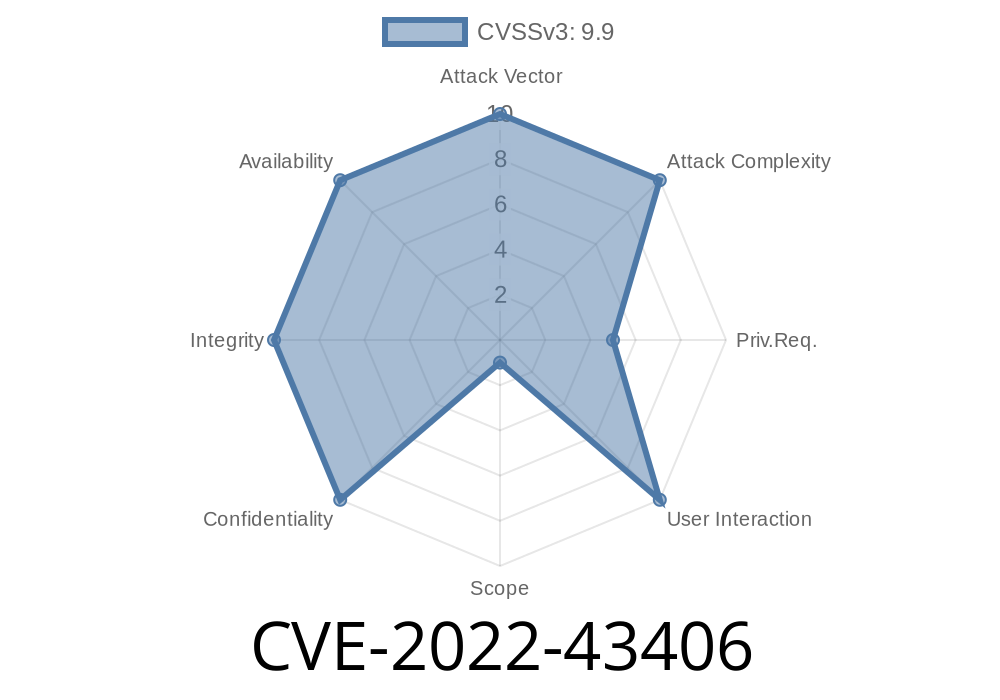
The issue results from the fact that the Deprecated Groovy libraries Plugin does not validate inputs, allowing to inject and execute arbitrary code. This Jenkins issue has been assigned the CSCvb5dv vulnerability reference.
CVE has been assigned to this Jenkins issue because attackers can inject and execute malicious code in the context of the Jenkins controller JVM and cause the affected application to load and execute the code. Note that the sandbox bypass in this case may only affect Jenkins Pipeline: Deprecated Groovy libraries Plugin. For example, an attacker may be able to inject and execute malicious code to obtain sensitive information such as credentials, or to cause the affected application to load and execute the code to obtain access to other systems. REFERENCE: https://github.com/jenkinsci/pipeline/issues/4246
We recommend upgrading Jenkins Pipeline: Deprecated Groovy libraries Plugin 583.vf3b_454e43966 and earlier to the latest version 584.7.vf1b_1e8a2b2e9 to protect against the above Jenkins issue.
Impact Our security team recommends limiting access to untrusted users. If you do not do so, you can avoid the consequences of this Jenkins issue and protect your systems. How To Upgrade To protect against the Jenkins issue, upgrade Jenkins Pipeline: Deprecated Groovy libraries Plugin 583.vf3b_454e43966 and earlier to version 5
References !
[Jenkins]: https://github.com/jenkinsci/pipeline/issues/4246 ![CVE-2022-43406]: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-43406
Install Jenkins Pipeline: Deprecated Groovy libraries Plugin 584.7.vf1b_1e8a2b2e9
Upgrade Jenkins Pipeline: Deprecated Groovy libraries Plugin 583.vf3b_454e43966 and earlier to version 584.7.vf1b_1e8a2b2e9
Solution
Upgrade Jenkins Pipeline: Deprecated Groovy libraries Plugin 584.7.vf1b_1e8a2b2e9 and later.
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/24/2022 14:58:00 UTC