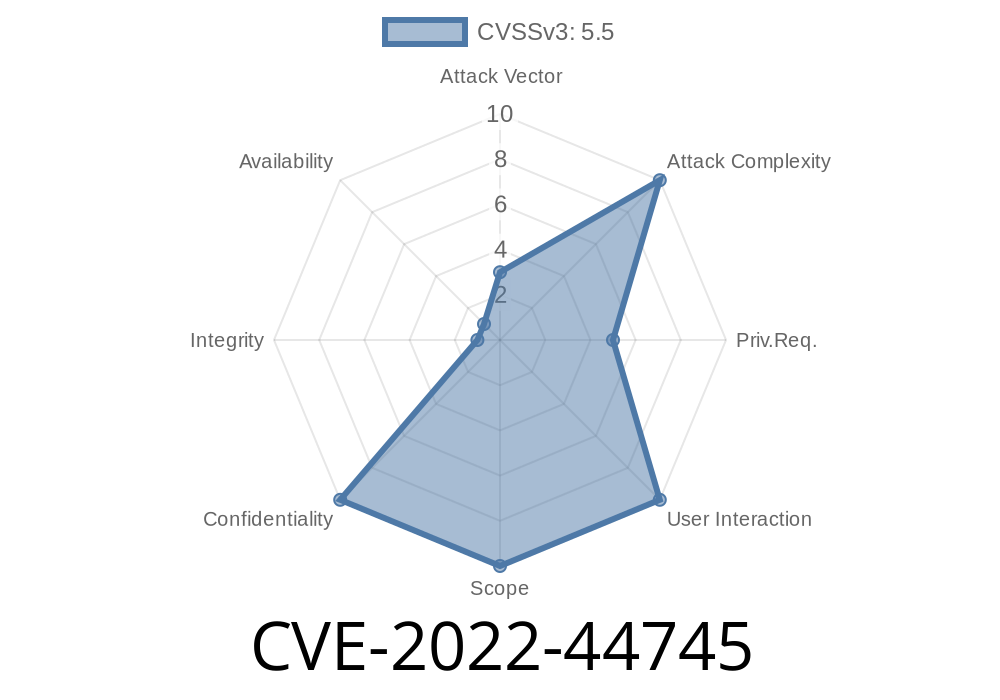
In November 2022, a security vulnerability was disclosed under the identifier CVE-2022-44745, impacting earlier versions of Acronis Cyber Protect Home Office (formerly Acronis True Image). The security flaw allowed sensitive user information to leak unintentionally through the application’s log files. This post breaks down what the vulnerability means, how attackers could exploit it, snippets of how the leak happens, and what steps users and administrators should take.
Affected Versions:
Acronis Cyber Protect Home Office (Windows) before build 40107
What Is the Problem?
Many backup and cyber-protection tools generate log files to help diagnose errors, monitor system status, and provide traceability. However, improper handling of these logs can lead to the unintentional exposure of sensitive data.
CVE-2022-44745 is an example of this: before build 40107, Acronis Cyber Protect Home Office’s logging mechanism sometimes wrote sensitive information—like authentication tokens, network credentials, backup target addresses, or even file paths containing personal data—into easily accessible log files.
Where Are These Log Files?
Typically, Acronis stores logs in directories like:
C:\ProgramData\Acronis\TrueImageHome\Logs\
or
C:\ProgramData\Acronis\CyberProtectHomeOffice\Logs\
These logs are readable by any user or process with local access. On shared or multi-user systems, this increases the risk of sensitive data exposure.
Technical Details & Exploit Scenario
Attackers do not need remote code execution or administrator privileges. If they can access the local file system—either as a regular user or via malware—they could read these log files and harvest sensitive data.
How the Leak Might Look in Real Logs
Below is a simplified example of a vulnerable log file entry (from a fictitious session, but similar to what could be found in pre-40107 builds):
2022-10-23 14:21:05 [INFO] Backup started to \\NAS-DEVICE\Backups\JohnDoe\ with credentials: user=john, password=Summer2022!
2022-10-23 14:21:08 [DEBUG] Connected to service token: 5e8f9a3b37263bf34e312b5f5adf4eaa
Plaintext credentials (user=john, password=Summer2022!) are visible.
- Service token (used for remote access/API) is in clear, not hashed or masked.
Stealing network credentials:
The attacker now has user/password pairs and can access network shares or backup storage.
Using tokens or other secrets:
If a leaked authentication token is valid, it could be used to impersonate the user in the Acronis environment.
Why Does It Matter?
- Sensitive credential leakage: Unintended parties can access backups, remote services, and possibly other sensitive infrastructure.
- GDPR/Data protection concerns: Personal/user data appearing in logs can have regulatory implications.
- Elevation for malware: Malware that runs as a basic user doesn’t need to escalate privilege; it just reads the logs and uses found secrets.
Upgrading and Mitigating
If you're running Acronis Cyber Protect Home Office (Windows), upgrade to at least build 40107 or later—Acronis’s official advisory and download page provides the fixed builds.
Short-term advice
1. Restrict log access: Ensure only trusted admin users can read log files (C:\ProgramData\Acronis\...).
References
- Original CVE: https://nvd.nist.gov/vuln/detail/CVE-2022-44745
- Acronis Advisory: https://kb.acronis.com/content/71961
- Security Research Community Writeup: https://secuniaresearch.flexerasoftware.com/advisories/61741/
Closing Thoughts
CVE-2022-44745 is a classic example of how even well-designed security software can create risks if operational details—like logging—aren’t carefully managed. Always keep backups and security software updated, and remember: what you log can be just as sensitive as what you back up!
If you’re unsure about your system’s status, check your Acronis build number and logs now—and consider upgrading as soon as possible.
Timeline
Published on: 11/07/2022 20:15:00 UTC
Last modified on: 11/08/2022 19:15:00 UTC