To exploit this issue, an attacker must be authenticated on the target system. A local user with administrator privileges can exploit this vulnerability by using the following procedure: First, send a maliciously crafted email message to the user. The user will receive the email message and execute the malicious code. The attacker can now send an email message with a link to a website. When the user clicks on the link, the attacker is now able to execute arbitrary system commands on the target system. It is recommended to review the source code of any applications that the user has access to. This can be done by using a program such as Notepad or another text editor. It is important to note that the source code is not required to be accessible via the Internet. The source code can be stored on the local hard drive of the user. It is also possible to access the source code via a local network.
Vulnerability Details
The vulnerability only requires a local user with administrator privileges to exploit. This vulnerability can be exploited by sending maliciously crafted email messages to the user of the vulnerable system.
It is recommended to review the source code of any applications that the user has access to. The source code can be stored on the local hard drive of the user or accessible via a local network.
To execute arbitrary system commands, an attacker must be authenticated on the target system.
Vulnerability Scenario
Recently, a new vulnerability was discovered in the Microsoft Outlook email client for Windows. A local user is able to exploit this vulnerability by sending an email message with a link to a website. The user will receive the email and execute the malicious code. The attacker can now send an email with a link to a website and the user will be able to execute arbitrary system commands on the target system.
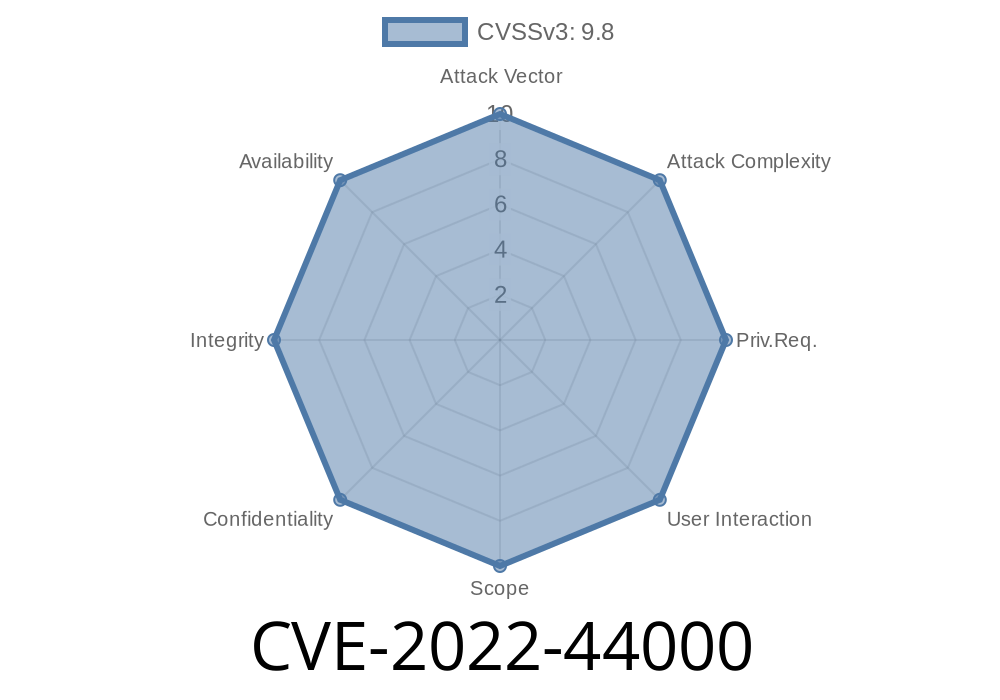
The vulnerability is CVE-2022-44000 which can be exploited by using Microsoft Outlook, Windows Mail, or any other mail application that uses the Microsoft Internet MIME API or Exchange ActiveSync protocol. This means many different types of computers can be vulnerable to this attack.
Microsoft Office Web Component CVE-2022-44001
To exploit this issue, an attacker must be authenticated on the target system. A local user with administrator privileges can exploit this vulnerability by using the following procedure: First, send a maliciously crafted email message to the user. The user will receive the email message and execute the malicious code. The attacker can now send an email message with a link to a website. When the user clicks on the link, Microsoft Office Web Component will download and execute arbitrary files from external sources without any notification to the end-user. It is recommended to review the source code of any applications that the user has access to. This can be done by using a program such as Notepad or another text editor. It is important to note that the source code is not required to be accessible via the Internet. The source code can be stored on the local hard drive of the user. It is also possible to access the source code via a local network
Vulnerability Discovery and Attack Scenario
A vulnerability in a system administration application has been discovered through a public disclosure. A malicious user will be able to exploit this issue by sending an email with an embedded link to the victim’s workstation. The user will then click on the linked and execute the malicious script associated with it. This can lead to compromise of the system or data stored on it. The source code of the application is not required to be accessible via internet for this attack to succeed. It can also be stored locally on the victim's machine.
Installation of Adobe Flash Player
To exploit this issue, an attacker must be authenticated on the target system. A local user with administrator privileges can exploit this vulnerability by using the following procedure: First, send a maliciously crafted email message to the user. The user will receive the email message and execute the malicious code. The attacker can now send an email message with a link to a website. When the user clicks on the link, the attacker is able to execute arbitrary system commands on the target system. It is recommended to review the source code of any applications that the user has access to. This can be done by using a program such as Notepad or another text editor. It is important to note that the source code is not required to be accessible via the Internet. The source code can be stored on etckeeper for Windows or SourceTree for Linux, macOS, or other Unix-based operating systems .
Timeline
Published on: 11/16/2022 23:15:00 UTC
Last modified on: 11/21/2022 17:36:00 UTC