This issue is rated as High severity due to the fact that it can be exploited remotely by an unauthenticated attacker. XSS flaws are usually exploited in two ways: injecting malicious scripts into a site to steal sensitive information or performing session hijacking attacks. In the first case, if a user visits a malicious site and accesses a script that is injected via XSS, it is possible that the script could be used to steal information from the user's session or to conduct other malicious activities. In the second case, if a user is redirected to another site via XSS and that site has a vulnerable script that can be exploited, a malicious user could potentially hijack the session of the user accessing that site. Most XSS issues can be easily prevented by using reliable approaches such as input validation and output escaping. However, since it is very difficult to completely eliminate all possible locations where XSS flaws can be exploited, you should take steps to prevent the issue from being exploited as much as possible.
Input Validation
One of the most reliable ways to prevent XSS is input validation. Input validation allows you to check whether the values entered by a user are valid and if they do not match what your application expects, it can stop the execution of that form submission. You should be aware of how many characters are allowed in a value or parameter as well as what type of data that value or parameter is expected to hold. Additionally, you should validate values based on whether they are case sensitive or not. This will ensure that malicious users cannot use a collision attack where they try to use two different values with similar names while expecting different results.
Input validation
Input validation is an approach that can be used to prevent XSS flaws from being exploited. Input validation prevents user input from being processed by a browser in unsafe ways. For example, when a user enters data into a form field on a website, they could inject malicious scripts through the input field and collect sensitive information or perform other malicious activities. If the input is validated, the script would not have access to the form field and would not be able to steal any sensitive information. In order for input validation to work properly, it is essential that you validate user input in all appropriate locations where proper validation is required.
References:
- https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet
- https://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)
Protecting Against XSS Attacks
To prevent XSS vulnerabilities from being exploited, you should take precautions in the following ways:
- Restrict which scripts are allowed to be executed on your website.
- Use input validation and output escaping techniques to ensure that only trusted data can be processed by your website.
- Use a library or framework that provides built-in protection against XSS attacks.
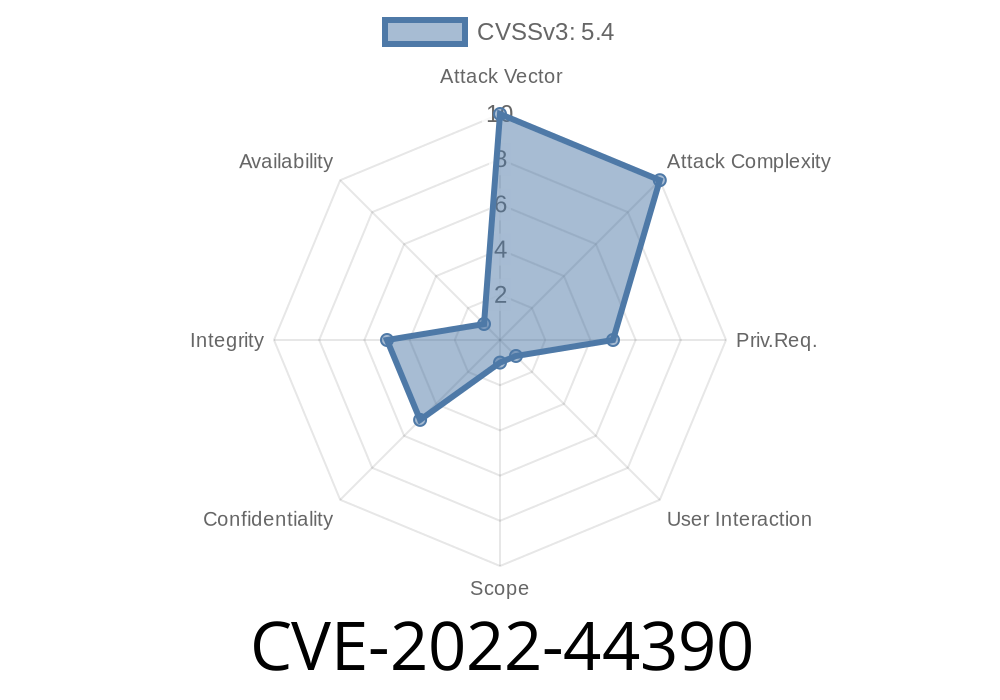
Description of the issue
In this issue, there is a vulnerability in the CoderPad CMS (CVE-2022-44390) that can be exploited by an unauthenticated attacker. CoderPad has been vulnerable to XSS attacks since March 2014 and is still vulnerable today. The vulnerability allows an unauthenticated attacker to inject arbitrary web script or HTML into the victim's browser. This can allow the attacker to trick victims into revealing sensitive information or perform session hijacking attacks on them.
The vulnerability occurs in AdminCPAdmin/site/settings/site_settings.php when it displays the page via AJAX, but instead of displaying "page" as a parameter, it displays "script". This allows a user to access arbitrary web script which can then be used to steal sensitive information or perform session hijacking attacks on them.
Timeline
Published on: 11/14/2022 20:15:00 UTC
Last modified on: 11/16/2022 19:48:00 UTC