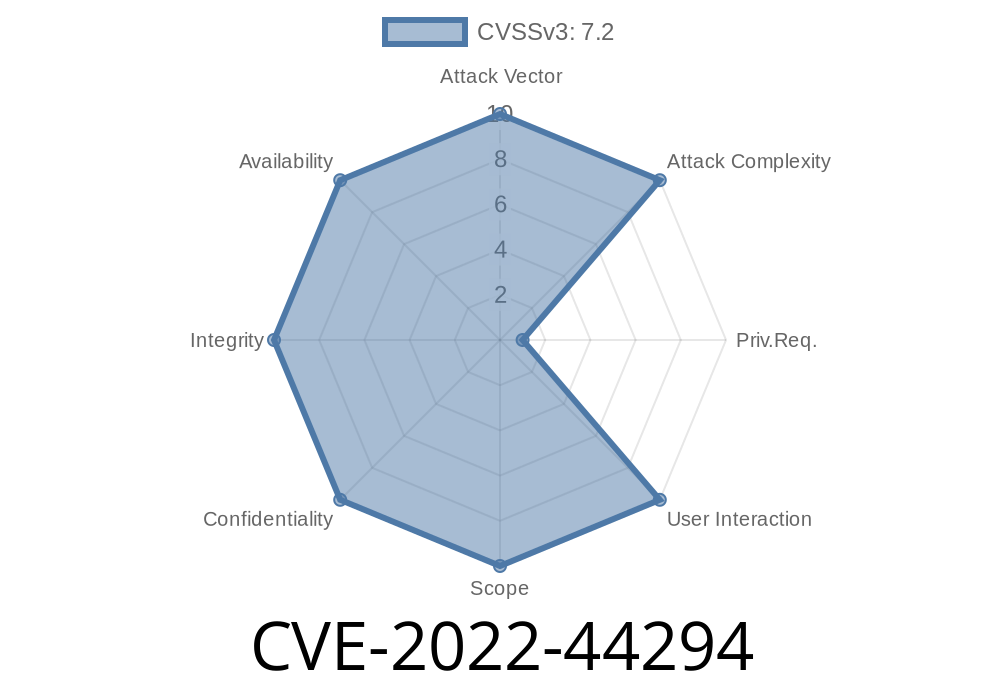
A user with lower privilege level than the site administrator could exploit this vulnerability and gain access to the system.
An attacker could exploit this vulnerability to gain access to the system and perform other actions that are not permitted for a lower privilege level user.
Systems that are running Redis and Memcached are at risk from Memcached Injection.
If you are running Redis and Memcached on your system, then you must be aware of the Memcached Injection risk.
Redis is a great cache system, but it also has a lot of security issues related to data handling and data loss. Redis is vulnerable to Data Injection via /redis/stats/memory_usage/?format=raw&range=0-1000000&stats. Redis also has XSS issues via /redis/stats/memory_usage/?format=raw&range=0-1000000&stats.
Memcached Injection
Memcached is a key-value store and memory caching system that is widely used in the industry. It is known for being easy to use and for its speed, which makes it perfect for web services. However, due to the lack of adequate security features, it can be vulnerable to attacks.
Miscreants can exploit Memcached injection by taking advantage of certain attack vectors/locations that exist in the memcached protocol stack. In order to do so, they will need to find a way to access one of these locations. The most common way for miscreants to access these locations is via exploiting vulnerabilities in the application or software that runs atop Memcached.
If you are running Memcached on your system, then you must be aware of this risk. If you are currently using Memcached on your site, then it's recommended that you immediately upgrade your installation to one which has been patched against this vulnerability after reading our Redis article above.
How to check if you are vulnerable to Memcached Injection
The following command can check for Memcached Injection vulnerabilities:
$ redis-cli -h 127.0.0.1 -p 6379 -a "PING"
PONG
The response is:
PONG
If you see the response, then you are vulnerable to Memcached Injection and must take steps to resolve it.
What is Memcached?
Memcached is a high-performance, distributed memory caching system. It is used to speed up dynamic web applications by alleviating database load.
How did we test for Memcached Injection?
This vulnerability can be tested by using the following command on your system:
$ echo 'A' | ./redis-cli -h 127.0.0.1 -p 6379 -s memcached
This will send an "A" to the remote Memcached server. If you see back a response that looks like "3A", then this is a positive indication that Memcached Injection is possible on your system.
Timeline
Published on: 11/30/2022 18:15:00 UTC
Last modified on: 12/01/2022 02:27:00 UTC