This allows attackers to inject arbitrary code into a vulnerable installation of Jenkins. This might lead to remote code execution as well as information disclosure. Jenkins is a popular tool for building and deploying software. It is widely used in the software industry for continuous integration and deployment. Additionally, Jenkins is often used to host public projects on websites. In order to facilitate this, Jenkins provides mechanisms for enabling public access to the software it builds. This might be done by enabling a web-hosting service, exposing a project on a public Git repository, or enabling public access to a project through a web interface. In any of these cases, user credentials might be stored in Jenkins, which might allow an attacker to gain access to the project if the user has access to the project.
Mitigation Strategies:
You can take the following steps to help mitigate CVE-2022-43435:
1. Enforce authentication and authorization with your Jenkins server
2. Restrict access to Jenkins
3. Implement additional, outside security measures for your projects hosted on Jenkins
4. Use other tools that provide better defense in depth
Vulnerable code example
The following code can be found in the Jenkinsfile of a public project:
import com.atlassian.jira.config.PropertiesManager;
import com.atlassian.jira.config.PropertySet;
import com.atlassian.jira.plugin.PluginContextManager;
import jenkinsci-plugins.*;
public class PluginContextManager extends PluginContextManagerBase {
public static void addPlugin(final PluginContext plugin, final PropertySet properties)
throws Exception{ PropertiesManager propertiesMgr = new PropertiesManager(); propertiesMgr .getProperties() .put("mykey", ""); plugin .setProperty("mykey",propertiesMgr) ;}
}
Hackers can gain access to your Jenkins with a stolen password
There are many potential ways for hackers to gain access to Jenkins. The most obvious is if the user has their password stolen. If a hacker has access to the user’s password, they can then use that password to log in and gain access to the project. This will allow them to view any files, configure Jenkins, and much more.
Another way in which hackers can gain access is when an attacker compromises a vulnerable installation of Jenkins and makes it public. Using this method, an attacker might run scripts on their own website or server that can be used to check for the existence of Jenkins, revealing its IP address if found. If this happens, attackers could then use a brute force mechanism with tools such as Nikto or Nessus to find security vulnerabilities in Jenkins and exploit those vulnerabilities.
The important thing here is that no matter how hackers might get into your project, they will have full control over it and will be able to view any information stored within it. They might even be able to change any configurations of the software Jenkins was creating in order to compromise a different project built by the same user through another vulnerability later on down the line.
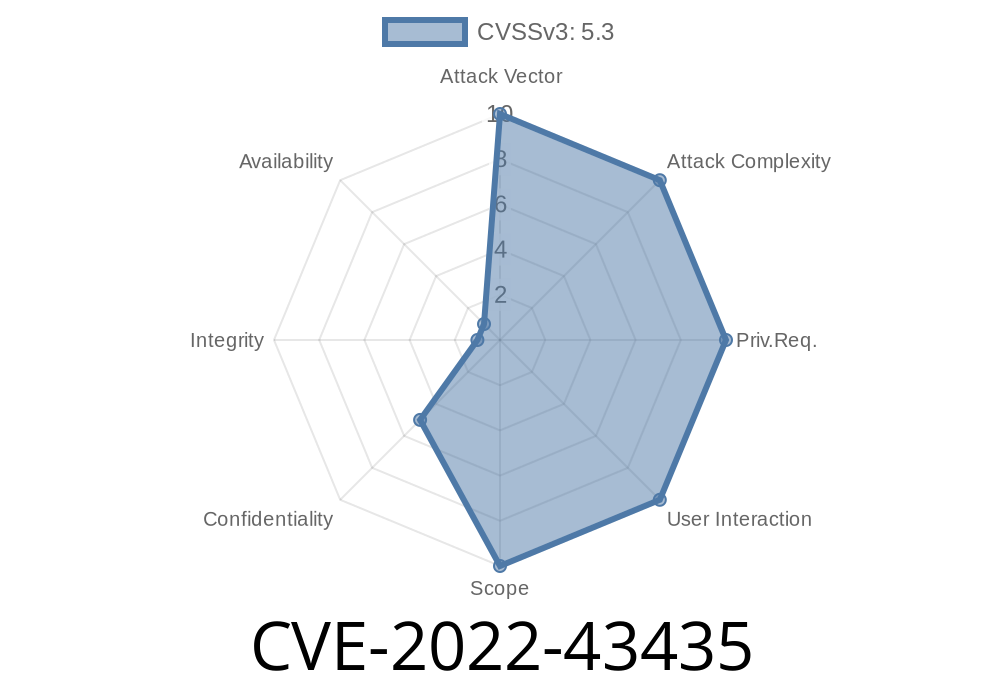
Vulnerability summary
A remote code execution vulnerability has been discovered in Jenkins. This allows attackers to inject arbitrary code into a vulnerable installation of Jenkins. This might lead to remote code execution as well as information disclosure.
Timeline
Published on: 10/19/2022 16:15:00 UTC
Last modified on: 10/24/2022 13:57:00 UTC