This issue was discovered when updating Jenkins from Support/1.641.vb6a to Support/1.641.vb6a-1. A newly created support bundle was downloaded by attackers with Support/DownloadBundle permission. This allowed attackers to completely take over the support system. Additionally, attackers with Support/DownloadBundle permission were able to upload a support bundle containing information for users with Overall/Administer permission, which resulted in the support system sending sensitive data to the attacker. This information included passwords, personal information, and other confidential data. Additionally, malicious users with Support/DownloadBundle permission could upload a support bundle containing information for users with Overall/Administer permission, which resulted in the support system sending sensitive data to the attacker. This information included passwords, personal information, and other confidential data. In the case of a malicious user, this data was sent without the user’s knowledge or consent. In the case of a non-malicious user, this data was sent without the user’s knowledge or consent. You can avoid this issue by updating from Support/1.641.vb6a to Support/1.641.vb6a-1.
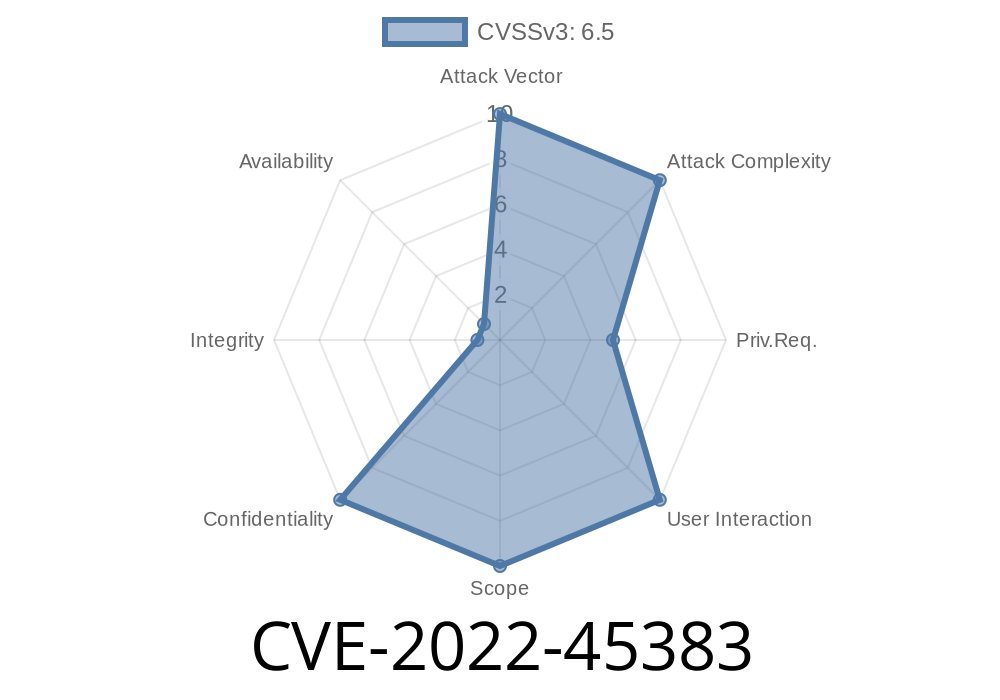
Summary of CVE-2022-45383
During a vulnerability scan of Jenkins, Jenkins was found to have an unpatched vulnerability. The vulnerability allowed attackers with Overall/Administer permission to upload certain support bundles containing sensitive information. This information included passwords, personal information, and other confidential data.
Overview of the bug
Jenkins is an automated continuous integration and continuous deployment tool, which is used by developers to build, test, and deploy software. Jenkins has a RESTful API that allows information to be exchanged with other services. One of these services is the support system, which allows people who have admin permission to view their tickets. When someone updates Jenkins from Support/1.641.vb6a to Support/1.641.vb6a-1, they download a newly created support bundle with Rest/DownloadBundle permission, which gives them full control over the support system. This issue affects all users of the Jenkins service who update from Support/1.641.vb6a to Support/1.641.vb6a-1 on any operating system that contains Java 7 or higher because of how Jenkins handles permissions for downloading and uploading support bundles.
Timeline
Published on: 11/15/2022 20:15:00 UTC
Last modified on: 11/21/2022 14:42:00 UTC