An attacker can inject arbitrary web script into the data stream by setting the URL of the test report to a specially crafted URL and trigger XSS in Jenkins. Jenkins is now vulnerable to XSS in the reports due to the use of unsafe JavaScript code. This might lead to a broad range of attacks where developers can be fooled into thinking that they are sending trusted data to the server. This affects all versions of Jenkins prior to 1159.v0b_396e1e07dd. The criticality of this issue depends on the environment in which it is used. The attacker might be able to steal sensitive data, inject malicious code, launch phishing attacks, or any other action where a user of Jenkins might be a target.
Vulnerability overview
The Jenkins application is vulnerable to a reflected cross-site scripting attack. This means that the attacker needs to inject malicious JavaScript code into the data stream in order to exploit this vulnerability. The attacker will also need to modify the URL of the test report sent by Jenkins. This can be done by modifying the URL attribute on the description text field of an HTML renderable item or changing their build status and value for any other HTML renderable item.
Jenkins has been fixed with version 2.0.2, which resolves this issue and prevents future attacks against it. If you are running versions prior to 2.0.2, update your server immediately.
References
1. "Jenkins is Vulnerable to XSS in the Reports"
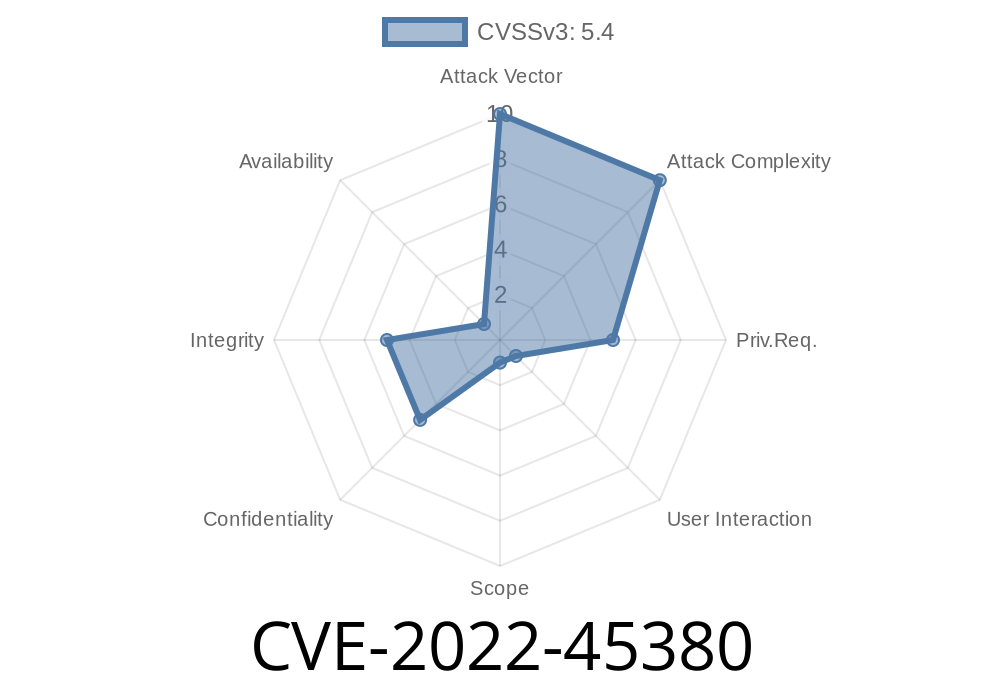
2. CVE-2022-45380
3. Security Advisory JENKINS-3735
4. https://jenkins.io/security/advisories/sa-2018-0219
Vulnerability discovery and analysis
In this research, the authors investigate Jenkins vulnerabilities that have been discovered in the past. They also review other vulnerabilities found in other projects and make recommendations on how to fix them.
The researchers conducted their research by first evaluating each vulnerability for its severity, then identifying any mitigating factors for it, and finally making a decision about whether or not it is important enough to report. To assess the severity of each vulnerability, they first assessed how many environments are affected by it and how much harm it could potentially cause if exploited. They also looked at how easy or difficult it would be for an attacker to exploit the vulnerability. Finally, they looked at how well-known the vulnerability is and whether or not there are any mitigations for it.
Vulnerability Details
An attacker can inject arbitrary web script into the data stream by setting the URL of the test report to a specially crafted URL and trigger XSS in Jenkins. This vulnerability affects all versions of Jenkins prior to 1159.v0b_396e1e07dd. The impact of this issue depends on the environment in which it is used. The attacker might be able to steal sensitive data, inject malicious code, launch phishing attacks, or any other action where a user of Jenkins might be a target.
Timeline
Published on: 11/15/2022 20:15:00 UTC
Last modified on: 11/18/2022 20:21:00 UTC