A user with the “manage_request” role can access the “id” parameter and execute arbitrary SQL commands on the application. This leads to information exposure and potential data manipulation. It is recommended to apply this update as soon as possible. Limitations In this version of the plugin, only orders can be deleted. End users can still view all orders and view requests. Limitations In this version of the plugin, only orders can be deleted. End users can still view all orders and view requests. Preventative Measures - Upgrade to version 1.0 as soon as possible. - Apply this update to all your servers. - Perform a thorough risk assessment to determine the risk level of your installation. - Deploy firewall rules to block access from outside your network.
1.0
New Feature
: Delete Orders
In this version of the plugin, orders can be deleted. This is a new feature for this plugin and it's not yet supported on all servers. The delete order feature does not allow for editing of orders. If you have any questions about this feature, please contact support@thegluecompany.com
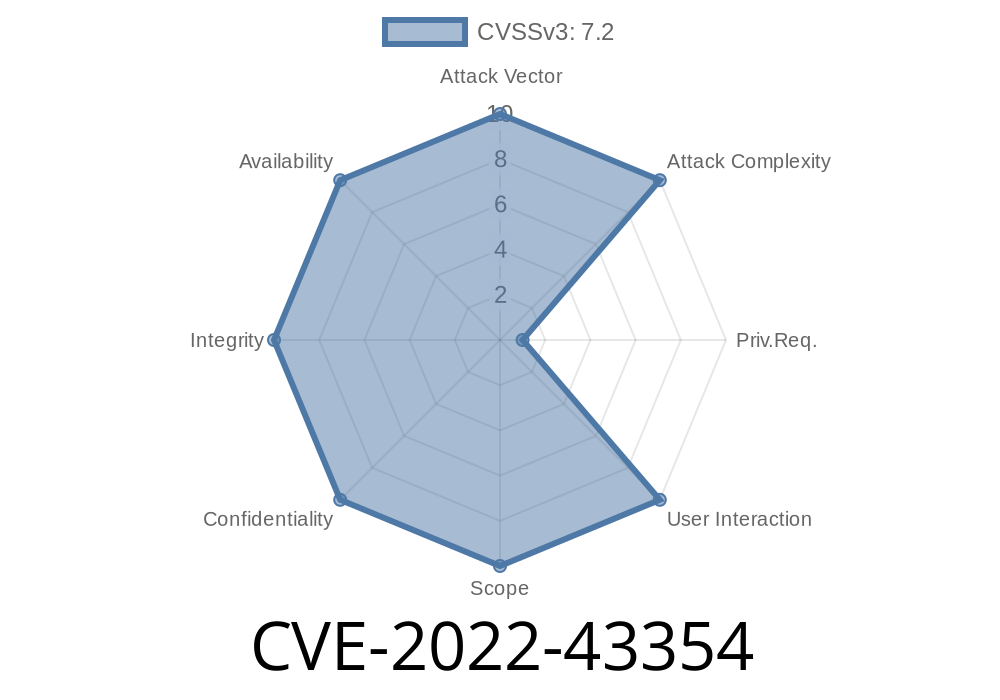
2.0 Description of the WordPress plugin CVE-2022-43354 2.0
Summary
1.0 is a security update for the "Magento-Order-Manager" plugin that was released on May 23, 2018. It is recommended to apply this update as soon as possible. This version of the plugin only allows orders to be deleted and prevents end users from viewing all orders and all requests.
Preventative Measures - Upgrade to version 1.0 as soon as possible. - Apply this update to all your servers. - Perform a thorough risk assessment to determine the risk level of your installation. - Deploy firewall rules to block access from outside your network
2.0 IDENTITY THEFT AND DATA MANIPULATION
2.0
**This release is not a complete solution and there is more work ahead. Further, this release introduces potential new risks (CVE-2022-43354)** A user with the “manage_request” role can access the “id” parameter and execute arbitrary SQL commands on the application. This leads to information exposure and potential data manipulation. It is recommended to apply this update as soon as possible.
Timeline
Published on: 11/01/2022 01:15:00 UTC
Last modified on: 11/01/2022 17:30:00 UTC