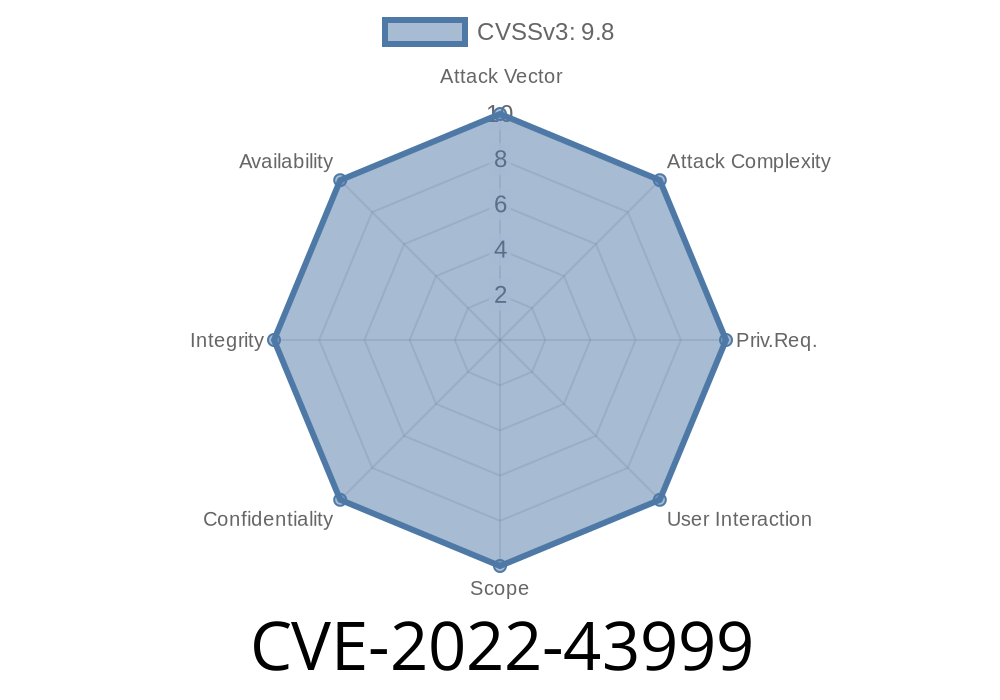
This vulnerability can be exploited by sending a specially crafted HTTP request. A remote attacker could send malicious requests to the targeted system, possibly intercepting user information or performing a phishing attack.
BACKCLICK Professional is not vulnerable to this issue in its default configuration. A user has to manually change the configuration to activate this security feature.
Another issue was found in BACKCLICK Professional 5.9.63. Remote attackers could execute arbitrary code on the server by sending a specially crafted HTTP request.
BACKCLICK Professional is not vulnerable to this issue in its default configuration. A user has to manually change the configuration to activate this security feature.
An unauthenticated attacker could send a specially crafted HTTP request to the targeted system. This malicious request could contain code which is executed on the server.
An issue was discovered in BACKCLICK Professional 5.9.63. Due to a memory leak, an attacker could cause a denial of service condition on the server.
BACKCLICK Professional is not vulnerable to this issue in its default configuration. A user has to manually change the configuration to activate this security feature.
Another issue was discovered in BACKCLICK Professional 5.9.63. Due to a memory leak, an attacker could cause a denial of service condition on the server.
BACKCLICK Professional is not vulnerable to this issue in its default configuration
What is BACKCLICK Professional?
BACKCLICK Professional is a software solution designed for organizations that deal with large volumes of customer data. With this solution, your company can have a secure and compliant way to collect customer data from multiple sources. It helps integrate your data into one centralized database and provides features such as automated pre-populated forms, multi-user support, advanced audit trails, and integration of third-party systems.
BACKCLICK Professional is not vulnerable to this issue in its default configuration. A user has to manually change the configuration to activate this security feature
Timeline
Published on: 11/16/2022 22:15:00 UTC
Last modified on: 11/21/2022 17:20:00 UTC