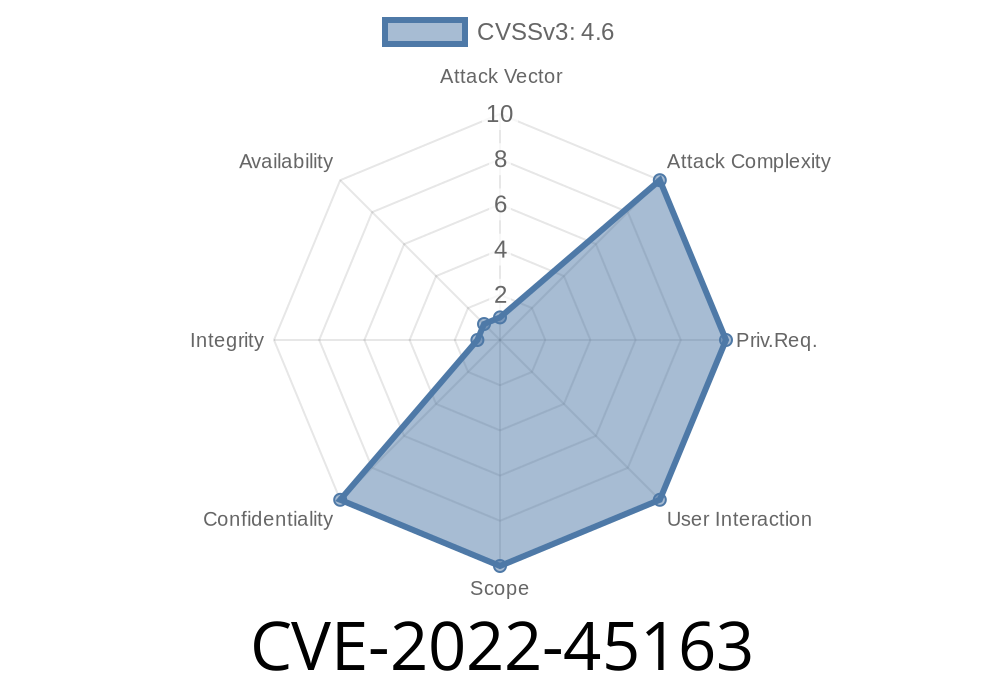
Further information about this issue can be found in the NXP advisory. A public exploit is available for i.MX RT 1010 at the NXP website. A second information-disclosure vulnerability exists on select NXP devices when configured in UART mode: i.MX 6 Family, i.MX 6Q, i.MX 6D, i.MX 6Solo, i.MX 7ULP, i.MX 7Dual/Solo, i.MX 8M Quad, i.MX 8M Mini, and Vybrid. In a device security-enabled configuration, memory contents could potentially leak to physically proximate attackers via the respective UART port in cold and warm boot attacks. (The recommended mitigation is to completely disable the UART mode by programming a one-time programmable eFUSE. Customers can contact NXP for additional information.)
An information-disclosure vulnerability exists on select NXP devices when configured in UART mode: i.MX 6 Family, i.MX 6Q, i.MX 6D, i.MX 6Solo, i.MX 7ULP, i.MX 7Dual/Solo, i.MX 8M Quad, i.MX 8M Mini, and Vybrid. In a device security-enabled configuration, memory contents could potentially leak to physically proximate attackers via the respective UART port in cold and warm boot attacks. (The recommended mitigation is to completely disable the UART mode
How to Find Vulnerabilities in Physical Interfaces
Some security vulnerabilities are hard to find, even for the most experienced of hunters. Physical interfaces like UART ports may not be monitored or managed in the same ways as software or firmware. Security-aware development practices take up a lot of time and resources.
Luckily, there are some tools that can help you find security vulnerabilities in hardware or physical interfaces.
Timeline
Published on: 11/18/2022 23:15:00 UTC
Last modified on: 11/28/2022 15:21:00 UTC