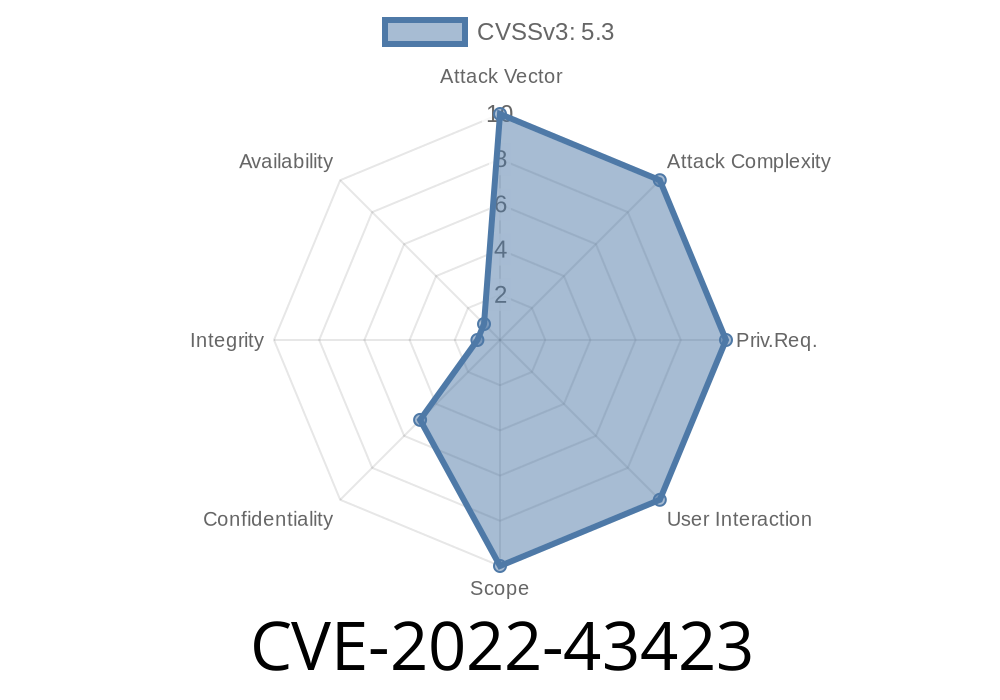
Jenkins versions prior to 2.0.12 are vulnerable to a remote code execution attack.
Agent/Controller Message Processing
PDS Plugin 2.0.12 and earlier does not validate the contents of the agent_controller_name field of the agent/controller message. In particular, if the value of this field is a Java Character, the plugin will try to execute the Java code associated with the Character in the field.
If the plugin receives an agent/controller message with a Java Character in the agent_controller_name field, the plugin will try to execute the Java code associated with the Character.
If the plugin receives an agent/controller message with a non-Java Character, the plugin will ignore the field.
Therefore, if an attacker can control the name of an agent process, they can control how the plugin processes the agent/controller message to obtain system properties.
Mitigation
Administrators of Jenkins instances with Agent/Controller Message Processing enabled should install the vulnerable version of PDS Plugin, update it to 2.0.12 or later, and apply the appropriate CVEs.
Vulnerability Confirmed in Jenkins 2.0.12 and Earlier
Jenkins versions prior to 2.0.12 are vulnerable to a remote code execution attack. This attack puts Jenkins users at risk of having their data stolen or their systems compromised.
The vulnerability was confirmed in Jenkins versions prior to 2.0.12 and affects all installations, not just those on the default settings of Jenkins.
PDS Plugin 2.0.12 and earlier does not validate the contents of the agent_controller_name field of the agent/controller message, which is critical if an attacker can control that field's value during an attack. If this plugin receives a Java Character in the agent_controller_name field, it will try to execute the Java code associated with that Character inside itself--which could potentially lead to data theft or system compromise for those running Jenkins instances with this plugin installed and enabled on their systems.
Finding the PDS Plugin Version
Finding the PDS Plugin Version
The vulnerable version of the PDS plugin is 2.0.12 and earlier.
Recommended Practices
The following are recommended practices to prevent this vulnerability:
- Upgrade to Jenkins 2.0.12 or later.
- Deploy the PDS Plugin 2.0.12 or later with the "disabled" option of agent_controller_name enabled.
- If an agent/controller message contains a Java Character in the agent_controller_name field, it is recommended that you do not process that message further, but rather send it back in its original form via a security notification to your administrator for review and remediation as appropriate.
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/20/2022 18:28:00 UTC