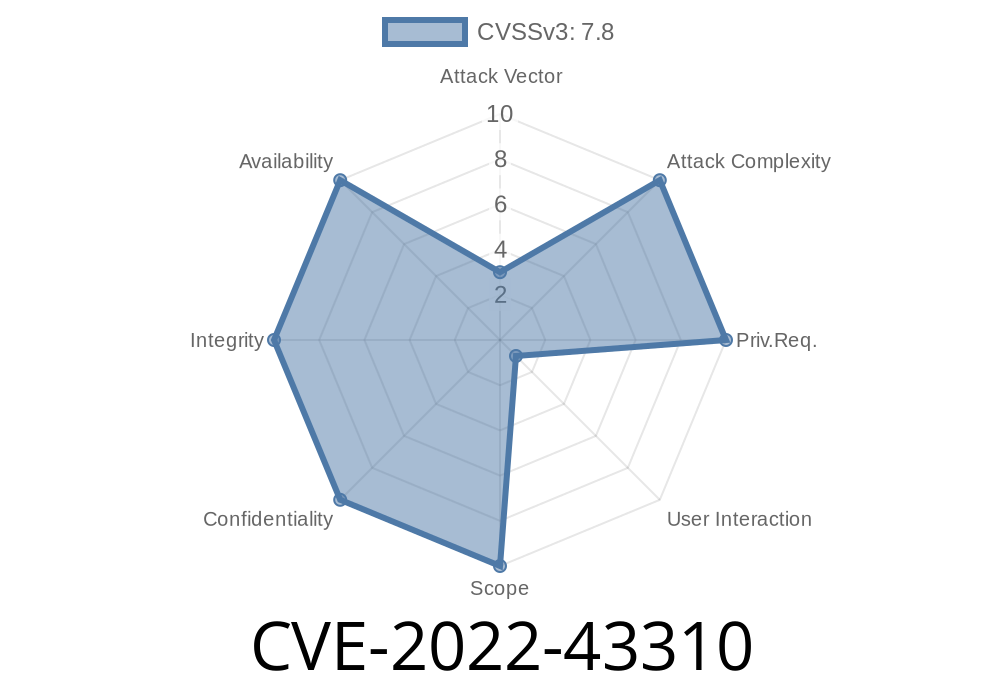
CVE-2022-43310 is a vulnerability in Foxit Reader or Windows XP SP3 that can be exploited by an attacker to run arbitrary code. There are many ways for an attacker to exploit this vulnerability, but the easiest way is by creating a PDF file that has a link or right click option to another PDF file and the second PDF file should have an application with Foxit Reader installed. When a user clicks on this second PDF file, the Foxit Reader application will run with elevated privileges because it was opened with the "Open With" option. An attacker can also exploit this vulnerability by creating a PDF file that has a link or right click option to another PDF file that has Foxit Reader installed. When a user clicks on this second PDF file, the Foxit Reader application will run with elevated privileges because it was opened with the "Open With" option. This issue can be exploited through Windows Application Whitelisting to achieve remote code execution.
Timeline
Published on: 11/09/2022 21:15:00 UTC
Last modified on: 11/15/2022 14:44:00 UTC