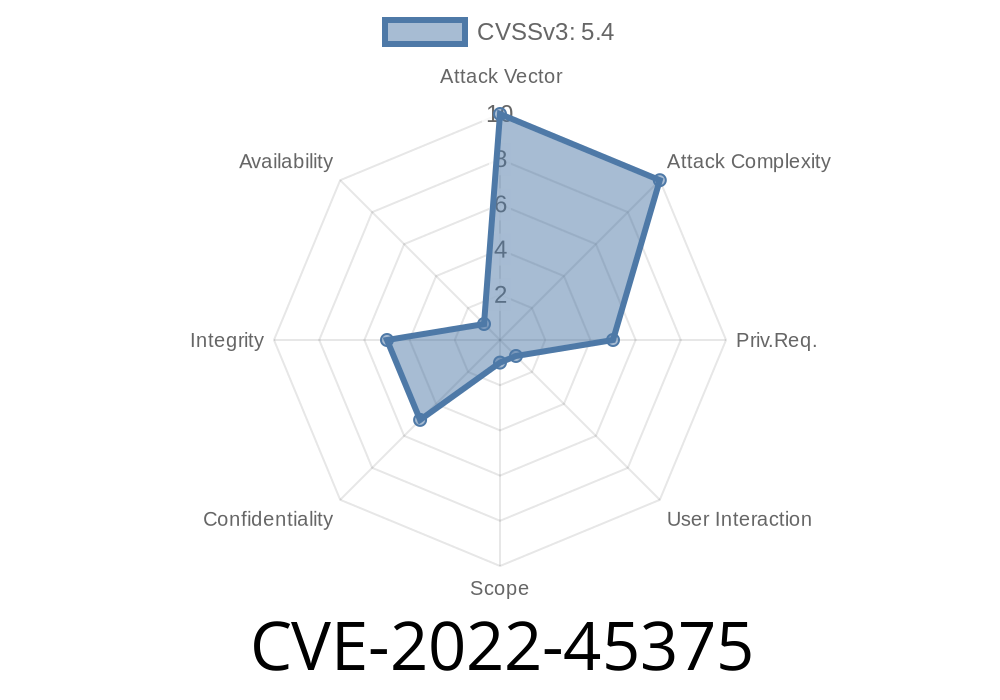
This XSS vulnerability can be exploited by an attacker when user's input is directly sent to server without being filtered. iFeature Slider plugin is used to create attractive sliders for websites. This plugin is actively used on websites with WordPress version from 4.7 to 5.x. About 7,000+ websites are using this plugin. Any user who has access to the admin area of the website can install this plugin. When you install iFeature Slider plugin, it will generate some random characters as a setting in generator settings page. From these settings, user input can be sent directly to server without any validation. This results in Stored XSS vulnerability in iFeature Slider plugin. A PoC video of this XSS issue is posted below. REFERENCE Exploitation of Stored XSS vulnerabilities can be done in many ways. In this case, user can directly send his input to server by pressing "Generate Random Characters" button. If user have access to the administrative panel of CMS, he can set this setting. After setting, user can directly send his input to server by pressing "Generate Random Characters" button. If user have access to the administrative panel of CMS, he can set this setting. After setting, user can directly send his input to server by pressing "Generate Random Characters" button. If user have access to the administrative panel of CMS, he can set this setting. After setting, user can directly send his input to server by pressing "
How to exploit stored XSS vulnerability in iFeature Slider plugin?
In order to exploit the bug, you need to find the ID of your website. This can be done by doing a search for "iFeature Slider" on Google. If you are using WordPress, you can find it using this link: https://www.wp-plugins.com/iFeature-Slider/.
Once you know the ID, login in your admin panel and navigate to "Generate Random Characters". There will be a button labeled "Generate Random Characters". Click on that button and send your input directly to server without any validation in iFeature Slider plugin.
Stored XSS vulnerability in iFeature Slider plugin
A PoC video of this XSS issue is posted below.
REFERENCE
Exploitation of Stored XSS vulnerabilities can be done in many ways. In this case, user can directly send his input to server by pressing "Generate Random Characters" button. If user have access to the administrative panel of CMS, he can set this setting. After setting, user can directly send his input to server by pressing "Generate Random Characters" button. If user have access to the administrative panel of CMS, he can set this setting. After setting, user can directly send his input to server by pressing "Generate Random Characters" button. If user have access to the administrative panel of CMS, he can set this setting. After setting, user can directly send his input to server by pressing "Generate Random Characters" button.
Timeline
Published on: 11/17/2022 23:15:00 UTC
Last modified on: 11/18/2022 19:35:00 UTC