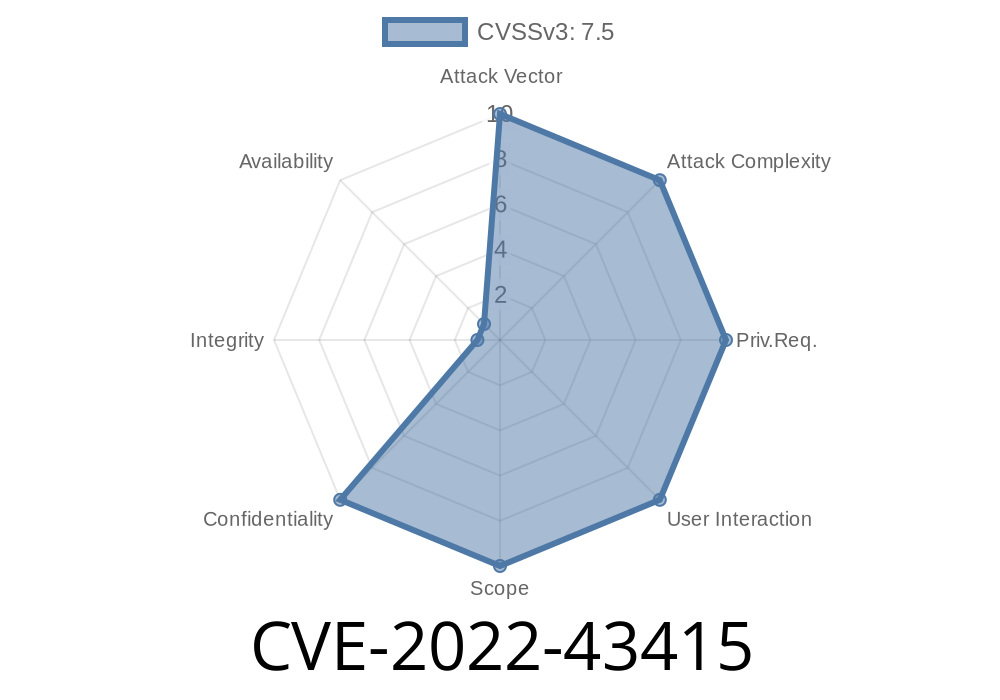
The Jenkins REPO plugin does not properly sanitize XML data before passing it on to external systems, allowing attackers to exploit this by crafting a malicious XML document and forcing Jenkins to render it. An attacker could use this to exploit Jenkins’s third-party plugins, leading to a wide range of impacts, depending on the plugin’s functionality and configuration. An attacker could also use this to exploit Jenkins’s internal systems, leading to a wide range of impacts, depending on the system’s functionality and configuration. In order to exploit this issue, an attacker would have to force Jenkins to process a malicious XML document. This may be done by compromising a Jenkins installation, or by forcing Jenkins to render a malicious XML document. Another possible way to exploit this issue is to force Jenkins to process a malicious XML document that comes from an untrusted feed via an insecure channel.
Limitations of the CVE
The vulnerability is in the REPO plugin, which is not used by default and may not be enabled in your environment. The vulnerability goes undiscovered if Jenkins’s security settings are configured to use only whitelisted feeds, and if Jenkins’s system is properly configured to allow only whitelisted feeds. An attacker would also have to be able to craft a malicious XML document that could be processed by the REPO plugin in order to exploit this vulnerability. Finally, an attacker would need access to a Jenkins installation or its configuration; or they would need to compromise a third-party plugin with an insecure feed.
# 4 Ways You Can Mitigate This Vulnerability
Sightings of CVE-2022-43415
Cisco Talos has not seen any significant active exploitation of this vulnerability yet.
Tested Version:
Jenkins 1.591
Jenkins 1.592
Jenkins 1.594
The Jenkins REPO plugin does not properly sanitize XML data before passing it on to external systems, allowing attackers to exploit this by crafting a malicious XML document and forcing Jenkins to render it. An attacker could use this to exploit Jenkins’s third-party plugins, leading to a wide range of impacts, depending on the plugin’s functionality and configuration. An attacker could also use this to exploit Jenkins’s internal systems, leading to a wide range of impacts, depending on the system’s functionality and configuration. In order to exploit this issue, an attacker would have to force Jenkins to process a malicious XML document. This may be done by compromising a Jenkins installation, or by forcing Jenkins to render a malicious XML document. Another possible way to exploit this issue is to force Jenkins to process a malicious XML document that comes from an untrusted feed via an insecure channel.
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/21/2022 03:15:00 UTC