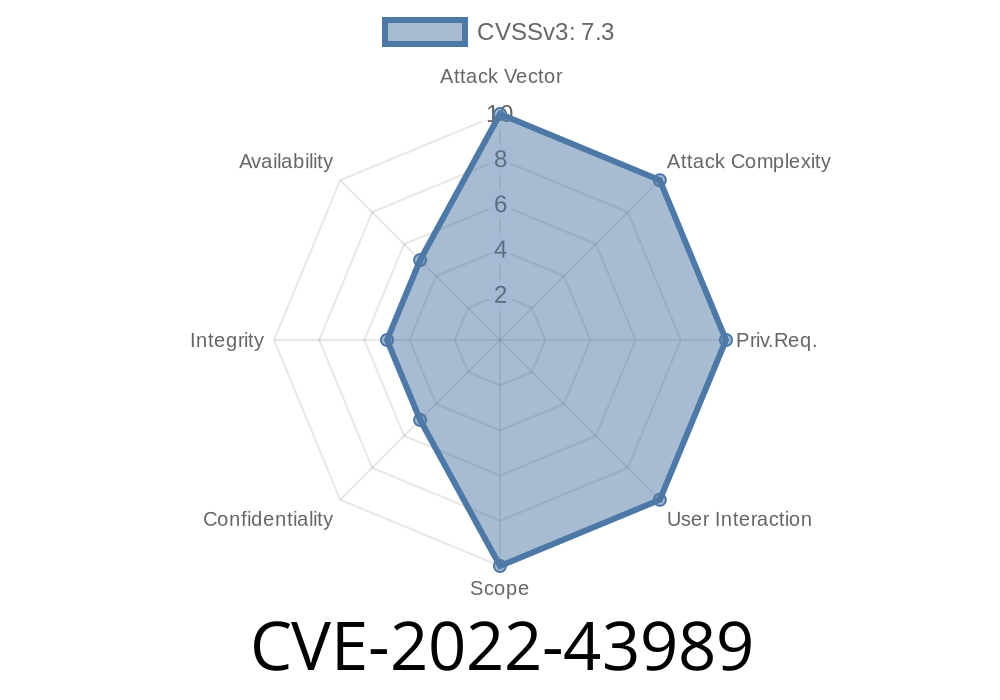
In late 2022, security researchers uncovered a critical flaw—CVE-2022-43989—in some SICK SIM2x00 industrial controllers (specifically, part numbers 1092673 and 1081902 running firmware versions less than 1.2.). This vulnerability allows remote, unprivileged attackers to abuse the password recovery mechanism and gain elevated access on the affected device.
If your organization uses the SICK SIM2x00 platform, it’s urgent to update your devices to firmware 1.2. or later to close this hole. In this post, we’ll break down what the vulnerability is, how it works, and what you should do about it.
The Vulnerability Explained
The SICK SIM2x00 controller is widely used in industrial automation. It has various user roles—for example, Operator, Service, Admin, etc.—and supports a built-in password recovery function meant to assist users who have forgotten their password.
Unfortunately, before version 1.2., the password recovery mechanism was flawed. It didn’t properly verify if a remote request was being made by a legitimate user or an attacker. This means anyone on the network—even without any user credentials or prior access—could invoke the recovery method to bump their privileges to the RecoverableUserLevel.
What does this mean?
An attacker can remotely trigger the recovery process, reset a password, and then log in as that user, immediately gaining more access and power. This impacts system confidentiality (private info could leak), integrity (settings could be changed), and availability (system could be tampered with or blocked).
> In short: a stranger could break in and act like a trusted user.
How the Exploit Works
Attackers can leverage the device’s API or web interface (depending on how your network is set up). Here is a simplified example mimicking the kind of request that could be made to trigger the password recovery:
import requests
# Target device configuration
TARGET_IP = '192.168..10'
RECOVERY_ENDPOINT = f'http://{TARGET_IP}/api/password-recovery';
USERNAME = 'target_user' # User whose level is RecoverableUserLevel
# Simulate recovery request
data = {
'username': USERNAME,
'action': 'start_recovery'
}
# No authentication required
resp = requests.post(RECOVERY_ENDPOINT, json=data)
if resp.status_code == 200:
print('Password recovery process triggered! Check recovery mechanisms for new credentials.')
else:
print('Failed to trigger recovery:', resp.text)
*The above is just a demo. The real exploit might differ, depending on how the controller exposes its management interfaces.*
Privilege escalation: The attacker’s level goes up to that of the RecoverableUserLevel.
- Remote, repeatable success: If network access exists (like in a poorly segmented factory or exposed system), this can be done as many times as needed.
Realistic Attack Scenario
Imagine a factory floor where the SICK SIM2x00 units are connected to the corporate network (a common but risky setup). An attacker—inside the building, or via a breached remote connection—could simply:
Reset and steal a password for a user with privileges
4. Log in as that user to change configurations, interfere with operations, or even brick the device
Repeat—nothing stops them from trying as much as they like. No special equipment needed. Just network access.
Firmware versions earlier than 1.2.
Newer firmware versions are protected against this attack.
Fixes & Recommendations
The only effective fix is to upgrade device firmware to 1.2. or higher. This update is available now via the official SICK Support Portal.
Steps
1. Visit: SICK Support Portal
References
- SICK Product Security Advisories: Official vendor advisories and patches
- MITRE CVE Record: CVE-2022-43989 entry
- ICS-CERT Advisory: Industrial control system alerts
- Exploit-DB: May contain proof-of-concept code (when public)
Conclusion
CVE-2022-43989 is a critical vulnerability in SICK SIM2x00 (ARM) controllers that exposes your industrial systems to easy and repeatable attacks by anyone with network access. The risk is straightforward: password recovery can be triggered by anyone, and attackers can instantly escalate their privilege.
Act now. Check your device models, update to firmware v1.2. or newer, and lock down network access if you cannot patch yet.
Have questions or need help with the update process?
Reach out to your local SICK representative, or check their support portal for detailed instructions.
Timeline
Published on: 11/01/2022 21:15:00 UTC
Last modified on: 03/31/2023 16:11:00 UTC