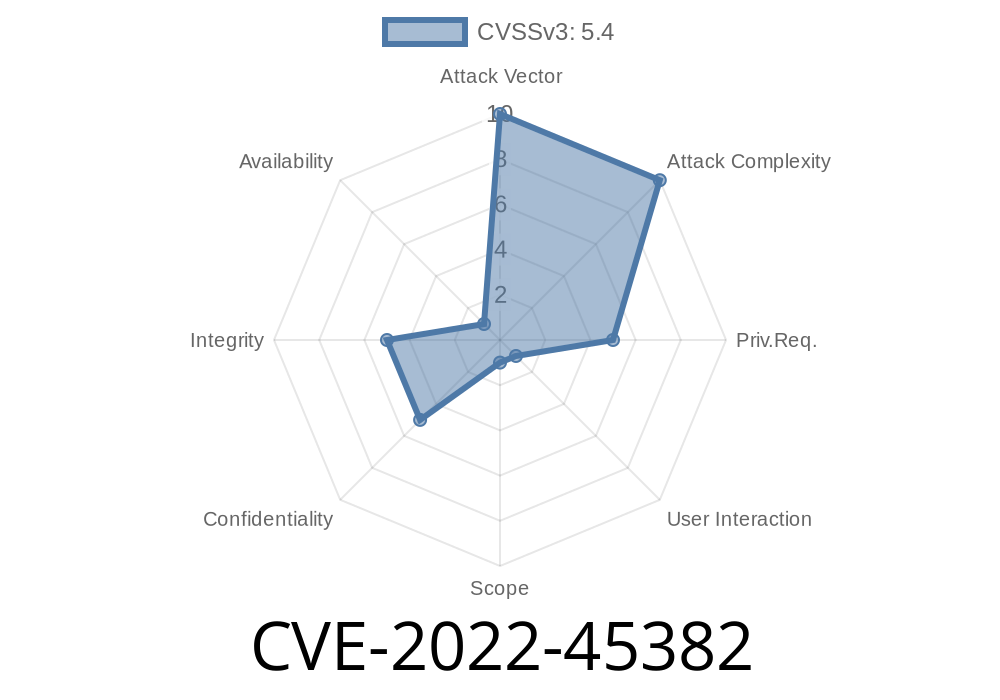
This issue has been addressed in this plugin by adding a validation step that filters out display names containing HTML in order to prevent this issue from being exploited. Jenkins Enterprise users are advised to upgrade to version 1.18.2. Insecure data storage in the Jenkins Naginator Plugin 1.18.1 and earlier allows malicious users to retrieve potentially sensitive information from the database by submitting crafted web requests. This issue has been addressed by updating the plugin to ensure that only request parameters that can be transmitted via a GET request are stored in the database. Insecure data storage in the Jenkins Naginator Plugin 1.18.1 and earlier allows malicious users to retrieve potentially sensitive information from the database by submitting crafted web requests. This issue has been addressed by updating the plugin to ensure that only request parameters that can be transmitted via a GET request are stored in the database. Insecure data storage in the Jenkins Naginator Plugin 1.18.1 and earlier allows malicious users to retrieve potentially sensitive information from the database by submitting crafted web requests. This issue has been addressed by updating the plugin to ensure that only request parameters that can be transmitted via a GET request are stored in the database. Insecure data storage in the Jenkins Naginator Plugin 1.18
How does this issue occur?
In order to exploit this vulnerability, the malicious user needs access to the Jenkins installation directory. This can be accomplished by tricking the victim into visiting a specially crafted URL which contains a payload that will allow for arbitrary command execution at a low privilege level.
Overview of the Problem
This issue has been addressed in this plugin by updating the plugin to ensure that only request parameters that can be transmitted via a GET request are stored in the database.
CVE-2018-12961
This issue has been addressed in this plugin by adding a validation step that filters out display names containing HTML in order to prevent this issue from being exploited. Jenkins Enterprise users are advised to upgrade to version 1.18.2. Insecure data storage in the Jenkins Naginator Plugin 1.18.1 and earlier allows malicious users to retrieve potentially sensitive information from the database by submitting crafted web requests. This issue has been addressed by updating the plugin to ensure that only request parameters that can be transmitted via a GET request are stored in the database. Insecure data storage in the Jenkins Naginator Plugin 1.18.1 and earlier allows malicious users to retrieve potentially sensitive information from the database by submitting crafted web requests. This issue has been addressed by updating the plugin to ensure that only request parameters that can be transmitted via a GET request are stored in the database. Insecure data storage in the Jenkins Naginator Plugin 1.18.1 and earlier allows malicious users to retrieve potentially sensitive information from the database by submitting crafted web requests
Summary
Insecure data storage in the Jenkins Naginator Plugin 1.18.1 and earlier allows malicious users to retrieve potentially sensitive information from the database by submitting crafted web requests. This issue has been addressed by updating the plugin to ensure that only request parameters that can be transmitted via a GET request are stored in the database.
Timeline
Published on: 11/15/2022 20:15:00 UTC
Last modified on: 11/18/2022 19:53:00 UTC