Published: June 2024
*By: Infosec Journal Exclusive Writer*
Introduction
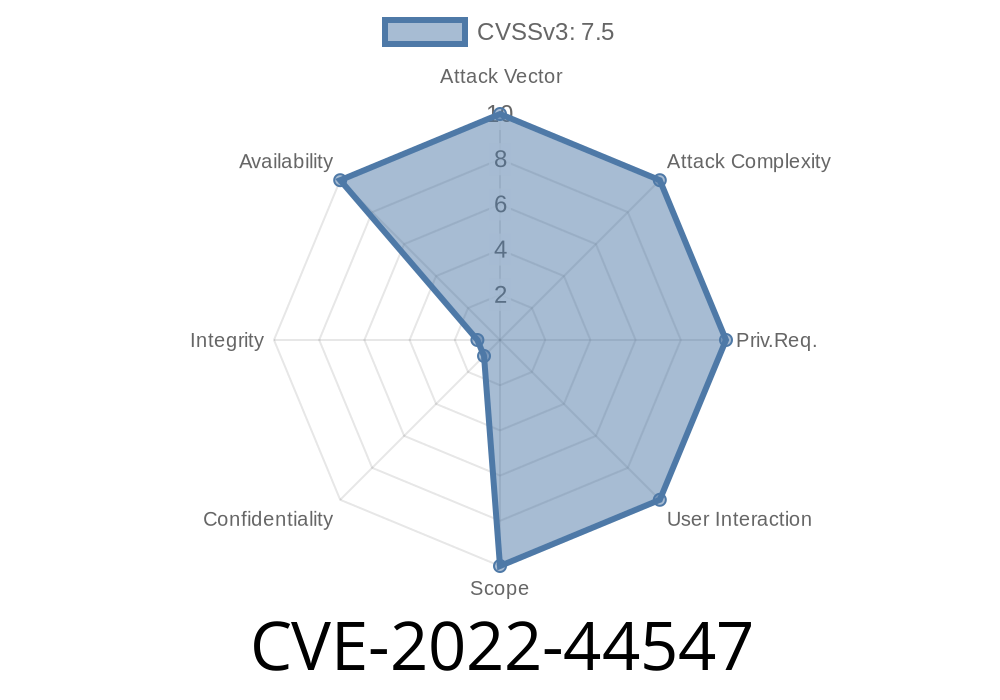
A significant vulnerability was discovered and tracked as CVE-2022-44547 in the Display Service module, exposing systems to a potentially dangerous Use-After-Free (UAF) condition. If exploited, it can impact the availability (and possibly integrity) of the display service, leading to crashes or unexpected behavior.
In this post, we'll break down the vulnerability in simple language, offer code snippets for understanding, link to original references, and explain how attackers could abuse it.
What is a Use-After-Free (UAF)?
A Use-After-Free (UAF) is a class of memory corruption bugs where the application continues to use a portion of memory after it has been "freed" (deallocated). This memory area may now contain unexpected or even attacker-controlled data.
Imagine renting a house, moving out, and someone else rents it, but you still have the keys—you could cause problems for the new resident! That's the idea behind UAF.
Affected Component: Display Service Module
The vulnerability exists in the Display Service—responsible for handling window rendering and screen content in affected systems. Due to a logic error, it's possible to access an object after it has been freed, especially when processing certain display update requests.
Vulnerability Details
- CVE: CVE-2022-44547
Type: Use-After-Free
- Impact: Can cause the Display Service to crash (denial of service), or potentially arbitrary code execution.
- Affected versions: See this vendor advisory or your system documentation (Example: Huawei devices running specific versions of HarmonyOS and EMUI)
- Attack Vectors: Local or remote (varies by implementation), typically requires ability to send crafted display requests.
Example Vulnerable Code Path
*(simplified for illustration; based on patterns in public advisories)*
Suppose the Display Service manages client sessions with a routine like this
void handle_display_request(Client *client) {
DisplayBuffer *buf = get_display_buffer(client);
free(buf); // Buffer is freed
// ... some code
update_display(buf); // UAF: buf pointer was already freed!
}
Sends crafted requests that trigger an object to be freed, but later reused.
3. Allocates new data (e.g., via other features) into the same memory spot to inject controlled content.
*(Illustration, not a working exploit)*
# Pseudocode - exploiting UAF via Python socket
import socket
def trigger_uaf():
s = socket.socket()
s.connect(('localhost', 11111))
s.send(b'TRIGGER_FREE') # Cause the buffer to be freed.
s.send(b'ALLOCATE_NEW') # Fill that memory with attacker content.
s.send(b'USE_AFTER_FREE') # Make service use the freed, now attacker-controlled, memory.
print(s.recv(1024)) # Service may crash or behave abnormally
Note: Actual exploitability (including remote code execution) depends on memory protections on the target (like ASLR or DEP/NX). But denial-of-service (crash) is almost always possible.
Security Impacts
- Denial of Service (DoS): Main risk. Display Service crashes, interrupting user interface functionality. On critical systems, this could mean system downtime or lockout.
- Arbitrary Code Execution: In some configurations, an attacker who can carefully control the heap may execute malicious code—although this is more advanced and depends on mitigations.
Official References & Mitigation
- NVD Details CVE-2022-44547
- Huawei Security Advisory (example)
- Mitre CVE Record
Fix: Upgrade your system or device to an updated version as advised by your vendor. Patch timelines may vary—check with your official support channels.
Conclusion
CVE-2022-44547 is a classic use-after-free bug that can threaten the reliability and security of affected devices. Keeping systems up-to-date and following minimum exposure principles is the best defense.
Stay tuned to trusted vendor advisories and security bulletins to ensure you’re protected.
*Do you work with affected systems or wish to report similar bugs? Share your experience below.*
Timeline
Published on: 11/09/2022 21:15:00 UTC
Last modified on: 11/10/2022 13:50:00 UTC