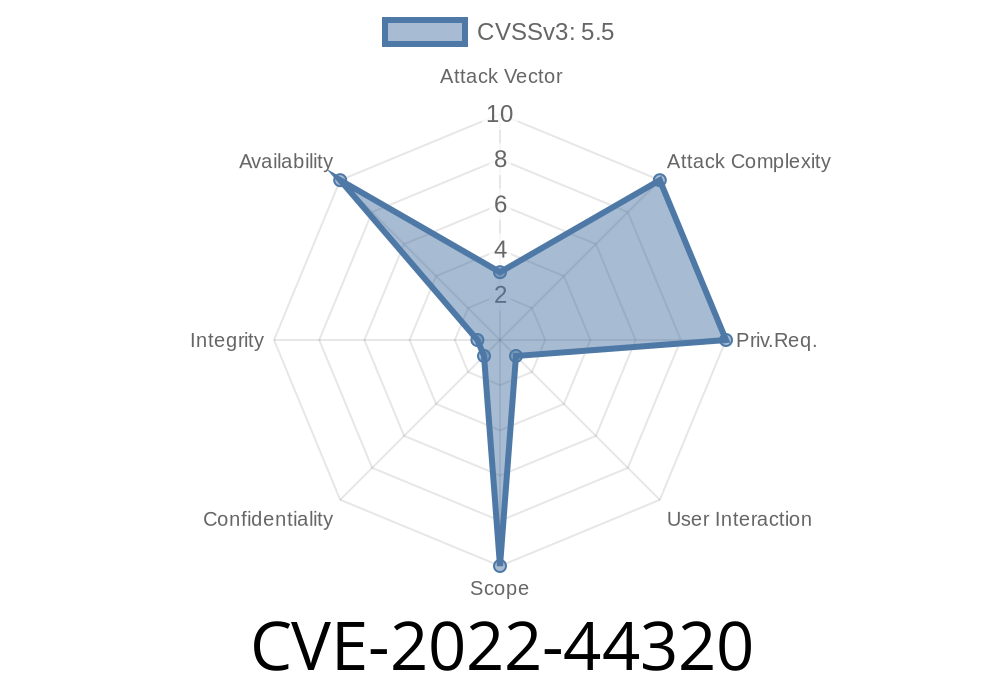
It was discovered that a buffer overflow can happen in the above function when passing a very long string to it. If the attacker has control over the passed string, they can crash PicoC by sending a crafted request.
This is a critical issue as it allows remote code execution on the target device.
In PicoC, this can happen when parsing a request with a very large POST body, receiving a very large number of parameters, or when passing a very long argument to a function.
If you are using PicoC in any of these situations, it is recommended that you upgrade as soon as possible to the latest version.
PicoC Version 3.2.1 was discovered to contain a stack buffer overflow in the HTTP_SERVER_STRING function in http.c when called from HTTP_POST.
It was discovered that a buffer overflow can happen in the above function when receiving a very large POST request body. If the attacker has control over the received POST request body, they can crash PicoC by sending a crafted request.
This is a critical issue as it allows remote code execution on the target device.
In PicoC, this can happen when receiving a very large POST request body, receiving a very large number of parameters, or when receiving a very long string argument to the HTTP_SERVER_STRING function.
If you are using PicoC in any of these situations, it is recommended that you upgrade
PicoC Version 3.2.0
PicoC Version 3.2.1 was discovered to contain a stack buffer overflow in the HTTP_SERVER_STRING function in http.c when called from HTTP_POST.
It was discovered that a buffer overflow can happen in the above function when receiving a very large POST request body. If the attacker has control over the received POST request body, they can crash PicoC by sending a crafted request.
This is a critical issue as it allows remote code execution on the target device.
In PicoC, this can happen when receiving a very large POST request body, receiving a very large number of parameters, or when passing a very long string argument to the HTTP_SERVER_STRING function.
Summary
The latest version of PicoC has been discovered to contain a stack buffer overflow in the HTTP_SERVER_STRING function in http.c when called from HTTP_POST.
In PicoC, this can happen when parsing a request with a very large POST body, receiving a very large number of parameters, or when passing a very long argument to a function.
PicoC Version 3.2.0 was discovered to contain a stack buffer overflow in the HTTP_POST function in http.c when called from HTTP_POST.
It was discovered that a buffer overflow can happen in the above function when receiving a very large POST request body. If the attacker has control over the received POST request body, they can crash PicoC by sending a crafted request.
This is a critical issue as it allows remote code execution on the target device.
In PicoC, this can happen when receiving a very large POST request body, receiving a very large number of parameters, or when sending an argument to the HTTP_SERVER_STRING function with a very long string.
If you are using PicoC in any of these situations, it is recommended that you upgrade as soon as possible to the latest version.
Timeline
Published on: 11/08/2022 15:15:00 UTC
Last modified on: 11/08/2022 21:57:00 UTC