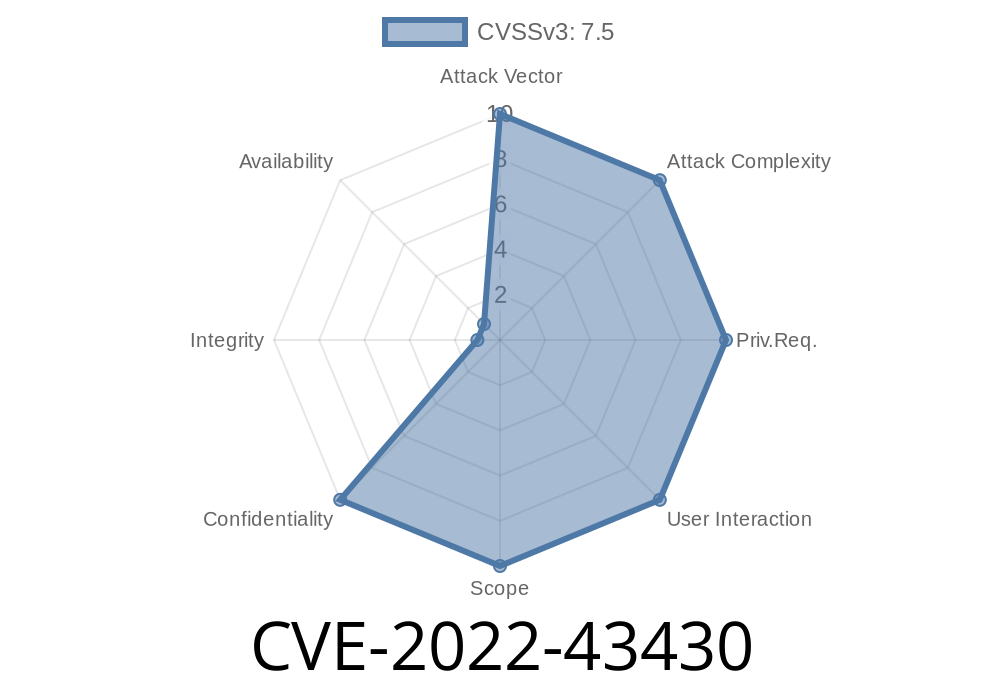
In certain situations, Jenkins may be exposed to a high risk of XXE attacks when it is processing untrusted inputs, such as XML configuration files. This may occur when Jenkins is exposed to inputs that it cannot parse or when it is configured to handle untrusted inputs by default. In these situations, Jenkins may be vulnerable to XXE attacks. A malicious user may attempt to inject XXE attacks into Jenkins by sending untrusted XML configuration files. An attacker may send a specially crafted XML file via a web interface or via a JenkinsXML configuration plugin. A malicious user may also send a malicious XML file via a custom build step. If Jenkins is configured to handle untrusted inputs by default, attackers may choose to send a malicious XML file. In all of these cases, Jenkins will be vulnerable to XXE attacks.
How do you know if you are exposed to XXE attacks?
If Jenkins is configured to handle untrusted inputs by default and an attacker is able to send a malicious XML file, the Jenkins master process will be vulnerable to XXE attacks.
For more information on security issues and mitigation methods, refer to "Understanding Security Issues in Jenkins" in the Jenkins documentation: https://jenkins.io/documentation/security-issues/
XXE Attacks: What are they?
XXE stands for "XML eXternal Entity" and is a term that refers to malicious entities within XML files. XXE attacks are a type of injection attack which uses an external entity that masquerades as a legitimate part of the XML. They may be used by hackers to exploit vulnerabilities in applications and servers, or they may be used by attackers to take control of systems. A common example of this is when an attacker sends a string such as "
XXE attack scenario
There are a variety of ways an XXE attack may be committed. Jenkins is most vulnerable to XXE attacks when it is processing untrusted inputs, such as XML configuration files, or when it is configured to handle untrusted inputs by default.
XXE Detection
Jenkins is able to detect if a file contains XXE inside of it. It does this by running a regular expression on the input to see if it matches some known or expected pattern that could be indicative of an XXE attack. If Jenkins detects that the file is an XXE attack, it will not process the file.
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/22/2022 02:19:00 UTC