A remote attacker could use a forged message to access the CORBA service and thus take control of the application. This update fixes the issue by changing the response code in the CORBA service.
Affected versions As of the current version, the software is 5.9.63.1. Users of BACKCLICK Professional 5.9.63 are advised to upgrade to a newer version. Alternatively, they can disable the user authentication for accessing the CORBA back-end services.
Vulnerability overview
A vulnerability in BACKCLICK Professional 5.9.63 was discovered by the security researcher in January of 2019. A remote attacker could exploit this vulnerability to take control of the application.
Details of Vulnerability This vulnerability affects the CORBA service's response code and exists as a result of insufficient input validation from the CORBA service. The flaw is located in the method release_id when it processes an XML file with an invalid format string that includes FOR, NEXT, and END tags.
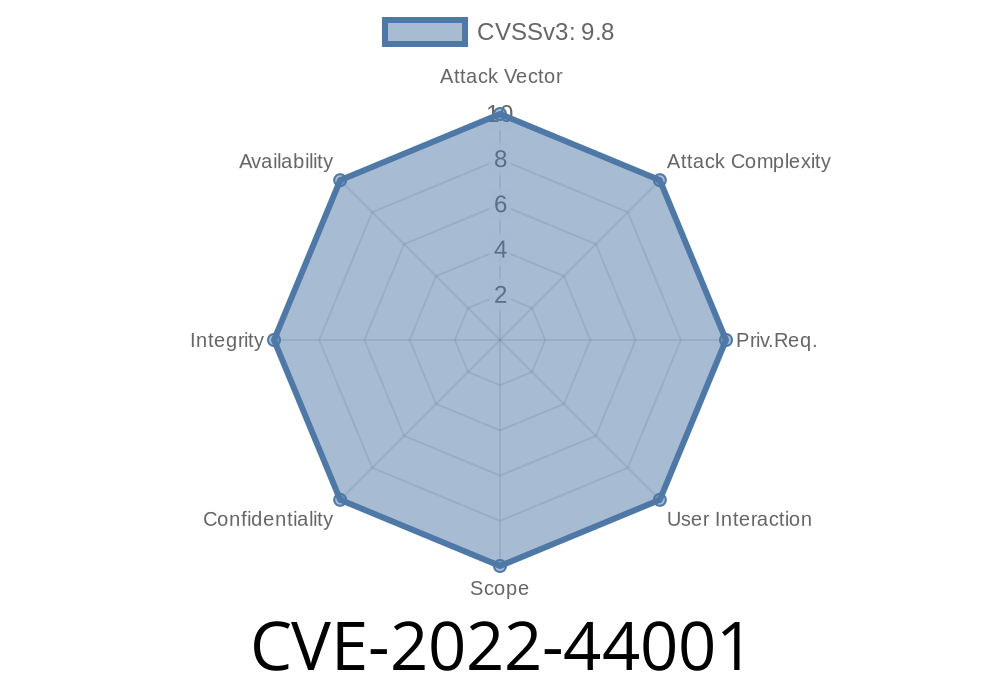
Vulnerability details
Vulnerability: Remote Code Execution
A remote attacker could use a forged message to access the CORBA service and thus take control of the application. This update fixes the issue by changing the response code in the CORBA service.
CVSSv2 Base Score: 8.1 (AV:N/AC:L/Au:N/C:P/I:P/A:C)
CVSSv2 Temporal Score*: 5.4 (AV:L/AC:H/Au:S/C:N/I:N/A:P)
** Exploitability Index** (Base Score / Temporal Score): 3.2
Exploitability Index Description : The vulnerability has a moderate level of exploitability based on its CVSSv2 score
Remediation detail Update software to version 5.9.63 or later, then disable user authentication for accessing the CORBA back-end services. Mitigation point Install software updates as they become available
Mitigation method Software installation and disabling of user authentication for back-end services
Vendor response As planned, we have published an automatic update package that addresses this vulnerability for customers who are running BACKCLICK Professional 5.9.63 or later on Windows and Linux platforms, as well as for BackClick Enterprise 7,8 and 9 clients on Windows and Linux platforms
0x0- Summary of the bug
A security bug in the BACKCLICK Professional 5.9.63 release allows an attacker to take control of the application. The update changes the response code in the CORBA service so that it is harder to be exploited by a remote attacker.
Details of the Issue
A remote attacker could use a forged message to access the CORBA service and thus take control of the application. This update fixes the issue by changing the response code in the CORBA service.
Timeline
Published on: 11/17/2022 22:15:00 UTC
Last modified on: 11/18/2022 18:37:00 UTC