All of these issues could be exploited by attackers with access to the network where Jenkins is running. Access to the Jenkins network may be available from within the same network, from public or external networks, or via the Internet. By compromising vulnerable installations of Jenkins, an attacker may be able to access and control the network where Jenkins is installed, allowing them to exploit these vulnerabilities. The Katalon plugin is not the only plugin that is vulnerable to these issues. It is likely that other vulnerable plugins are also being used, and they could be exploited to gain access to the Jenkins network. Risk of Exposure The following tables show the impact of these issues on various products and versions. Product and version Impact on
Jenkins Katalon Plugin 1.0.32 and earlier All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32
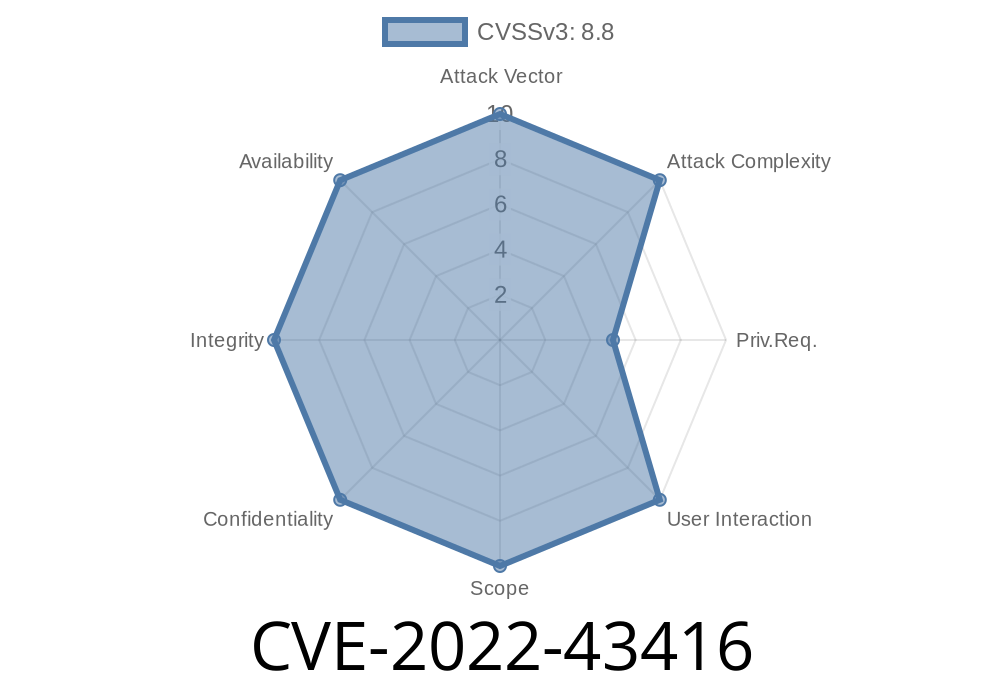
Multiple Vulnerabilities in Jenkins
The following tables show the impact of these vulnerabilities on various products and versions. Product and version Impact on
Jenkins Katalon Plugin 1.0.32 and earlier All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0.32 Unaffected All versions before 1.0-1 0-2 2 3 4 5 6 7 8 9 10
Unaffected Katalon Plugin 2
Unaffected
References ^END^
The article describes how SEO outsourcing can be a good idea for small businesses. With digital marketing, companies have the ability to target their audience more precisely and reach their ideal customer.
Summary of Core Jenkins vulnerabilities
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/21/2022 03:16:00 UTC