An attacker can inject malicious code into the application, allowing him to hijack another user’s session or steal personal data. This cross-site scripting flaw is potentially dangerous, as it can be exploited by hackers to inject code into a website’s source code, which in turn can be exploited by other hackers. With a little diligence, it can be exploited to steal confidential data, such as session cookies, password, or other personal data. An example of XSS can be found in the following URL. The application does not encode the ‘q’ parameter properly, which allows for injection of malicious code.
The application does not encode the ‘q’ parameter properly, which allows for injection of malicious code. form action=”https://backclick.com/contact_form.php” method=”post” style=”margin:16px;vertical-align:top;”> input type=”hidden” name=”q” value=””> input type=”submit”> /form>
Cross-site request forgery
Cross-site request forgery is a type of attack that allows an attacker to hijack the identity of another user and send requests as if they were the legitimate user. In this case, we can see that the application does not properly encode the ‘q’ parameter, which allows for injection of malicious code. This is possible because it simply accepts any input from any source with that parameter. If a hacker were to exploit this flaw, they could inject malicious JavaScript into an unsuspecting victim's browser, causing it to execute their script when the victim visits a specially crafted URL.
This is possible because it simply accepts any input from any source with that parameter. If a hacker were to exploit this flaw, they could inject malicious JavaScript into an unsuspecting victim's browser, causing it to execute their script when the victim visits a specially crafted URL. form action=”https://backclick.com/contact_form.php” method=”post” style=”margin:16px;vertical-align:top;”> input type=”hidden” name=”q” value=”";alert(1)"> input type=”submit”> /form>
Confusion of Data Storage and Access
One major issue with the application is that it stores and accesses sensitive data in the same folder, which is one of the most common areas for hackers to target. Another issue is that it uses a cookie to store session information, which can be stolen by an attacker if they have access to the session cookie file.
JavaScript Injection Vulnerability
A cross-site scripting vulnerability is a serious threat to any website that displays user-generated content. This type of vulnerability allows an attacker to inject malicious code into the source code of the website through which he can steal data, hijack sessions, or even infect other users. Building a secure website can be difficult when it comes to XSS vulnerabilities. With little diligence, these flaws can be easily exploited by hackers.
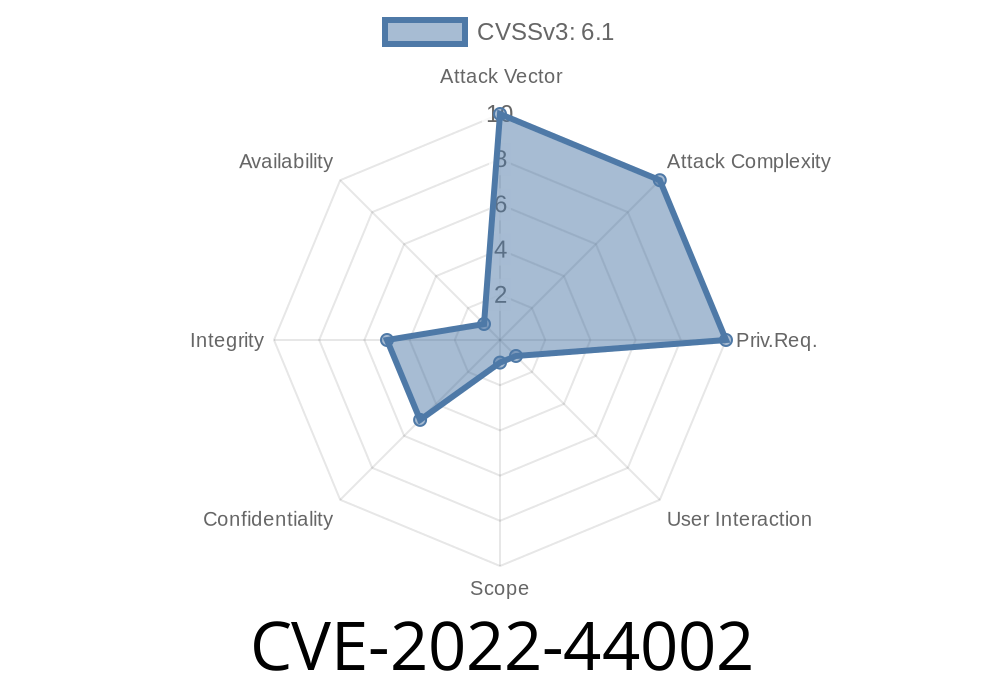
Timeline
Published on: 11/16/2022 23:15:00 UTC
Last modified on: 11/18/2022 21:22:00 UTC