This issue is due to Groovy’s implicit casting from one type to another, which can be exploited to bypass the security policy. Attackers can use certain Groovy expressions to perform a variety of actions such as creating or deleting files, sending network requests, or exfiltrating data from the Jenkins master. In some cases, attackers can even bypass the security restrictions and directly manipulate the Jenkins configuration or application code, for example by deleting a Jenkins installation. An attacker can leverage this vulnerability to perform malicious actions on the Jenkins master such as performing an attack via the web interface or by shutting down the Jenkins master. How this Vulnerability Occurs? There are various ways an attacker can exploit this vulnerability. An attacker can create a Groovy pipeline plugin that has an insecure casting statement in it, or create a pipeline that has an insecure casting statement in it. An attacker can create a new Jenkins instance and copy an insecure casting statement into the plugin definition of the new instance. An attacker can upload an insecure casting statement into the web interface of an existing Jenkins instance. After an attacker has created an insecure pipeline plugin, he/she can create new pipelines that have an insecure casting statement in them
Protecting against this vulnerability Configuration:
Modify the Jenkins configuration to use a Groovy compiler that has an option for security-sensitive code verification.
File System:
Configure Jenkins to restrict the access of sensitive files to only the user account owning them and disable the execution of untrusted Groovy scripts.
Network:
Configure Jenkins to restrict the network connections that can be made by untrusted Groovy scripts.
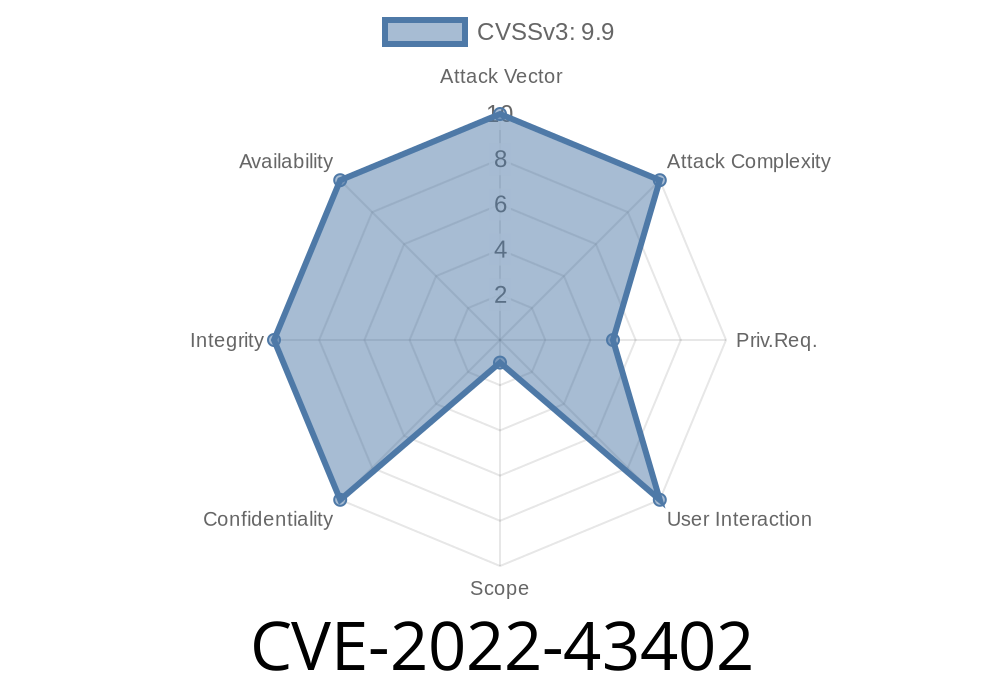
CVE-2022-43403
This issue is due to Groovy’s implicit casting from one type to another, which can be exploited to bypass the security policy. Attackers can use certain Groovy expressions to perform a variety of actions such as creating or deleting files, sending network requests, or exfiltrating data from the Jenkins master. In some cases, attackers can even bypass the security restrictions and directly manipulate the Jenkins configuration or application code, for example by deleting a Jenkins installation. An attacker can leverage this vulnerability to perform malicious actions on the Jenkins master such as performing an attack via the web interface or by shutting down the Jenkins master. How this Vulnerability Occurs? There are various ways an attacker can exploit this vulnerability. An attacker can create a Groovy pipeline plugin that has an insecure casting statement in it, or create a pipeline that has an insecure casting statement in it. An attacker can create a new Jenkins instance and copy an insecure casting statement into the plugin definition of the new instance. An attacker can upload an insecure casting statement into the web interface of an existing Jenkins instance. After an attacker has created an insecure pipeline plugin, he/she can create new pipelines that have an insecure casting statement in them
Instances Where This Vulnerability Can Be Exploited
This vulnerability is most commonly exploited by attackers who have gained access to a Jenkins master. If an attacker has gained access to the Jenkins master, they can exploit this vulnerability from their laptop or mobile device. As mentioned above, an attacker can also exploit this vulnerability in a new instance created using Groovy’s CopyInstance plugin.
The Attacker Control Panel
This is the Jenkins attacker control panel page. This page provides information about the attack. The following tabs are available:
Vulnerability Details
The vulnerability details tab provides a detailed list of affected versions, affected releases, affected builds, and the CVE-2022-43402. It also lists which security policies have been bypassed.
Commands
The commands tab shows the Groovy expressions that are used by attackers to bypass security restrictions and take actions such as sending network requests or exfiltrating data from Jenkins master
Apps
The apps tab shows the applications that were targeted by this vulnerability. It provides information about whether or not any of these applications were deployed on an insecure pipeline plugin.
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/21/2022 14:42:00 UTC