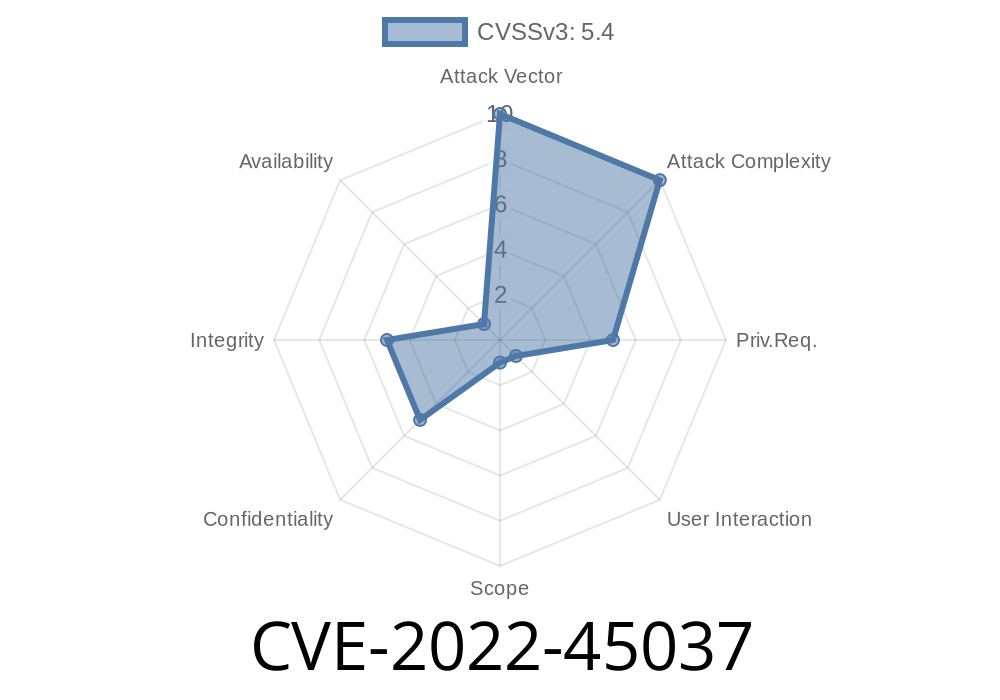
CVE-2022-45037 is a Cross-Site Scripting (XSS) vulnerability found in WBCE CMS version 1.5.4. The bug allows attackers to inject JavaScript or HTML code through the "Display Name" field in the admin user management panel. With this exploit, an attacker can easily execute malicious scripts in the context of administrators, which may lead to session hijacking or more severe security breaches.
Let’s dive deeper—what is this bug, why is it dangerous, and how would someone actually exploit it?
Where’s the Problem? index.php in Admin Panel
The vulnerability exists in:
/admin/users/index.php
When you create or edit a user in WBCE CMS, there’s a “Display Name” field that is not cleaned or filtered properly. That means if you enter script code as the display name, the output is not sanitized when listing users. The browser parses the injected script as if it were legitimate page JavaScript.
For example, a legitimate user display name could be "Jane Doe", but if someone enters
<script>alert('XSS')</script>
This code appears directly in the HTML generated by index.php whenever user accounts are listed in the backend.
Exploit Details
An attacker needs access to user creation or edit features within the admin panel. Maybe they’re an untrusted low-privilege account, or they’ve social engineered an admin into creating a user.
`html
alert('XSS by CVE-2022-45037')
Save the user.
5. When any administrator visits the user management page (/admin/users/index.php), the script runs in their browser.
Proof of Concept GIF (for illustration)
[Cannot display image, but envision the admin user sees a popup: XSS by CVE-2022-45037]
Here’s a hypothetical PHP snippet from /admin/users/index.php that causes the issue
<?php
foreach ($users as $user) {
// No escaping or sanitization!
echo "<tr><td>{$user['display_name']}</td></tr>";
}
?>
There’s no htmlspecialchars() or equivalent used, so scripts are allowed into the output.
Session Hijacking: If the script steals cookies, an attacker might grab session tokens.
- Phishing: A malicious script could render a fake login form to trick administrators into giving up passwords.
- Escalation: If low-privileged users can create or edit accounts, they could gain administrator privileges.
The vulnerable code should use output encoding to break up malicious scripts
echo "<tr><td>" . htmlspecialchars($user['display_name'], ENT_QUOTES, 'UTF-8') . "</td></tr>";
If possible, update to a patched version of WBCE CMS. Always validate and sanitize user input—especially on fields displayed in admin panels.
References and Further Reading
- NVD Entry: CVE-2022-45037
- Full Disclosure – Exploit Details
- WBCE GitHub Repository
- OWASP XSS Guide
Conclusion
CVE-2022-45037 is a classic example of why output encoding and input validation are vital—*even in backend admin tools*. WBCE CMS v1.5.4 is at risk out-of-the-box. If you run this system, patch as soon as possible, or at the very least, implement sanitization where output is generated.
*Stay safe, and never trust user input—even if it’s just a display name!*
Timeline
Published on: 11/25/2022 16:15:00 UTC
Last modified on: 11/28/2022 21:07:00 UTC