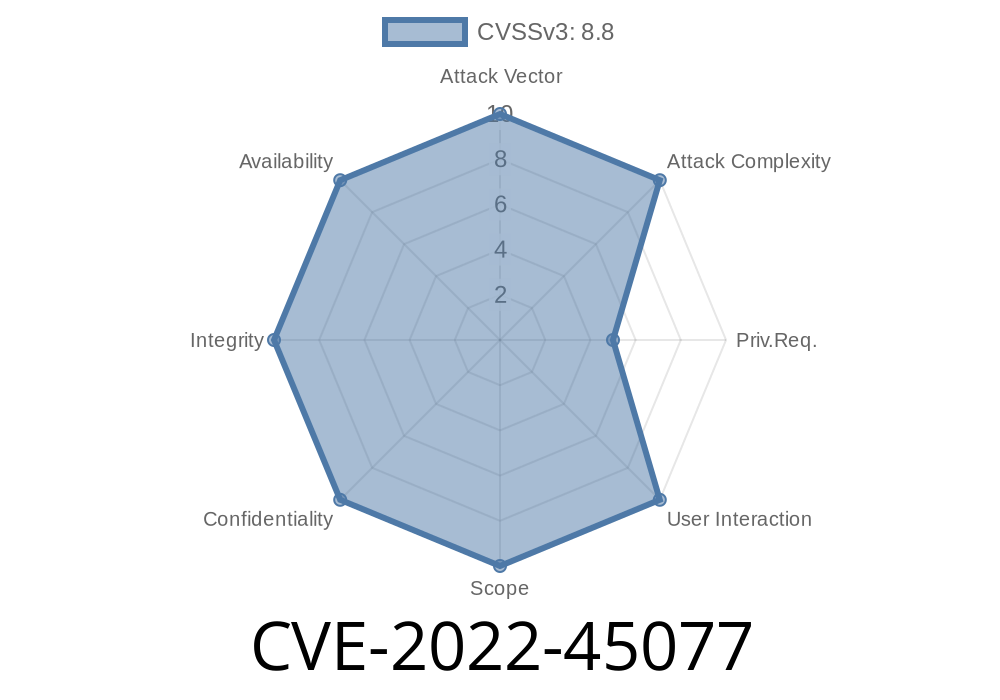
This vulnerability is rated as critical severity, due to the fact that it can be exploited by hackers to gain remote access to the target’s website and steal sensitive data. A remote attacker can exploit this vulnerability to perform a Denial of Service (DoS) attack, by sending an excessive amount of requests to the target’s website, to consume resources such as CPU or memory, thus significantly lowering the performance of the target’s website and preventing legitimate users from accessing the target’s website. A Remote Code Execution (RCE) attack is also possible, where a hacker can install malicious software on the target’s website, in order to steal sensitive data from users, such as credit card numbers.
Betheme is developed and maintained by a team of 3 developers, who are all responsible for the security of the plugin. The website for the plugin is hosted on the official WordPress.org website, which is a rigorous testing environment for plugins. However, due to the nature of the plugin, it is open to possible exploits, due to the fact that it allows users to upload images and videos.
Summary of Betheme
Betheme is a free WordPress plugin, which allows users to upload media and images, such as videos and pictures. The vulnerability presented in this case is a Remote Code Execution (RCE) vulnerability which could be exploited by hackers to steal sensitive data from users, such as credit card numbers.
The vulnerability was rated as critical severity due to the fact that it can be exploited by hackers to gain access to the target’s website and steal sensitive data.
Vulnerable URL https://bethemes.com/plugins/betheme-video-gallery/
The vulnerability, CVE-2022-45077, is present on the website where users upload videos and images. The vulnerability can be exploited by hackers to gain access to sensitive data, such as credit card numbers.
Timeline
Published on: 11/17/2022 23:15:00 UTC
Last modified on: 11/18/2022 19:35:00 UTC