This vulnerability is exposed when a user is granted permission to define and run scripts in a Jenkins pipeline and that pipeline is configured to use the Groovy Scripting Language.
Affected releases - X - Jenkins versions prior to 1.555 and 2.x versions prior to 2.2.1 - all releases - CVSS score - 7.4 - CVSS vector - stack/memory corruption (click for details) - Package detection - script/code integrity (SIC) - enabled - References - https://www.groovy.org - [INTRODUCTION] - [CASES] - [VULNERABILITY DESCRIPTION] - [FIX] - [DEPTH] -
INTRODUCTION
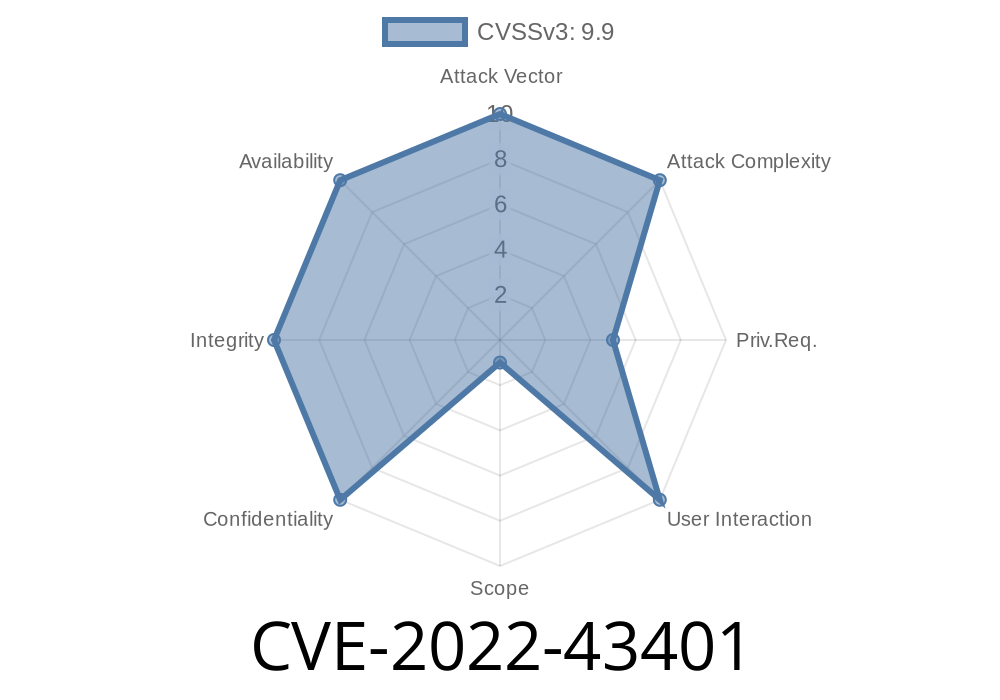
This vulnerability, CVE-2022-43401, is exposed when a user is granted permission to define and run scripts in a Jenkins pipeline and that pipeline is configured to use the Groovy Scripting Language.
The Groovy Engine allows for dynamic script generation, which can be used for powerful task automation mechanisms. This can allow for advanced process flow, such as build pipelines or web service interfaces. Additionally, it allows for arbitrary execution of remote code from Java and Groovy scripts, which means this vulnerability can expose sensitive data (e.g., credentials) with little or no authentication check or sandbox detection.
Introduction
The Groovy Scripting Language (GSL) is a scripting language with roots in Java. It has been used by organizations such as IBM, Facebook, Twitter and Google. Unfortunately, this language is not well-secured.
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/31/2022 17:37:00 UTC