This can be exploited by malicious code to escalate privileges or cause a Denial of Service (DoS) attack. A malicious attacker can inject code into a Jenkins pipeline definition or Jenkins job definition that when executed allows them to break out of the sandbox, allowing them to access and potentially modify other data in the Jenkins environment, such as another pipelines, network configurations and host information.
An attacker can inject code into a Jenkins pipeline definition or Jenkins job definition that when executed allows them to break out of the sandbox, allowing them to access and potentially modify other data in the Jenkins environment, such as another pipelines, network configurations and host information. This vulnerability is caused due to the implementation of casting an array-like value to an array type in Jenkins Script Security Plugin 1183.v774b_0b_0a_a_451 and earlier. An attacker with code access can cast an array-like value to an array type and create a script that accesses data from other packages, networks or external systems, which may allow the attacker to gain access to other data and systems.
Hackers can create shells allowing them to access other environments
Jenkins is an open-source automation platform and toolset that builds, tests, deploys, and monitors applications. Jenkins has powerful plugins for building pipelines and jobs, managing Jenkins itself, and automating CI/CD tasks. This allows developers to be more productive with their work with the software.
An attacker can use the vulnerability to create a shell allowing them to access other environments in the Jenkins environment. The malicious code will then break out of the sandbox after the execution of this code, which would allow attackers to potentially access other data in the Jenkins environment such as another pipelines, network configurations and host information.
Solution
Jenkins Script Security Plugin 1183.v774b_0b_0a_a_451 and earlier should be upgraded to Jenkins Script Security Plugin 1184.v774b_0b_0a_c14d.
CVE-2023-43405
A malicious attacker can exploit this vulnerability to bypass the password policy, allowing them to change the password of another user.
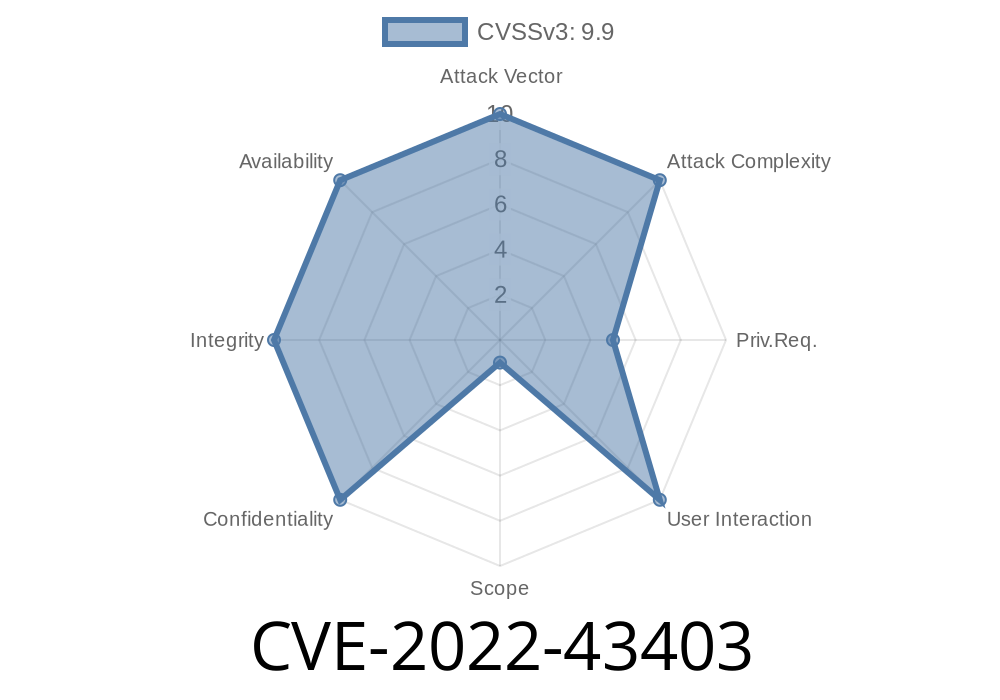
Build Number of Vulnerability CVE-2022-43403
5.0
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/21/2022 15:06:00 UTC