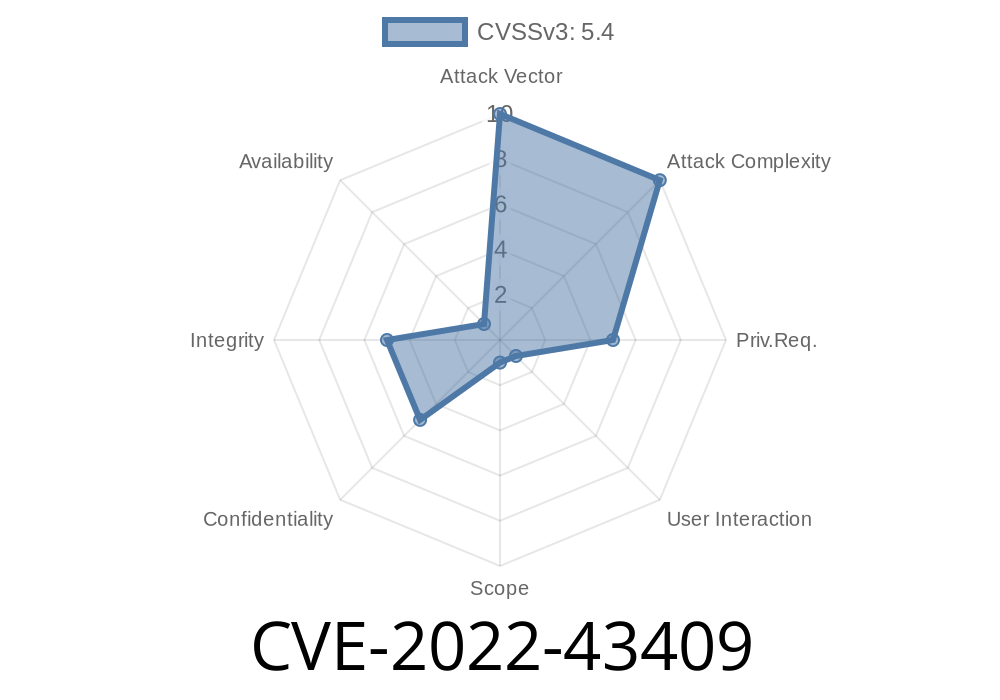
This issue is rated as high severity due to the risk of being exploited via Jenkins’s hosted and public build logs. Stored XSS vulnerabilities in Jenkins’s web interface can be exploited by attackers to gain remote access or by employees who fail to change their XSS-infected credentials. End users are advised to upgrade Jenkins to version 838.va_3a_087b_4055b or later.
Background information
Jenkins is a popular open source automation server that allows developers to continuously build, test, and deploy their projects. Its popularity has become so widespread that it is now hosted by major companies such as Microsoft, IBM, and Red Hat.
A Jenkins vulnerability was discovered in Jenkins’s web interface that allows remote attackers to inject JavaScript into the application's website or steal sensitive information from vulnerable end users.
The vulnerability was found in Jenkins’s public build logs. Anyone can view these public build logs on Jenkins’s website without authentication. This vulnerability probably went unnoticed for some time because the victim would have had to be logged in on the site for this issue to be exploitable.
The vulnerability could also have been exploited by employees who failed to change their XSS-infected credentials. The threat actors could have then gained access to Jenkins’s system and executed actions remotely without any authentication or authorization needed.
Description
CVE-2022-43409 is the vulnerable component in Jenkins. This vulnerability has been assigned a high severity rating because it allows attackers to gain remote access or by employees who cannot change their XSS-infected credentials.
The vulnerability exists in Jenkins's web interface and is triggered if an attacker sends a malicious request to the application's build logs. The flaw can be exploited by sending a crafted URL, leading to stored XSS vulnerabilities in Jenkins’s web interface which would allow attackers to execute JavaScript with no need for further authentication. In some cases, users who have already been authenticated can exploit this vulnerability without having changed their password over time.
Update Instructions
Because this issue is rated high severity, follow the instructions below:
- See the Upgrade Instructions section in the reference for a complete list of steps to take.
- Follow these instructions to update Jenkins:
o Navigate to the Jenkins download page at https://jenkins.io/downloads/
o Download and execute the auto-update script from your terminal application.
o To install from source, use one of the following commands:
sudo apt-get update && sudo apt-get -y upgrade
cd /tmp && wget https://jenkins.io/downloads/maven.repo -O jenkins.repo
sudo mv jenkins.repo /etc/apt/sources.list.d/jenkins.list
sudo apt-key adv --keyserver hkp://keyserver.ubuntu.com:80 --recv E16AD0E4
sudo apt update && sudo apt install jenkins
cd /var/lib/jenkins/.jenkins
mv jenkins_home /opt/jenkins
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/21/2022 17:20:00 UTC