communication. This can be leveraged to control the functionality of the device and obtain sensitive information. Delta Electronics DIAEnergie version 1.9.02.001 and earlier contains a SQL injection vulnerability in the HandlerTag_kID handler that allows attackers to inject SQL commands into the device. This can be leveraged to control the functionality of the device and obtain sensitive information. Delta Electronics DIAEnergie version 1.9.02.001 and earlier contains a SQL injection vulnerability in the HandlerTag_kID handler that allows attackers to inject SQL commands into the device. This can be leveraged to control the functionality of the device and obtain sensitive information. In order to exploit this issue, an attacker must be in the local network and be able to craft a malicious packet. An attacker can leverage this issue to inject SQL queries into the device. An attacker can leverage this issue to inject SQL queries into the device. Workarounds Delta Electronics has confirmed the fix for this issue and released version 1.9.02.002 of DIAEnergie. Users are advised to update to the latest version.
Delta Electronics DIAEnergie SQL Injection Vulnerability
Delta Electronics DIAEnergie version 1.9.02.001 and earlier contains a SQL injection vulnerability in the HandlerTag_kID handler that allows attackers to inject SQL commands into the device. This can be leveraged to control the functionality of the device and obtain sensitive information. Delta Electronics DIAEnergie version 1.9.02.001 and earlier contains a SQL injection vulnerability in the HandlerTag_kID handler that allows attackers to inject SQL commands into the device. This can be leveraged to control the functionality of the device and obtain sensitive information. In order to exploit this issue, an attacker must be in the local network and be able to craft a malicious packet. An attacker can leverage this issue to inject SQL queries into the device. An attacker can leverage this issue to inject SQL queries into the device. Workarounds Delta Electronics has confirmed the fix for this issue and released version 1.9.02.002 of DIAEnergie...
Delta Electronics DIAEnergie version 1.9.02.001 and earlier contains a SQL injection vulnerability in the HandlerTag_kID handler that allows attackers to inject SQL commands into the device, which could allow them take over function or access sensitive data on it by replicating command execution via malicious packets uploaded through UDP ports 161, 443, 445, or 553 on port 161 TCP/UDP port number 161 (ICMP).
Delta Electronics DIAEnergie vulnerability
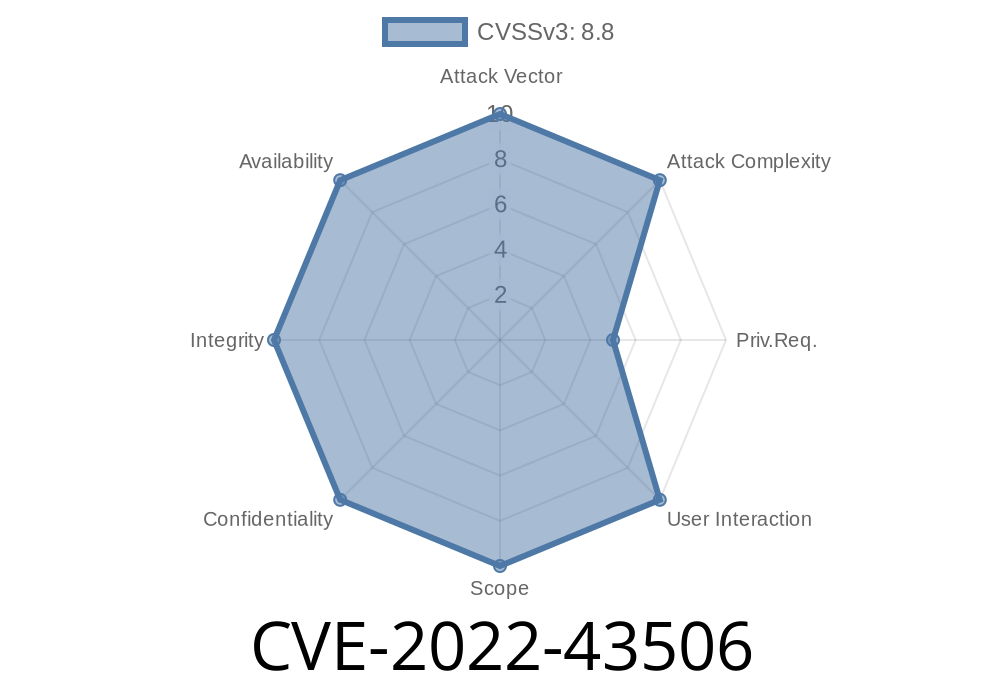
CVE-2022-43506: Delta Electronics DIAEnergie version 1.9.02.001 and earlier contains a SQL injection vulnerability in the HandlerTag_kID handler that allows attackers to inject SQL commands into the device. This can be leveraged to control the functionality of the device and obtain sensitive information. Delta Electronics DIAEnergie version 1.9.02.001 and earlier contains a SQL injection vulnerability in the HandlerTag_kID handler that allows attackers to inject SQL commands into the device. This can be leveraged to control the functionality of the device and obtain sensitive information. In order to exploit this issue, an attacker must be in the local network and be able to craft a malicious packet. An attacker can leverage this issue to inject SQL queries into the device. In order to exploit this issue, an attacker must be in the local network and be able to craft a malicious packet. An attacker can leverage this issue to inject SQL queries into the device.
Delta Electronics DIAEnergie HTTP API Vulnerability
Delta Electronics DIAEnergie version 1.9.02.001 and earlier contains a SQL injection vulnerability in the HandlerTag_kID handler that allows attackers to inject SQL commands into the device. This can be leveraged to control the functionality of the device and obtain sensitive information. Delta Electronics DIAEnergie version 1.9.02.001 and earlier contains a SQL injection vulnerability in the HandlerTag_kID handler that allows attackers to inject SQL commands into the device. This can be leveraged to control the functionality of the device and obtain sensitive information. In order to exploit this issue, an attacker must be in the local network and be able to craft a malicious packet. An attacker can leverage this issue to inject SQL queries into the device which may include function calls or other actions within Delta Electronics DIAEnergie that can compromise its stability or cause harm if not mitigated correctly. An attacker could also leverage this issue to execute malicious code on behalf of a victim user running Delta Electronics DIAEnergie by injecting malicious code into their web browser while they are logged into their respective account on Delta Electronics DIAEnergie using a cookie vulnerability within Delta Electronics DIAEnergie's web application, which would then allow for full access to system resources, including files, passwords, etc., or exploits such as malware or phishing links could potentially be used against them.>>END>>
Timeline
Published on: 11/17/2022 23:15:00 UTC
Last modified on: 11/18/2022 19:17:00 UTC