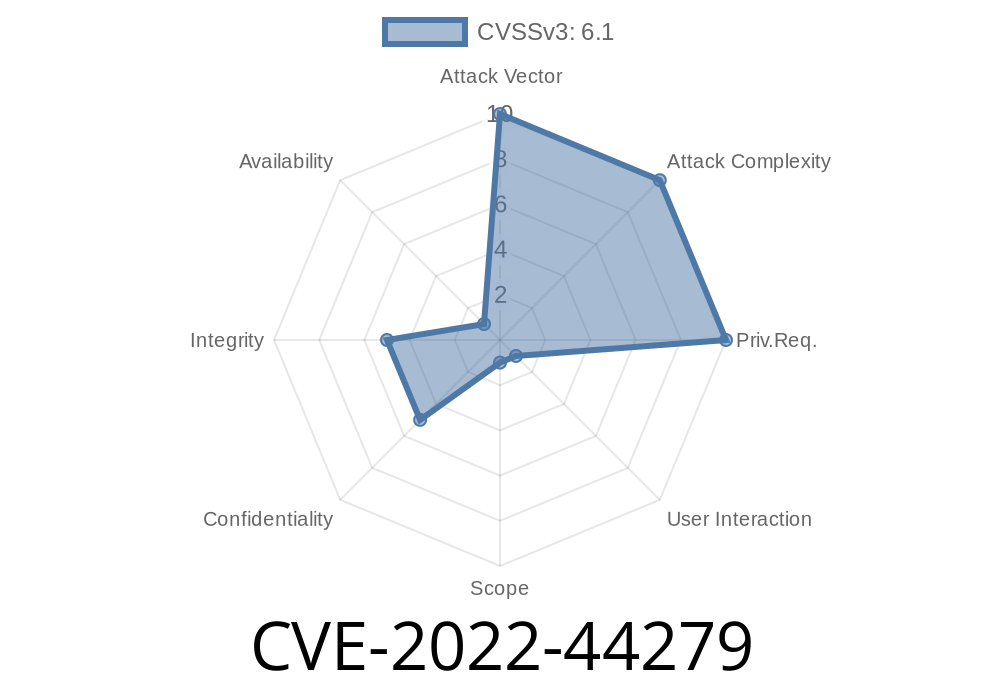
Garage Management System (GMS) is a popular open-source software used by many small auto repair shops to manage daily operations. In late 2022, CVE-2022-44279 was assigned to a Cross-Site Scripting (XSS) vulnerability present in version 1. of this system. This article dives into what the vulnerability is, how it can be exploited, and what you can do to protect your garage and your users.
What is CVE-2022-44279?
CVE-2022-44279 is a Stored XSS vulnerability that exists in Garage Management System v1.. The vulnerability is found in the createBrand.php script located at /garage/php_action/. It lets an attacker inject malicious JavaScript code, which is then stored and executed for other users—potentially leading to session hijacking, data theft, or site defacement.
Why is this Important?
Stored XSS means the attack can persist — once injected, it can affect every user who views the affected page. This could compromise trust, expose customer data, and disrupt business operations in your garage.
How Does the Exploit Work?
The vulnerable endpoint, /garage/php_action/createBrand.php, handles the creation of vehicle brands. It takes user input from a form (like the brand name) but doesn't properly sanitize or escape what users submit. This allows an attacker to submit a brand name containing JavaScript code. That code will then run every time someone else views the brands listing, or in the relevant management dialogs.
`html
alert('XSS Exploit!')
Here's a simplified version of what the vulnerable code might look like inside createBrand.php
<?php
// ...assume connection and authentication handled here
$brandName = $_POST['brandName']; // No sanitization!
$sql = "INSERT INTO brands (brand_name) VALUES ('$brandName')";
mysqli_query($conn, $sql);
?>
Notice the lack of sanitization or escaping — this is what allows XSS.
`html
alert('Gotcha!')
Submit the form.
Now, when anyone loads the brands page, that JavaScript will run. The attacker can do more than just show an alert; they can steal cookies, redirect users, or deface the site.
Video Demonstration
*Not available in this article, but you can try the proof of concept above on a test instance of Garage Management System.*
Example Fix in PHP
$brandName = htmlspecialchars($_POST['brandName'], ENT_QUOTES, 'UTF-8');
$sql = "INSERT INTO brands (brand_name) VALUES ('$brandName')";
mysqli_query($conn, $sql);
Alternatively, use parameterized queries and output encoding
$stmt = $conn->prepare("INSERT INTO brands (brand_name) VALUES (?)");
$stmt->bind_param("s", $_POST['brandName']);
$stmt->execute();
And always escape when displaying content
echo htmlspecialchars($brandName, ENT_QUOTES, 'UTF-8');
References and Further Reading
- Exploit Database - Garage Management System v1. Stored XSS
- CVE Details for CVE-2022-44279
- OWASP XSS Prevention Cheat Sheet
- Garage Management System on SourceForge
Conclusion
CVE-2022-44279 is a textbook example of why input validation and output escaping matter, even in small business web apps like Garage Management System. If you're running GMS v1., patch your code, sanitize input, and always keep your systems up to date. Don’t wait for an attacker to demonstrate what you can prevent today.
Timeline
Published on: 11/29/2022 20:15:00 UTC
Last modified on: 12/01/2022 20:12:00 UTC