To achieve this, an attacker can trick users into installing a malicious plugin. Once a malicious plugin has been installed, an attacker can then send a request to the plugin with a specially crafted request that can cause arbitrary file deletion in the server. The plugin will then handle the request, delete the file, and send the information back to the attacker. This means that instead of the file being deleted by WatchTowerHQ, the plugin will handle the deletion and send the information back to the attacker. WatchTowerHQ is a WordPress plugin that is used to manage the settings of WatchTower, a WordPress hosting company. Unauthorised file deletion in WatchTowerHQ can result in a permanent loss of data on the server.
Discovery & Vulnerability Assessment:
Discovered by:
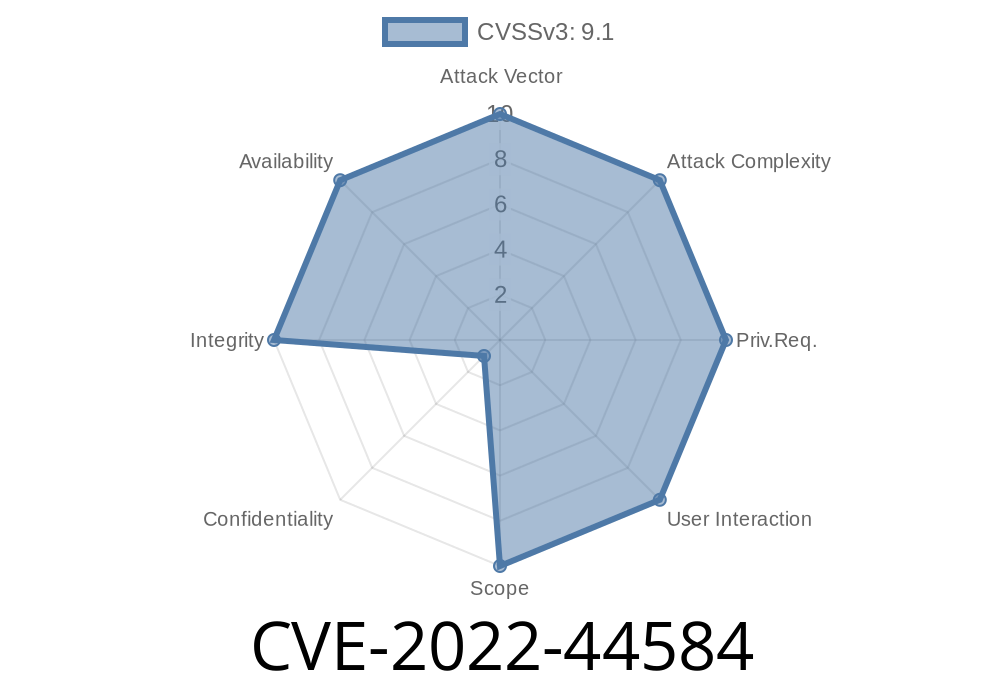
CVE-2022-44584
Vulnerability Description:
An attacker can trick users into installing a malicious plugin. Once a malicious plugin has been installed, an attacker can then send a request to the plugin with a specially crafted request that can cause arbitrary file deletion in the server. The plugin will then handle the request, delete the file, and send the information back to the attacker. This means that instead of the file being deleted by WatchTowerHQ, the plugin will handle the deletion and send the information back to the attacker. WatchTowerHQ is a WordPress plugin that is used to manage settings of WatchTower, a WordPress hosting company. Unauthorised file deletion in WatchTowerHQ may result in permanent loss of data on server.
References: -https://www.nytimes.com/2019/01/27/business/watchtower-hq-wordpress-plugin.html
The New York Times is reporting that a WordPress plugin has been found to have vulnerabilities that allow an attacker to delete files on the server without permission from WatchTowerHQ, a website managed by WatchTowerHQ. This vulnerability would allow an attacker to cause arbitrary file deletion in the server because WatchTowerHQ is handling the deletion instead of being able to delete it themselves.
Timeline
Published on: 11/18/2022 23:15:00 UTC
Last modified on: 11/21/2022 19:34:00 UTC