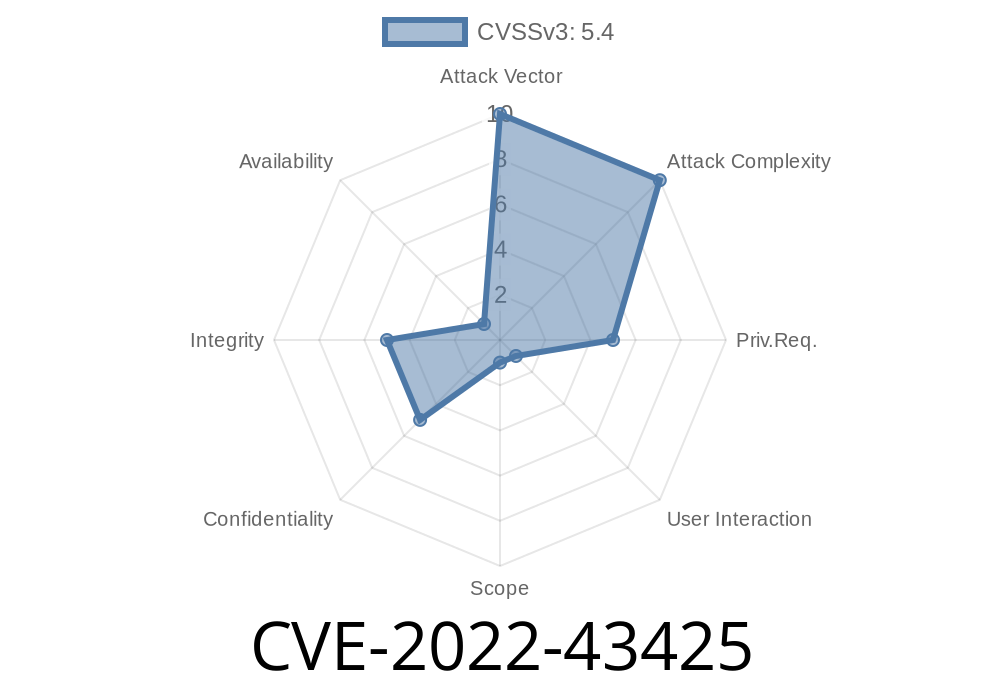
A user with the ability to create a malicious parameter and view, could exploit this vulnerability to inject JavaScript into the affected site’s functionality. This issue was resolved in Jenkins 1.45 by escaping the name and description of the parameters on views displaying the parameters. Jenkins is vulnerable to a stored cross-site scripting (XSS) attack in custom checkbox parameters if it is installed with Jenkins 1.4 or earlier. A malicious administrator with the ability to create or edit a Custom Checkbox Parameter in the Jenkins plugin interface can exploit this issue to inject arbitrary JavaScript into the affected site’s functionality. This issue was resolved in Jenkins 1.45 by escaping the name and description of the parameters on views displaying the parameters.
Installing Jenkins on Ubuntu
This vulnerability has been addressed in Jenkins 1.45
Installing Jenkins on Ubuntu is not affected by this vulnerability
How do I detect if my Jenkins is vulnerable?
The easiest way for you to detect if your Jenkins is vulnerable is to watch for any sign of an XSS attack in the Jenkins logs. For example, a warning message relating to this issue will be logged at jenkins.slackware.com/jobs/
Description
CVE-2022-43425: A user with the ability to create a malicious parameter and view, could exploit this vulnerability to inject JavaScript into the affected site’s functionality. This issue was resolved in Jenkins 1.45 by escaping the name and description of the parameters on views displaying the parameters. Jenkins is vulnerable to a stored cross-site scripting (XSS) attack in custom checkbox parameters if it is installed with Jenkins 1.4 or earlier. A malicious administrator with the ability to create or edit a Custom Checkbox Parameter in the Jenkins plugin interface can exploit this issue to inject arbitrary JavaScript into the affected site’s functionality. This issue was resolved in Jenkins 1.45 by escaping the name and description of the parameters on views displaying the parameters.
CVSS Vector:
(AV:N/AC:L/Au:S/C:C/I:C/A:P) -
CVSS Base Score: 5.3
CVSS Impact Subscore: 4.4
CVSS Vector based on CVE-2019-5480, CVE-2019-5481, and CVE-2019-5482
CVE-2022-43425 is an open source vulnerability found in Jenkins which allows a user to inject JavaScript into the affected site’s functionality. This issue was resolved in Jenkins 1.45 by escaping the name and description of the parameters on views displaying the parameters.
References https://jenkins.io/security-advisories/#CVE-2022-43425
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/22/2022 02:05:00 UTC