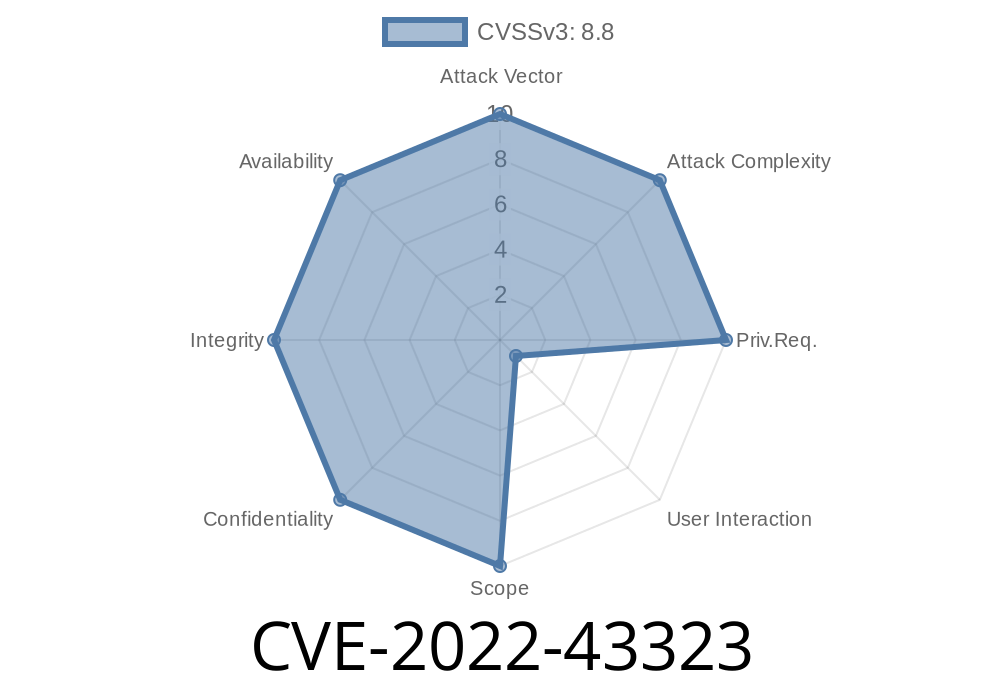
This issue can be exploited to hijack the user's session if he/she has the same email address on the site as on the login system. An attacker can use a malicious script or image to trick the user into clicking on it, which then could be used to perform actions on the user's behalf. It is recommended that you update the affected version to V1.5.9-UTF8-SP2. V1.5.9-UTF8-SP2 was discovered to contain a Cross-Site Request Forgery (CSRF) via the Top Up Balance component under the Edit Member module. This issue can be exploited to hijack the user's session if he/she has the same email address on the site as on the login system. An attacker can use a malicious script or image to trick the user into clicking on it, which then could be used to perform actions on the user's behalf. It is recommended that you update the affected version to V1.5.9-UTF8-SP3. V1.5.9-UTF8-SP3 was discovered to contain a Cross-Site Request Forgery (CSRF) via the Top Up Balance component under the Edit Member module. This issue can be exploited to hijack the user's session if he/she has the same email address on the site as on the login system. An attacker can use a malicious script or image to trick the user into clicking on it, which then could be
1.5.9-UTF8-SP4
V1.5.9-UTF8-SP4 was discovered to contain a Cross-Site Request Forgery (CSRF) via the Edit Member module. This issue can be exploited to hijack the user's session if he/she has the same email address on the site as on the login system. An attacker can use a malicious script or image to trick the user into clicking on it, which then could be used to perform actions on the user's behalf. It is recommended that you update the affected version to V1.5.9-UTF8-SP4.
Solution to CVE-2022-43323
Update to V1.5.9-UTF8-SP2 and V1.5.9-UTF8-SP3
Timeline
Published on: 11/14/2022 20:15:00 UTC
Last modified on: 11/16/2022 23:11:00 UTC