This issue affects the “Credential Discovery” report type only and can be exploited by attackers when Contrast service is used for password management, for example, via a user management system like Active Directory. Jenkins administrators are strongly advised to update to version 3.9.1 or later as soon as possible. A fix has also been released for the Jenkins service itself to avoid possible denial of service due to this issue. In addition, a rev 1.9.1 release of the Jenkins service is available to prevent possible remote code execution due to this issue. When upgrading to Jenkins version 3.9.1 or later, it is also recommended to update the version of the Contrast security plugin on all of the managed host operating systems to rev 3.9.1, in order to avoid possible XSS issues.
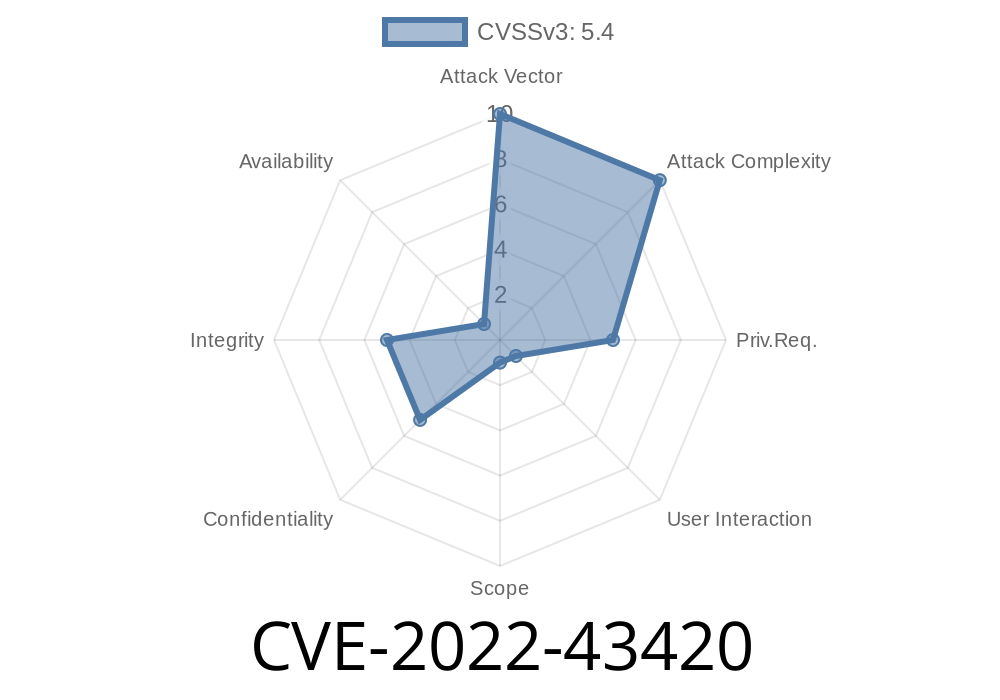
Summary of CVE-2022-43420
This issue affects the “Credential Discovery” report type only and can be exploited by attackers when Contrast service is used for password management, for example, via a user management system like Active Directory. Jenkins administrators are strongly advised to update to version 3.9.1 or later as soon as possible. A fix has also been released for the Jenkins service itself to avoid possible denial of service due to this issue. In addition, a rev 1.9.1 release of the Jenkins service is available to prevent possible remote code execution due to this issue. When upgrading to Jenkins version 3.9.1 or later, it is also recommended to update the version of the Contrast security plugin on all of the managed host operating systems to rev 3.9.1, in order to avoid possible XSS issues.
CVE-2021-43418
This issue affects the “Filter Plugin” report type only and can be exploited by attackers when Contrast service is used for password management, for example, via a user management system like Active Directory. Jenkins administrators are strongly advised to update to version 3.9.1 or later as soon as possible. A fix has also been released for the Jenkins service itself to avoid possible denial of service due to this issue. In addition, a rev 1.9.1 release of the Jenkins service is available to prevent possible remote code execution due to this issue. When upgrading to Jenkins version 3.9.1 or later, it is also recommended to update the version of the Contrast security plugin on all of the managed host operating systems to rev 3.9.1, in order to avoid possible XSS issues.>>END>>
Finding the cause of the CVE -2022-43420
This vulnerability was found and fixed by Contrast Security. It has been assigned CVE-2022-43420.
Discovery - CVE-2022-43421
The "Credential Discovery" report type is also impacted and can be exploited by attackers when Contrast service is used for password management, for example, via a user management system like Active Directory. Jenkins administrators are strongly advised to update to version 3.9.1 or later as soon as possible. A fix has also been released for the Jenkins service itself to avoid possible denial of service due to this issue. In addition, a rev 1.9.1 release of the Jenkins service is available to prevent possible remote code execution due to this issue. When upgrading to Jenkins version 3.9.1 or later, it is also recommended to update the version of the Contrast security plugin on all of the managed host operating systems to rev 3.9.1, in order to avoid possible XSS issues.
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/21/2022 03:41:00 UTC