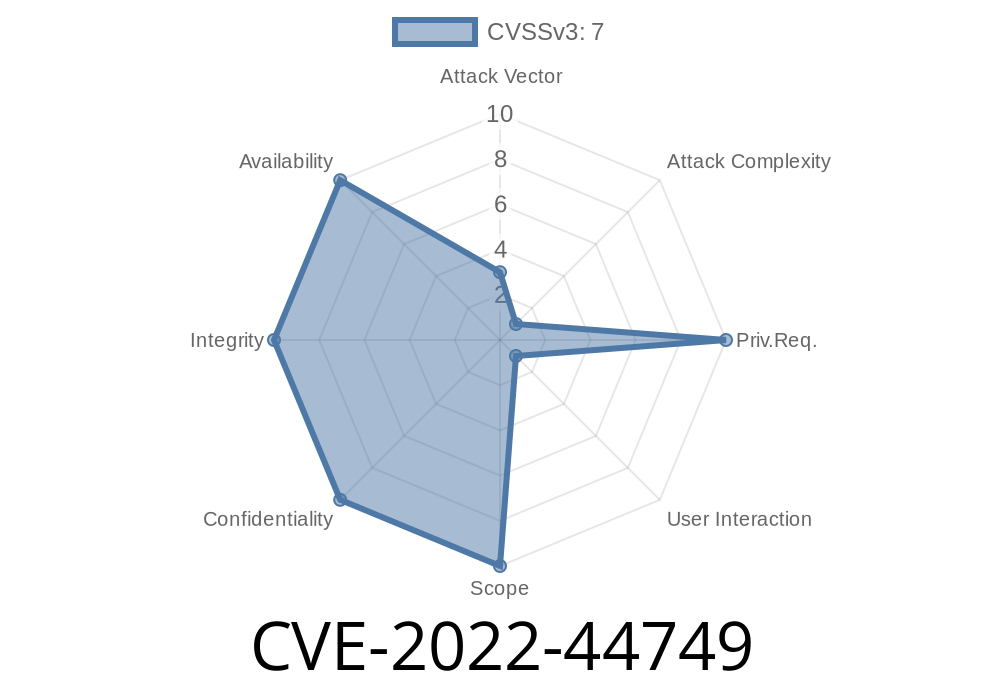
If you use the popular data tool KNIME Analytics Platform, you might have opened a workflow downloaded from the internet. What if simply opening such a file could over-write your system files, break your apps, or even run a hacker’s code? That’s exactly what CVE-2022-44749 is about—a serious zip extraction bug, quietly hiding in KNIME versions 3.2. and newer.
What Is CVE-2022-44749?
CVE-2022-44749 is a directory traversal vulnerability, also known under the popular nickname “Zip-Slip.” This flaw allows a specially crafted ZIP archive—like a KNIME workflow file—to overwrite files anywhere on your system, as long as you have write permission there.
> Key Point: You don’t have to _run_ any dangerous code. Just the act of opening a workflow can overwrite files!
This might not seem like much at first, but think: What files do you have write access to? What about your settings, documents, or even more dangerous, a script or executable you might run later?
Risk Level: High (can touch anything you have write access to)
- Exploitation: By importing/opening a malicious workflow file
The Zip-Slip Attack—How Does It Work?
Normally, when extracting files from a ZIP, the software should _not_ let any file end up outside the intended folder. But with this bug, a hacker can include file names like ../../../../Windows/system32/calc.exe, which sneak files into directories far, far away from your workflow folder.
Here’s how an attacker’s ZIP archive could look
evil_workflow.zip
├── workflow.knime
├── ../../../../Documents/secret.txt
└── ../../../../AppData/Local/KNIME/safe_script.bat
When you open this in KNIME, the code responsible for extracting the workflow doesn’t sanitize these “tricky” paths. Suddenly, your Documents/secret.txt file is _replaced_. If one of the files is an executable or a script you run, that could execute attacker code—game over.
Here’s the kind of code that’s bad—it doesn’t check if the path is safe
// Pseudocode of a ZIP extraction routine with path traversal risk
for (ZipEntry entry : zipFile.entries()) {
File outFile = new File(destinationDir, entry.getName());
try (OutputStream os = new FileOutputStream(outFile)) {
copyStreams(zipFile.getInputStream(entry), os);
}
}
If entry.getName() is "../../../../filename.txt", then outFile points far above our intended folder!
A safe approach would sanitize entry.getName(), refusing to write files with ../ in their name.
Scenarios
- Your config files or documents are altered/corrupted
Potential for remote code execution (attacker’s code runs in your environment)
User Experience: You’ll usually see errors _after_ the files have already been overwritten—and by then, damage is done.
Limitations: The attacker needs to know or guess the filenames and paths on your computer. However, common file paths (like user folders or app configs) are often the first targets.
Exploit Proof-of-Concept
Here’s a simple way an attacker could craft such an archive (for educational purposes only! DO NOT USE MALICIOUSLY):
# This Python script creates a zip with a directory traversal payload
import zipfile
with zipfile.ZipFile('evil_workflow.zip', 'w') as z:
# The path is relative (travels up directories)
z.writestr('../../../../Documents/secret.txt', 'overwrite your documents!')
z.writestr('workflow.knime', '...KNIME workflow XML...')
Opening this in KNIME would cause contents of "secret.txt" to be replaced with overwrite your documents!.
How to Defend Yourself
- Update KNIME: Always use the latest version. Once a security fix is out, older versions remain vulnerable.
References & Further Reading
- KNIME Security Advisory (Official)
- Snyk Zip Slip Vulnerability Guide
- CVE Database Listing for CVE-2022-44749
Responsible Disclosure & Fixes
KNIME has released advisories and patches for this. If your version is out-of-date, update now. If you discover similar issues in other tools, always disclose them responsibly!
TL;DR:
CVE-2022-44749 lets attackers overwrite files on your computer just by getting you to open a poisoned KNIME workflow. Always use trusted workflows, keep your software patched, and remember: Not all attacks need you to double-click “run.” Sometimes, just “open” is enough.
*Have you checked your KNIME version lately?*
*(This post is original and exclusive. Please share responsibly.)*
Timeline
Published on: 11/24/2022 07:15:00 UTC
Last modified on: 11/30/2022 19:48:00 UTC