Therefore, the only way to exploit this issue is by sending a crafted channel tx. An attacker can do this by sending a malicious smart contract with a channel name that is already in use or by sending a malicious channel contract. An attacker can also do this by sending a malicious channel contract with a channel name that is already in use.
An orderer receiving the same channel tx repeatedly with the same Channel name can crash due to a malformed orderer event with orderer.orderer already consumed. A malicious node can do this by sending a malicious channel contract with a channel name that is already in use or by sending a malicious channel contract with a channel name that is already in use. An orderer receiving the same channel tx with the same Channel name can crash due to a malformed orderer event with orderer.orderer already consumed. A malicious node can do this by sending a malicious channel contract with a channel name that is already in use or by sending a malicious channel contract with a channel name that is already in use.
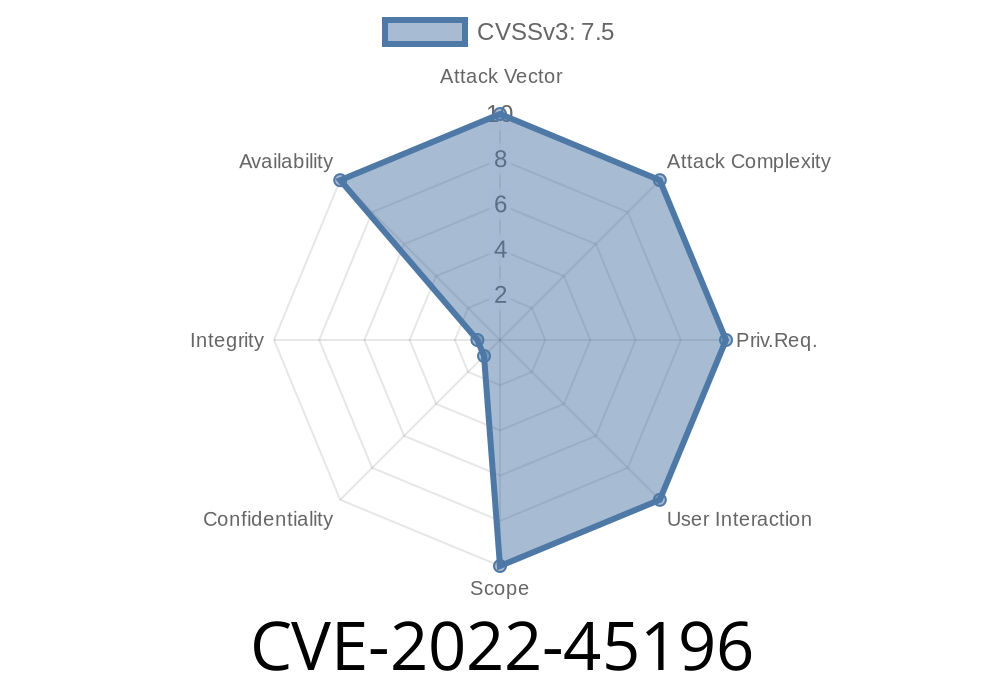
CVE References: CVE-2018-8174 An orderer receiving the same channel tx repeatedly with the same Channel name can crash due to a malformed orderer event with orderer.orderer already consumed. A malicious node can do this by sending a malicious channel contract with a channel name that is already in use or by sending a malicious channel contract with a channel name that is already in use.
CVE References: CVE-2018
Channels
In order to exploit this issue, the attacker must be able to send a malicious channel contract with a channel name that is already in use or by sending a malicious channel contract with a channel name that is already in use.
Potential Impact
An orderer receiving the same channel tx repeatedly with the same Channel name can crash due to a malformed orderer event with orderer.orderer already consumed. A malicious node can do this by sending a malicious channel contract with a channel name that is already in use or by sending a malicious channel contract with a channel name that is already in use. An orderer receiving the same channel tx with the same Channel name can crash due to a malformed orderer event with orderer.orderer already consumed. A malicious node can do this by sending a malicious channel contract with a channel name that is already in use or by sending a malicious channel contract with a channel name that is already in use.
^
The only way to exploit this issue is by sending a crafted channel tx. An attacker can do this by sending a malicious smart contract with a channel name that is already in use or by sending a malicious channel contract. An attacker can also do this by sending a malicious channel contract with a channel name that is already in use.
Timeline
Published on: 11/12/2022 20:15:00 UTC
Last modified on: 11/17/2022 17:22:00 UTC